Security researchers found that most apps associated with Apple services on iOS 16 will send data that bypasses a selected VPN connection.
In March 2020, ProtonVPN found a bug in iOS 13.3.1 and later that could prevent a VPN from fully encrypting traffic. It exposed data and IP addresses by failing to terminate existing network connections once a user activated a VPN.
Then, in August 2022, security researcher Michael Horowitz found that the flaw still existed within iOS.
"It takes so little time and effort to re-create this, and the problem is so consistent, that if [Apple] tried at all, they should have been able to re-create it," he wrote at the time. "None of my business. Maybe they are hoping, that like ProtonVPN, I will just move on and drop it. Dunno."
Recently, a different security researcher looked into the issue and found similar results as Horowitz.
On October 11, Tommy Mysk shared results from his own tests using ProtonVPN and Wireshark, a tool that can intercept and analyze network traffic. He found that DNS requests from some Apple apps on iOS 16 ignore the VPN when communicating back to Apple servers.
We confirm that iOS 16 does communicate with Apple services outside an active VPN tunnel. Worse, it leaks DNS requests. #Apple services that escape the VPN connection include Health, Maps, Wallet.
— Mysk (@mysk_co) October 12, 2022
We used @ProtonVPN and #Wireshark. Details in the video:#CyberSecurity #Privacy pic.twitter.com/ReUmfa67ln
Apple apps that leaked data were Apple Store, Clips, Files, Find My, Health, Maps, Settings, and Wallet. Most apps, such as Health, are responsible for handling private user information.
Mysk found that Android apps behave the same way when handling Google services.
"I know what you're asking yourself and the answer is YES. Android communicates with Google services outside an active VPN connection," he wrote, "even with the options "Always-on" and "Block Connections without VPN. I used a Pixel phone running Android 13."
Some apps, such as Health, use end-to-end encryption to connect to Apple servers. Others use encryption in transit and at rest.
Apple's iCloud encrypts the data as it's being sent to one of its servers, then stores it in an encrypted format along with the encryption keys. End-to-end encryption means that only a user's device can encrypt and decrypt their information, and Apple can't access it.
Whether an attacker could snoop on the non-VPN traffic from these apps to gain insight into the data or user isn't clear. However, given that this issue, and the same behavior on Android as it pertains to Google's services has persisted for several years, it is likely intended behavior for a reason known only to Apple and Google.
How to avoid the VPN issue
The only way to be sure that Apple and Google calls do not "leak" out of the VPN connection, is to use a VPN on a Wi-Fi router. There does not appear to be a way on-device to force the issue. You can compare the latest offers on services that can be used with compatible routers in our VPN deals roundup.
 Andrew Orr
Andrew Orr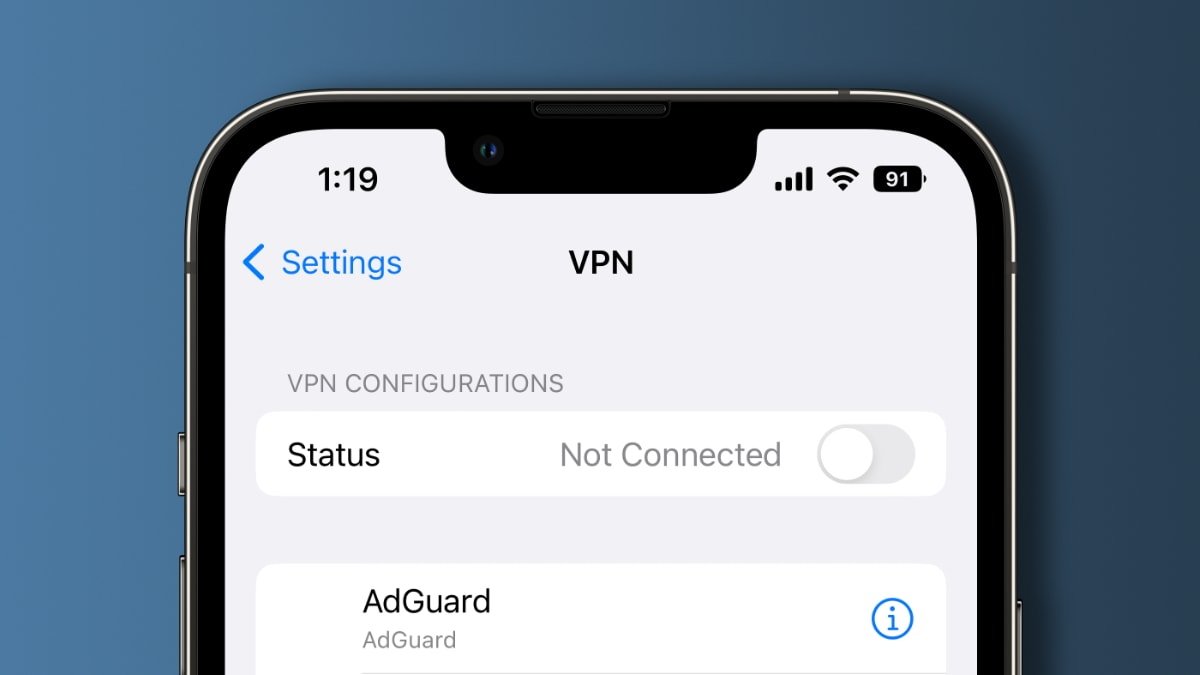







-m.jpg)






 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher
 Chip Loder
Chip Loder
 Brian Patterson
Brian Patterson
 Christine McKee
Christine McKee
 Wesley Hilliard
Wesley Hilliard
 Amber Neely
Amber Neely
-m.jpg)






12 Comments
Interesting article. At some point I would suspect both Apple and Google will have to explain the reasoning.
At least on a Pixel phone using Fi as the carrier with their Virtual Carrier Network I believe that issue has been addressed and mitigated, but not 100% certain. I'll definitely be looking.
It's the "agreement" with the government for a "Back Door".