Apple on Tuesday reacted to news that the U.S. National Security Agency has worked on iPhone spyware to remotely monitor users, saying it has not cooperated with the agency on such projects and was not previously aware of those attempts.
In an official company statement provided to AllThingsD, Apple vowed to use its resources "to stay ahead of malicious hackers and defend our customers from security attacks, regardless of who's behind them." The statement came after new documents showed the NSA has the capability of deploying software implants on the iPhone to grant access to onboard assets such as text messages, location data, and even microphone audio.
While Apple was previously unaware of the NSA's spyware, the company said it's constantly working to make its products more secure. The iPhone maker said that any reports about potential security issues on its products prompt Apple to "thoroughly investigate and take appropriate steps" in order to protect its customers.
The statement also declared Apple's product security as "industry-leading," and boasted that great effort is placed on making it easy for customers to be able to easily keep their software up to date. To that end, the most recent data from Apple shows that 78 percent of iPhone, iPad and iPod touch users are using iOS 7, the company's latest mobile operating system.
The leaked documents reveal that the NSA's iPhone-targeting spyware program is called "DROPOUTJEEP," and it began in 2008. Capabilities of the software include the interception of SMS text messages, access to onboard data, microphone activation, and approximate positioning via cell tower location.
The NSA boasts a 100 percent success rate in implanting its spyware on iOS devices, but the leaked documents suggest that physical contact with a target phone is required to implant the software.
Apple's full statement in response is included below.
Apple has never worked with the NSA to create a backdoor in any of our products, including iPhone. Additionally, we have been unaware of this alleged NSA program targeting our products. We care deeply about our customers' privacy and security. Our team is continuously working to make our products even more secure, and we make it easy for customers to keep their software up to date with the latest advancements. Whenever we hear about attempts to undermine Apple's industry-leading security, we thoroughly investigate and take appropriate steps to protect our customers. We will continue to use our resources to stay ahead of malicious hackers and defend our customers from security attacks, regardless of who's behind them.
 Neil Hughes
Neil Hughes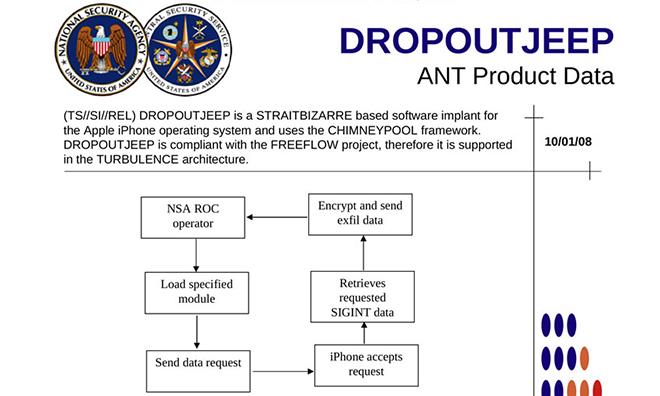














 AppleInsider Staff
AppleInsider Staff
 Chip Loder
Chip Loder
 Christine McKee
Christine McKee
 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher


 Andrew Orr
Andrew Orr





84 Comments
As has been pointed out many times, it's not surprising, not an indication of poor security on the iOS, and not evidence of collusion by Apple that it was, and probably still is, possible to install spyware on an iPhone if one has physical access.
So the NSA created spyware - like a keylogger on a desktop computer - which must be hacked into the iPhone. This means the iPhone has to be jailbroken by the NSA first before installation of the spyware. Luckily, the NSA needs physical contact with the iPhone to do this. It doesn't have a virus that can attach itself to the iPhone.
We know nothing, yeah... It reminds me of our president, he knew nothing as well about NSA spying, no clue about IRS targeting groups, learned about Benghazi from the news...
Man, is the NSA stuff so advanced that none of the industry-leading security advocates can see this stuff at work in the wild? Not even Charlie Miller can sniff out this stuff? It seems he would've encountered some strange process/app/utility running somewhere during one of his scans of iPhones/iPads at work, to the point that it would've aroused his curiosity. But, again, maybe the NSA stuff is so ahead of its time that not even top security researchers can "see" it. Scary.
We know nothing, yeah...
It reminds me of our president, he knew nothing as well about NSA spying, no clue about IRS targeting groups, learned about Benghazi from the news...
I suggest that you take your political rants to AppleOutsider, where they belong.