Apple fixed a recently unearthed lock screen bypass with the release of iOS 15.0.1, but failed to publicly recognize the weakness or the person who discovered it.
In September, researcher Jose Rodriguez detailed an iOS vulnerability that enables attackers to bypass a secured iPhone lock screen and access notes through a combination of VoiceOver and common sharing tools.
Rodriguez published a proof of concept on his YouTube channel on Sept. 20, illustrating methods by which a user's notes can be copied and sent to another device. The researcher did not disclose the vulnerability to Apple prior to going public, saying at the time that he was "giving away" the exploit in hopes of shedding light on problems related to the tech giant's Bug Bounty Program.
As noted by Rodriguez in a Twitter post on Friday, Apple's iOS 15.0.1 release contains a fix for the lock screen bypass. Accompanying release notes show that Apple did not assign a CVE designation or provide credit to the researcher for discovering the flaw. The company pulled a similar move last month when it quietly fixed a macOS Finder bug.
A report last week saw researchers criticize Apple's Bug Bounty Program for a general lack of communication and issues with payouts for discovered vulnerabilities. Those sentiments were recently echoed by security researchers Denis Tokarev, Bobby Rauch and Rodriguez, all of whom discovered and reported bugs to Apple.
The tech giant's head of security engineering, Ivan Krstic, in an interview last month called the program a "runaway success," adding that Apple is gathering feedback as it continues to "scale and improve" the initiative. Apple works hard to address mistakes and "learn from them to rapidly improve the program," he said at the time.
Recent reports indicate that Apple hired a new team lead to reform the Bug Bounty Program.
 AppleInsider Staff
AppleInsider Staff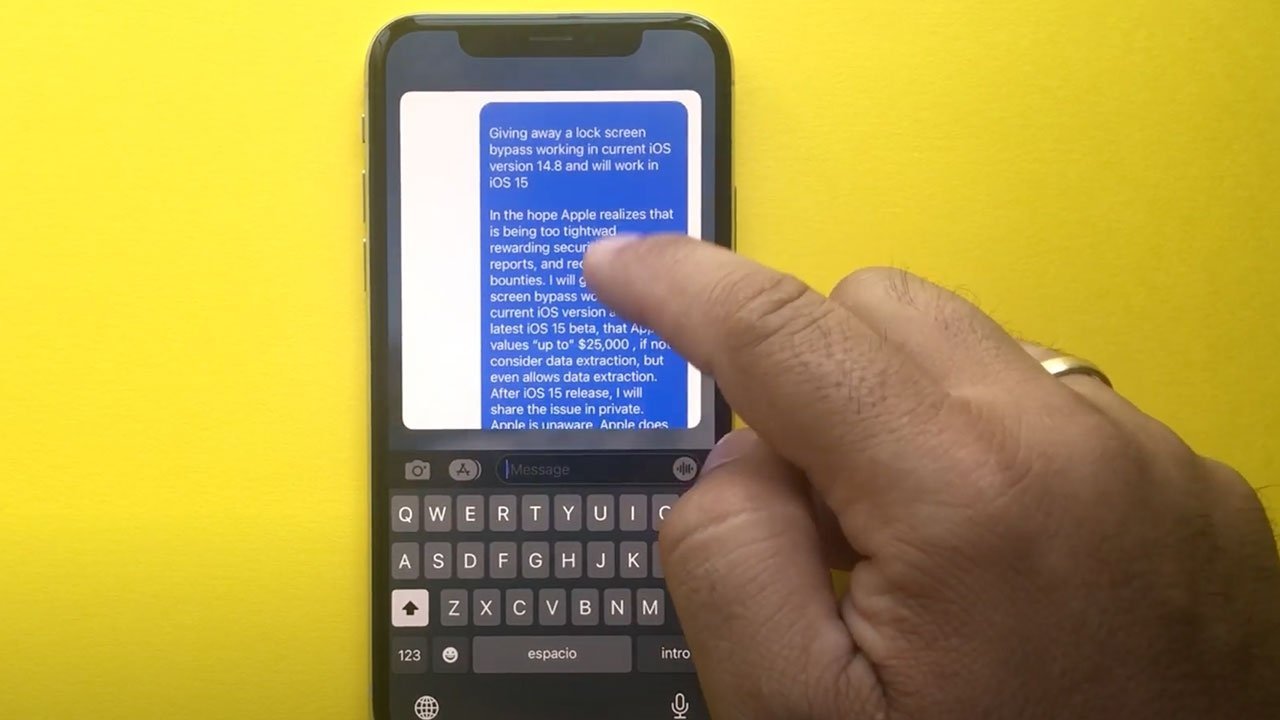








 Marko Zivkovic
Marko Zivkovic
 Christine McKee
Christine McKee
 Andrew Orr
Andrew Orr
 Andrew O'Hara
Andrew O'Hara
 William Gallagher
William Gallagher

 Mike Wuerthele
Mike Wuerthele
 Bon Adamson
Bon Adamson



-m.jpg)



12 Comments
Well that confirms at least one of the problems with Apple's bug bounty program: Apple Sherlocked an exploit. Whowouldathunkit?
The sky really is falling.
My reading of this: he tried to report, but was not the first and therefore could not claim the bounty. Not every "researcher" is running their own YouTube channel. Most will be working for companies which do not allow their staff to run to the media to claim publicity.
Even if he was the first to discover, the problem for Rodriguez was that the moment he placed it on Youtube, he lost any IP rights. The video itself is copyrighted but the knowledge inside is now made public. Everyone can use it without needing to credit and this includes Apple.
I mean these kinds of bugs are embarrassing. Not surprising that Apple or any other company doesn’t want to draw attention to them.
Also, if this one wasn’t reported thorough the proper channels, why would anyone expect to be given credit anyways?