A patent application published on Thursday reveals an Apple solution that dynamically changes a mobile device's user interface, security levels and other behaviors based on its location, whether it be at the office or in a user's home.
In a filing with the U.S. Patent and Trademark Office titled "Location-sensitive security levels and setting profiles based on detected location," Apple describes a system in which the hardware and software of a mobile device work together to automatically adjust various UI and device behavior settings.
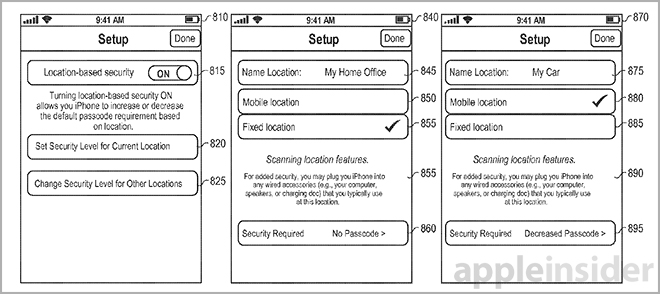
More importantly, the invention delivers a mechanism to adjust iPhone access levels based on its location, meaning different tolerances can be applied based on the relative security of a location. For example, a user may only need a simple four-digit passcode to unlock a device while at home, but authentication via Apple's Touch ID when in public areas like a shopping mall.
Apple notes that any suitable means can be used to determine location — called a "location aspect" — including cellular tower data, recognition of a home Wi-Fi network, GPS data or even proximity to other cellphones, among others. At least two location aspects are required for the system to function with any precision.
A secondary data processing logic, dubbed a "location context" module, determines which settings to apply based on the system's relative confidence in correctly placing device location. Using a predefined scale to measure against, the module defaults to certain settings based on thresholds of confidence.
Once homed in on a specific location, or preset threshold, the system determines whether to apply or modify a specialized user profile or device behavior.
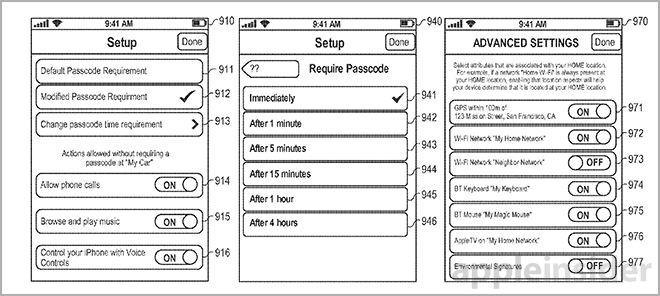
Recognized locations can set low-level security factors, while unrecognized locations may trigger more stringent authentication requirements. Likewise, locations recognized as "unsecure" or public, like mobile Wi-Fi hotspots or geofenced areas not on the trusted list, can also invoke higher strength security factors. Further, public areas may also trigger higher authentication requirements for apps holding sensitive information like Address Book and Calendar.
For example, a user may be required to authenticate via Touch ID when outside of a trusted environment, while a passcode or password will do while at home. Once unlocked, the device may lower security requirements for a preset period of time. If the iPhone leaves the area, or the countdown timer reaches zero, the system resets to an appropriate protection level.
While the most stringent security measures should be used to ensure complete protection, the document points out that location-based methods can enhance user experience without introducing significant vulnerabilities. As mentioned in the filing, users may actually be less apt to employ restrictive — and effective — authentication methods if they find it causes undue burden, which leads to weaker passwords or complete system disablement.
As for customized user profiles, the same location awareness mechanisms described above apply. Instead of modifying security settings, however, the system can change UI behavior and access to device functions based on predefined user preferences. Examples include prominently displaying productivity apps like FaceTime on the home screen when at work, or entertainments apps while at home.
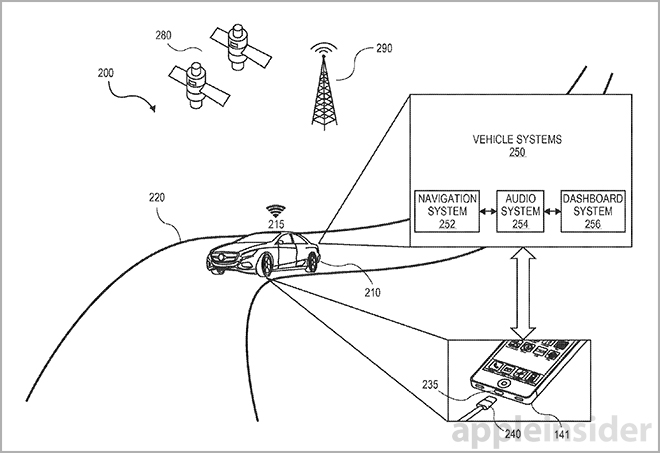
Other examples of device behaviors include a "My Car" setting that allow certain features like dialing 911 and playing music, while disabling others. These settings can be invoked by a variety of triggers including connection to a car's infotainment system.
The remainder of the application focuses on technical minutiae regarding table lookups, alternate embodiments and example system controls including an alert mechanism that notifies the user of current location and operating mode.
Apple's Touch ID has in many ways addressed the perceived issue of employing strong authentication mechanisms without fuss, though some users may still find the feature unnecessary while at home or in a safe location. Adding location awareness to the equation not only streamlines the security process, but also offers a more personalized user experience.
Apple's location-sensitive security patent application was first filed for in 2012 and credits Alexander Reitter, David Amm, Julian Missig and Raymond Walsh as its inventors.
 Mikey Campbell
Mikey Campbell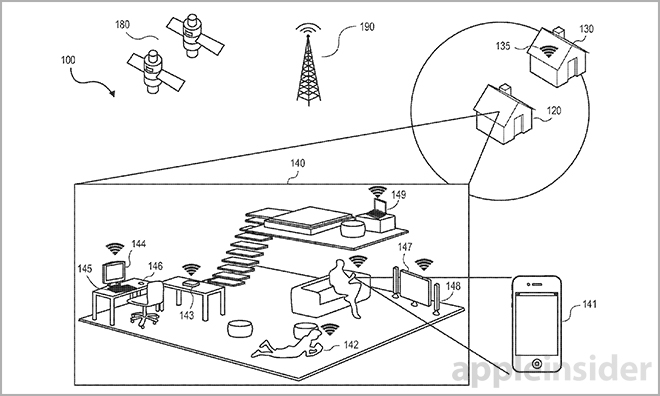





-m.jpg)






 Andrew O'Hara
Andrew O'Hara
 Christine McKee
Christine McKee
 Charles Martin
Charles Martin
 Wesley Hilliard
Wesley Hilliard
 Malcolm Owen
Malcolm Owen

 William Gallagher
William Gallagher








27 Comments
It seems over the next years smartphones actually start to become smart. :)
Tom Tom had something similar on their GPS units a long time ago.
It seems over the next years smartphones actually start to become smart.
No. Machines will never be smart, unless you keep lowering the bar for what qualifies as smart (for humans as well).
The price of freedom is: constant vigilance and the willingness to fight back. So if enough of us keep applying this, machines will remain our servants.
It seems over the next years smartphones actually start to become smart.
they're only as smart as the user.
Tom Tom had something similar on their GPS units a long time ago.
Do explain how what you claim Tom Tom had years ago is anything like this? I've never heard of a GPS with no other functionality having anything like this, or even needing anything like this.