For years, the Mac has been seen as a safer platform than competitors. But, there are still steps you can and should take to keep yourself safe.
So far in 2022, over 34 million samples of new malware have been discovered. But only 2,000 of those samples have targeted macOS, according to AtlasVPN.
Still, Apple has said security in macOS is unacceptable.
Craig Federighi, Apple's chief of software engineering, appeared in court in May 2021 during the Epic Games v. Apple trial. He explained the security features of Apple devices and how the Mac has different security than the iPhone.
Users can download apps from the Mac App Store, a curated storefront where apps are subject to scrutiny from Apple's review team. But software is also available to download from the web, a practice referred to as "sideloading" on the iPhone.
Judge Yvonne Gonzalez Rogers asked Federighi why the Mac supports multiple sources of apps, a capability that Epic Games would like to see on iOS. These third-party sources of apps are "regularly exploited on the Mac," Federighi said, adding that the level of Mac malware is unacceptable.
Federighi used this as an example of why Apple believes iOS is more secure than macOS. "iOS has established a dramatically higher bar for customer protection," adding, "The Mac is not meeting that bar today."
If used safely, the Mac is still "the safest possible" platform, Federighi continued. That statement should get Mac users to think about their security software and how they use their computers.
Layer one: Best security practices
The best ways to prevent a virus infection involves stopping infected emails, routing around infected websites, and downloading software from trusted sources. Basic safety practices combined with a Mac's built-in security features mean that antivirus software isn't needed for most people.
Some of these safety practices are preventative, such as keeping software up to date, and using a DNS service that blocks malicious websites. Others help stop malware that has already been downloaded, such as GateKeeper and XProtect, the antivirus capability that the Mac already has. Finally, some methods go beyond viruses and involve securing online accounts.
Passwords
One way to prevent hackers from stealing online accounts involves using a password manager. Having a different, complex password for each online account drastically reduces the chance of getting hacked.
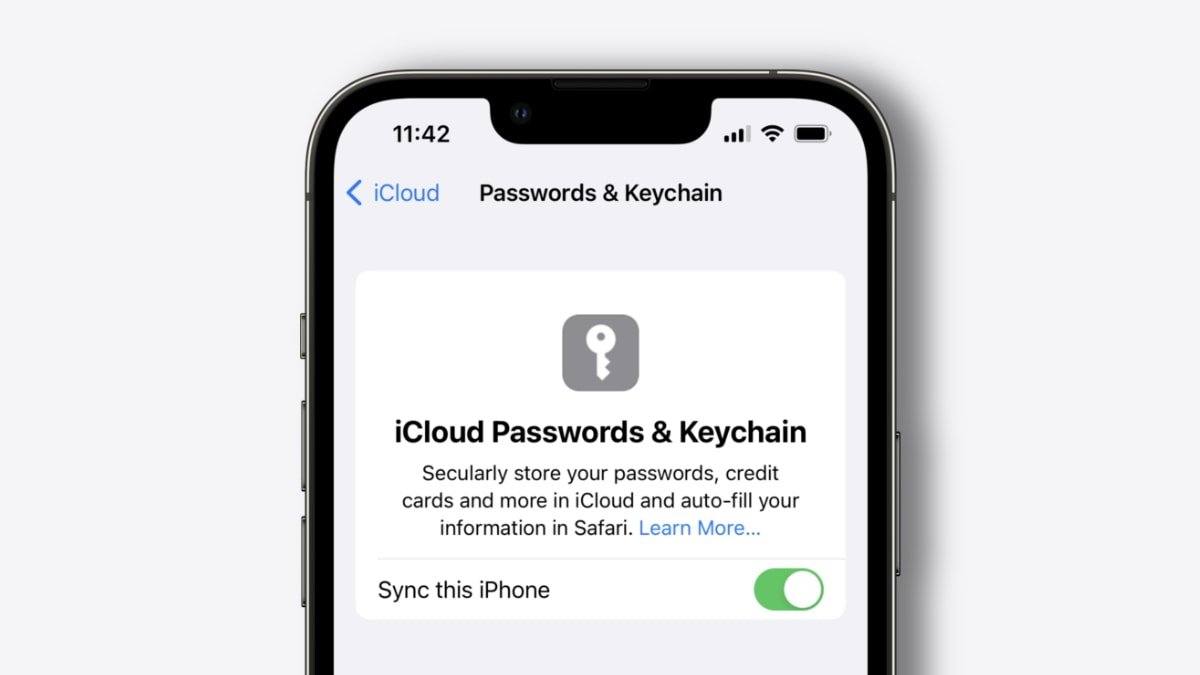
Apple's iCloud Keychain found on Mac, iPhone, and iPad is an easy way to get started. It automatically suggests a password for each new login and auto-fills it the next time a person logs into an account. It can warn a person if their password was found in a data breach and supports two-factor authentication, another layer of account security.
On the iPhone and iPad, users can find iCloud Keychain by going to Settings > Passwords. Users can find it in System Preferences > Passwords on the Mac.
Users can find further password options in Keychain Access, a built-in app in macOS. Keychain Access is the home for logins synced with iCloud Keychain, Wi-Fi logins, system certificates, and even secure notes.
Emails and usernames
In addition to using a different password for each website, a user may use a different email address or a different username. An experimental shortcut creates passwords and usernames, if having a random jumble of letters and numbers is acceptable for a username.
On the email side, Apple users have a built-in option called Hide My Email. Part of the iCloud+ subscription, it automatically creates a different, unique email address for online accounts.
Email sent to one of these addresses is forwarded to a user's Apple ID. They can be deleted anytime and have randomly-generated names such as camper_witting_0r@icloud.com.
Users can find Hide My Email on the iPhone and iPad in Settings > Your Profile Name > iCloud. On the Mac, it can be found in System Preferences > Apple ID.
Phishing
Another way to stay safe using email is to avoid clicking on suspicious links and attachments. An attacker sends these malicious emails in a cybercrime campaign known as phishing. Phishing is when people are contacted through email, phone, or text message in which the sender pretends to be a legitimate institution.
For example, the attacker will create a website posing as a bank and craft an email to get the victim to log into the malicious website. Their username and password will be quickly stolen and used or sold by the attacker.
Standard features of phishing emails include "too good to be true" offers, such as saying the victim won a free iPhone. Or, an email attachment will infect the victim's computer with a virus, in which case antivirus software does come in handy.
When someone receives an email they think is suspicious, they should avoid clicking on any URL inside of it or downloading an attachment. If the email is asking the person to click a button within it, they can instead manually type the website into a browser and look for any alert within their account that matches the email.
Software updates
One of the most critical lines of defense against malware is keeping software up to date. Updates to apps and operating systems often contain fixes for security vulnerabilities found in an older software versions.
Apple is improving this experience with iOS 16, iPadOS 16, macOS Ventura, and other new upgrades coming in fall 2022. A feature called Rapid Security Response decouples security patches from software updates so the OS will protect users faster than ever.
For example, in the iOS 16 developer beta, this feature is found in Settings > General > Software Update > Automatic Updates. A toggle called "Install Security Responses & System Files" says that patches for security bugs and system files will be automatically installed.
The user may need to restart their device to complete the installation, but some system files may be installed automatically even if the toggle is turned off.
These are a few ways that Apple users can stay safe online as the first layer of defense, and the second layer of defense can be found within macOS.
Layer two: Security features built into macOS
After security best practices for browsing the web, Apple's Mac operating system is the second layer. It has native security features that protect users from malicious apps, starting with Gatekeeper.
Gatekeeper ensures that only trusted software runs on a Mac. When a user downloads an app, a plug-in, or software installer package, Gatekeeper verifies that it's from an identified developer using Notarization.
Notarization is a process that requires developers of software outside of the Mac App Store to upload their apps to Apple servers. Apple checks it for malware and sends it back to the developer, who must sign the code with their developer ID. Apple introduced Notarization with macOS Mojave.
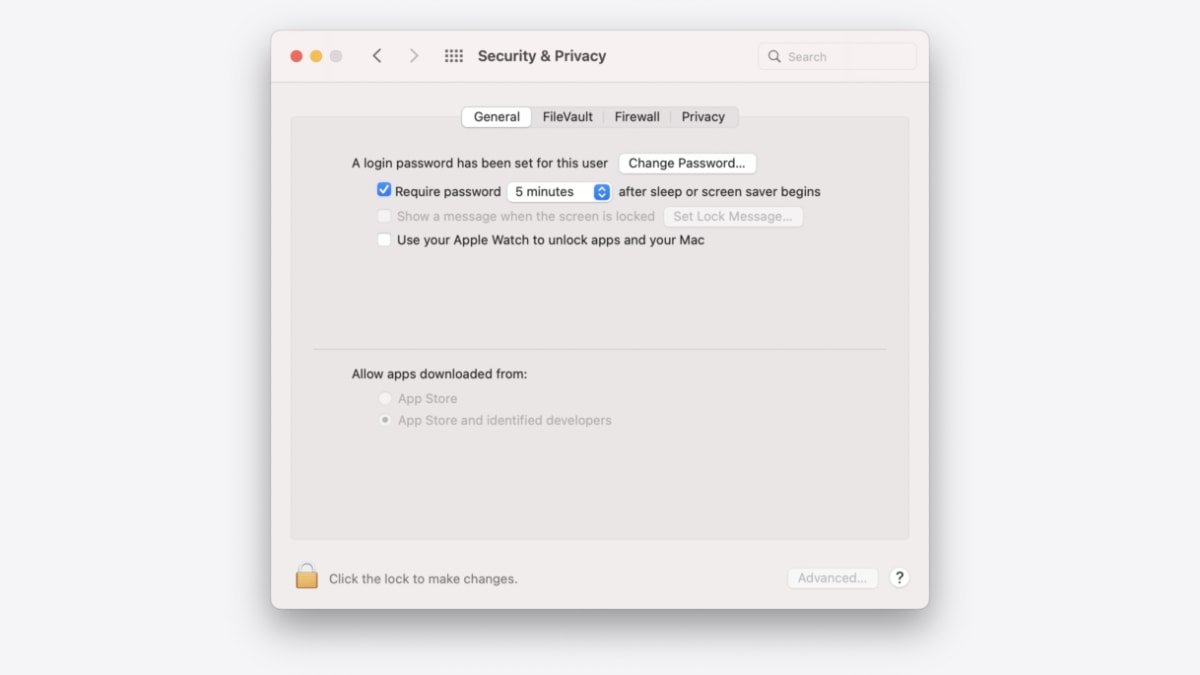
By default, macOS checks all installed software for known malware the first time it's opened. Mac users can change the level of control by going to System Preferences > Security & Privacy. Clicking on the General tab shows two options: "Allow apps downloaded from App Store" and "Allow apps downloaded from App Store and identified developers."
The operating system has further security measures even if Gatekeeper isn't at its strictest setting. The Mac has a little-known feature called XProtect, which acts as antivirus. It was released in 2009 in Mac OS X 10.6 Snow Leopard.
In macOS 10.15 or later, XProtect checks for known malicious content when an app is first launched, when an app changes in the file system, and when Apple updates XProtect signatures. Apple says that these signatures that match known malware are updated automatically, independent of system updates.
When XProtect detects known malware inside downloaded software, the software is blocked, the user is notified, and they have the option to move it to the trash. It also removes malware if the signatures have been updated and periodically checks for new infections.
Mac owners can choose to add a third layer of defense to their systems with third-party security tools. This defense can still include antivirus, but there are more options available.
Layer three: Third-party tools
Tools from Objective See are a popular alternative to antivirus, although they can be used in tandem. They're free, open-source apps that complement the Mac's native security.
One tool, OverSight, helps block malware designed to spy on users through their webcam and microphone. OverSight constantly monitors the system and alerts the user when the internal Mac microphone or the built-in webcam is activated.
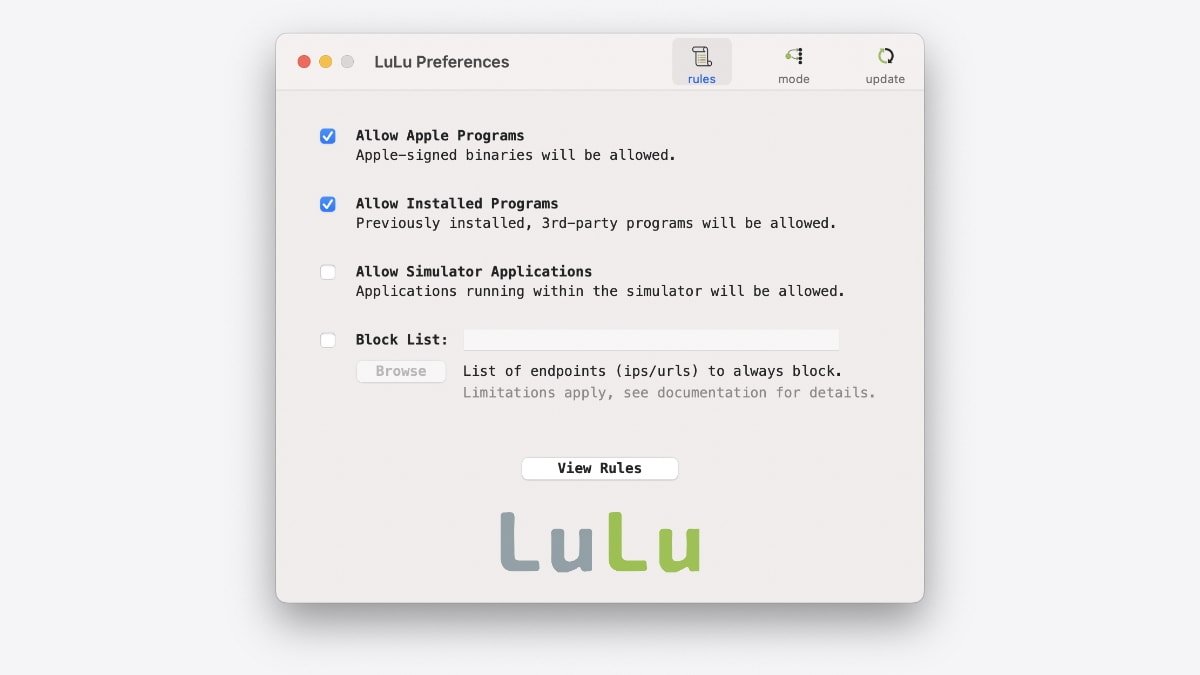
Next, Lulu is a firewall that can block unknown outgoing network connections. It's an excellent option to use, and it works with the Mac's built-in firewall found in System Preferences > Security & Privacy. Finally, Objective See has more tools, such as those that block persistent malware and ransomware.
Another way to stay safe on the web is with DNS. The Domain Name Registry, commonly referred to as the internet phone book connects IP addresses with web domains. A service called NextDNS blocks ads and trackers, offers parental network controls, and much more. In addition, it helps protect against malware by blocking websites that host such content.
These are just some of the security tools available on the web. As a result, Mac owners can take control of their security on all fronts, ensuring their safety even as Apple works to improve security for all its platforms.
 Andrew Orr
Andrew Orr








 Brian Patterson
Brian Patterson
 Charles Martin
Charles Martin


 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher
 Christine McKee
Christine McKee
 Marko Zivkovic
Marko Zivkovic








