Researchers found a security flaw in an older version of the Wemo Mini Smart Plug that involved changing its name — and Belkin isn't going to fix it.
The Wemo Mini Smart Plug is designed to offer convenient remote control over lights and basic appliances, such as fan lamps, through a mobile app. The application utilizes Wi-Fi for communication and seamlessly integrates with HomeKit and other smart home ecosystems.
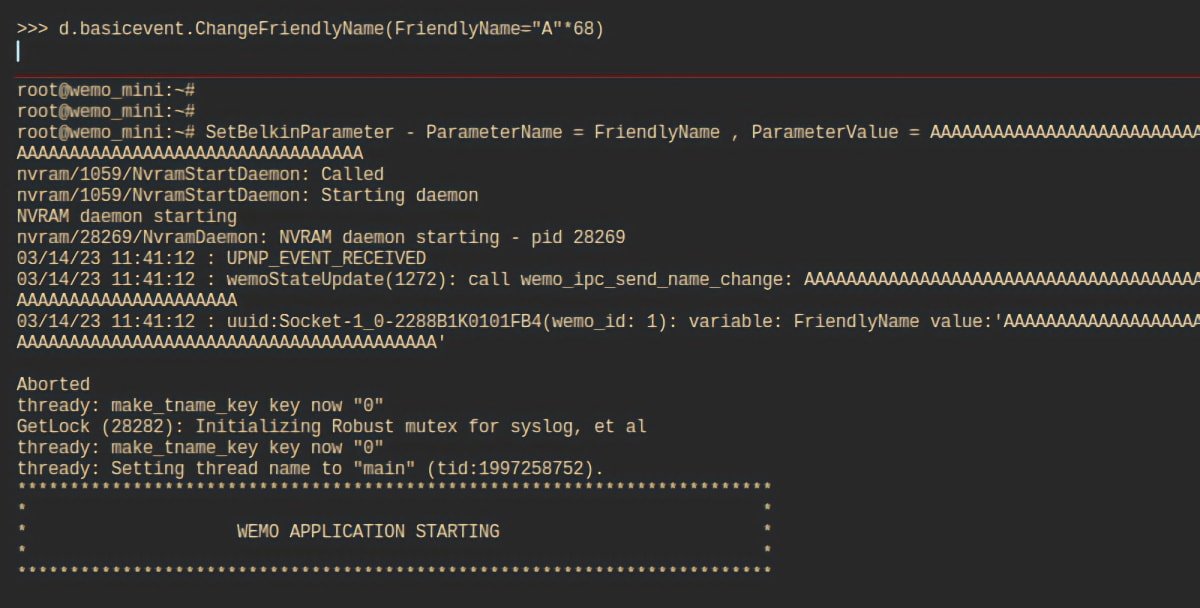
Among other functions, the app lets people change the device name. The length is limited to 30 characters or less, but only the app enforces that rule.
However, through reverse engineering, the security experts at Sternum discovered a method to circumvent the character limit, thereby triggering a buffer overflow. They subsequently named this vulnerability "FriendlyName."
A buffer overflow happens when there's too much information put into a storage area (buffer) that it can't handle. It's like pouring more water into a cup than it can hold, causing it to overflow.
That can lead to unexpected results in computer systems because the extra information can overwrite or change nearby data. Hackers can use a buffer overflow to gain unauthorized access or cause malfunctions in a computer program.
The researchers from Sternum examined the smart plug's firmware and used it to change the device's name to one that was longer than the app's rule of 30 characters. The resulting overflow allowed them to issue commands to the device and control it.
In the hands of a malicious hacker, that could lead to data theft or possibly controlling other devices plugged into the Wemo device.
The team contacted Belkin to inform the company of the security flaw. However, Belkin said it wouldn't fix the vulnerability because the Wemo Smart Plug V2 is at the end of its life.
The current Wemo Smart Plug is version 4.
How to protect yourself from "Friendlyname"
Sternum says people who own one of these plugs shouldn't connect them to the internet. They also shouldn't be allowed to connect to sensitive devices on a home network.
Considering the lack of future updates for version 2 of the Wemo device, there is also the option to explore newer smart plug alternatives if they desire ongoing support and enhancements.
 Andrew Orr
Andrew Orr







-m.jpg)






 Charles Martin
Charles Martin
 Christine McKee
Christine McKee
 Wesley Hilliard
Wesley Hilliard
 Malcolm Owen
Malcolm Owen

 William Gallagher
William Gallagher
 Sponsored Content
Sponsored Content








17 Comments
Absolutely inexcusable to not fix this. There are enough of these plugs functioning perfectly fine to consider these a “dead product” for a security flaw fix.
So WEMO just expects people to upgrade smart devices every couple of years? As they just stop all support? Well, I guess I was ahead of the curve and pulled all my WEMO smart plugs. I moved over to Meross. I have 5 WEMO plugs just sitting around not being used. I do know who to avoid.
Don’t you have to be on the WiFi network to do this and then don’t you already have a much bigger problem?
A perfect example of why Apple needs to get back into routers. (new AirPort Express mesh routers for the new generation).