Apple users are becoming the target of a new wave of phishing attacks called "MFA Bombing" that relies on user impatience, and a bug in Apple's password reset mechanism.
Phishing attacks often rely on users supplying information to an attacker or allowing them to do something to their account, often via an email, text message, or other messaging means. A recently discovered phishing attack has used a new route to make victims fall for it, by using Apple's password reset system.
Dubbed "MFA Bombing," "MFA Fatigue," or "Push Bombing," the attack detailed by Krebs on Security is an elaborate phishing attack that appears to revolve around a bug in the password reset feature. Victims are inundated by "Reset Password" notifications, including the text "Use this iPhone to reset your Apple ID password," and the options to allow or reject the request.
This notification is genuine. It is usually displayed once to the user when they attempt to reset their Apple ID password, as a form of multi-factor authentication on an iPhone, Mac, iPad, or Apple Watch.
The problem with the attack is that the attacker is bombarding the target with so many notifications. It is hoped the user will either accidentally select Allow instead of Don't Allow, or will be annoyed by the deluge of notifications that they will select Allow in order to make it stop.
In this instance, selecting Allow would let the attacker reset the Apple ID password, granting access to the account.
Notifications, then calls
If the sheer number of notifications doesn't work for the attackers, a second phase can occur, if they know the target's phone number.
The victim is called by the attackers, posing as Apple Support, with the calling phone number spoofed to display Apple's actual customer support number. After an unusual number of notifications that may seem like a bug, an unwary victim may believe the caller is genuinely from Apple itself.
Last night, I was targeted for a sophisticated phishing attack on my Apple ID.
— Parth (@parth220_) March 23, 2024
This was a high effort concentrated attempt at me.
Other founders are being targeted by the same group/attack, so I'm sharing what happened for visibility.
Here's how it went down:
Victims are then asked to verify their information, with the attacker using data sources such as websites that offer identity details to "confirm" other account details, all to be more convincing.
Once the victim believes the caller is Apple Support, the attacker can then trigger for an Apple ID reset code to be sent to the victim, in a bid to get them to reveal the one-time password to the "support agent." Again, this allows the attacker to reset the account password and lock the user out.
Not easily avoided
In the case of one Apple user who was hit by the notifications across multiple days and was concerned about how easily they could've granted an attacker access, they contacted the genuine Apple Support about the issues, and was escalated to a senior Apple engineer.
The engineer advised that enabling an Apple Recovery Key would prevent an attacker from using the standard account recovery process. This entailed the generation of a 28-character code that would be used for account recoveries.
However, despite having it enabled on their account, the password reset notifications continued to flow.
Apple did not respond to Krebs' requests for comment about the issue.
It is unknown whether Apple actually knows about the possible notification bug in the password recovery system. However, it has previously dealt with a similar notification issue.
In 2019, an exploit called "AirDoS" allowed an attacker to constantly spam nearby iOS devices with a prompt to share a file via AirDrop. The issue was fixed in iOS 13.3, four months after its discovery, with Apple adding stricter rate limiting to AirDrop requests.
How to protect yourself from MFA Bombing
Apple users facing such an attack have a few opportunities to ward off the attack. But, at this time, the notifications cannot be stopped from coming through.
Victims do have to be vigilant and to select "Don't Allow" every single time it appears.
If the attackers call up pressing for the code, the best practice is to tell them that you will call them back, via the official Apple support number. Apple also will not provide customer information over the phone as a form of verification, which is another indicator that the caller isn't genuine.
Enabling the Apple Recovery Key is a more extreme option that will help ensure the account password reset cannot be performed by an attacker. It does require you to hold onto a lengthy passcode to perform the action for yourself in the future — and as the notification for it says, the code shouldn't be provided to anybody, even on request.
 Malcolm Owen
Malcolm Owen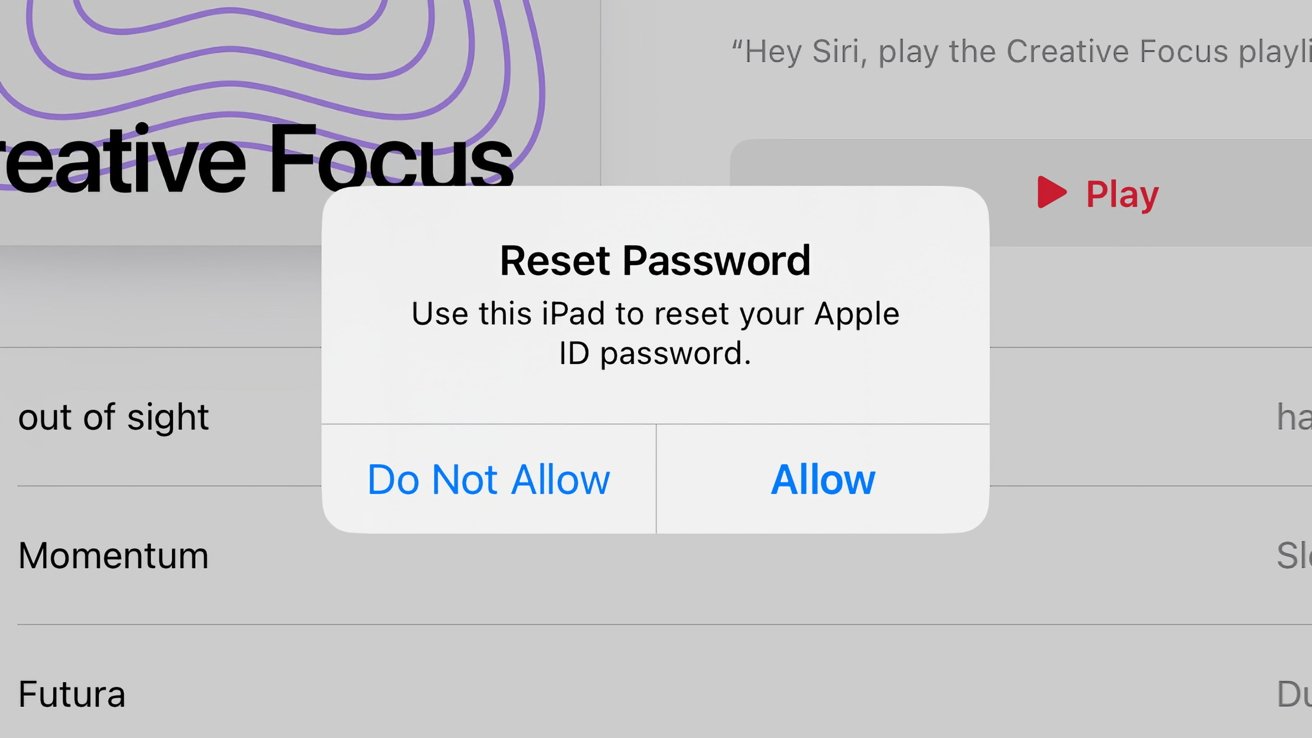







-m.jpg)






 Andrew Orr
Andrew Orr
 Amber Neely
Amber Neely
 Marko Zivkovic
Marko Zivkovic
 William Gallagher and Mike Wuerthele
William Gallagher and Mike Wuerthele


 Mike Wuerthele
Mike Wuerthele








11 Comments
This has happened to me over the last 6 months at least two dozen times. What's worse, those push notifications come through even in Do Not Disturb or Sleep Focus, and pings all devices in a home at once (often late at night.) In addition, authentic "Account Recovery" emails come from Apple's own servers saying your account will be recovered by an unknown phone number! Apple knows this is happening and their suggestion was to change your Apple ID. Not an easy process. Suggestion to Apple: Set a flag in Privacy to disable account recovery from the web, which is the path attackers are using. Here is my tweet from October 2023 about this nefarious situation:
Say I might’ve been attacked like this in 2022 but I haven’t seen anything be changed/charged… i shouldn’t be worried right? I think I still have a photo of it happening
I got the "Apple support" call a few weeks ago after a few password reset requests a day or days earlier (I don't remember for certain). I hung up of course, but some iPhone owners almost certainly fall for it, at least enough to make the scam worthwhile.
Not just Apple of course. Google sent me a notification that someone was claiming ownership of my web domain, and they wanted to confirm the transfer before doing anything. :/
I was targeted with this attack. I suspected it was an attack and supposed that meant my password was breached, so I manually altered it and signed out everything signed into my account, to shut down this attack vector. I don’t know how much data was compromised prior to me resetting my password.
I've got a very simple way of confirming whether the incoming call is legitimate or not. In this case, if it really IS Apple Support calling me about something important and I'm actually tempted to believe it, before I reveal even one small piece of information about myself, I simply hang up, and call the number I REALLY KNOW TO BE APPLE SUPPORT, and ask them if they've been trying to reach me. Simple. No muss. No fuss.