The privacy of Internet users "is not absolute," according to a statement from a five-country coalition that includes the United States following a meeting about security, with the overall theme demanding technology companies to make social networks and messaging services safer and to offer more support to government agencies to break encryption and access potentially sensitive data.
The meeting, which took place from August 28 to August 29 on Australia's Gold Coast, and included representatives from the governments of the United States, United Kingdom, New Zealand, Canada, and Australia. Described as a forum for collaboration between the countries on domestic security issues, this year's meeting focused on cyber security, counter-terrorism, and countering violent extremism.
In a "Statement of Principles on Access to Evidence and Encryption," the group claims they are committed to personal rights and privacy, supporting the role of encryption to protect said rights. At the same time, the "increasing use and sophistication of certain encryption designs" are said to make things difficult for security agencies in combatting serious crimes and threats to national security, with the same encryption systems used to protect citizens also protecting criminals and terrorists.
"Privacy laws must prevent arbitrary or unlawful interference, but privacy is not absolute," the statement reads. "It is an established principle that appropriate government authorities should be able to seek access to otherwise private information when a court or independent authority has authorized such access based on established legal standards. The same principles have long permitted government authorities to search homes, vehicles, and personal effects with valid legal authority."
Calling the increasing gap between the ability for agencies to lawfully acquire the data and the ability to use said data a "pressing international concern" that requires informed debate, the statement goes on to note "Each of the Five Eyes jurisdictions will consider how best to implement the principles" of the statement.
Three principles are offered in the statement, with the first of "Mutual Responsibility" passing some of the responsibility to other stakeholders, including firms involved in telecommunications. Highlighting a "will to work with technology providers" to ensure citizens have access to their data, it goes on to note these firms also need to help assist with the execution of legal orders.
In the majority of cases, major tech companies already provide assistance, with Apple even issuing guidelines in 2014 on how law enforcement and other agencies can request user data. In the case of 2015's San Bernardino attack, the FBI requested data from Apple just three days after the attack, and for some requests, providing data within the same day.
The second principle reaffirms that all assistance that governments request from tech companies is "underpinned by the rule of law and due process protections," in order to maintain democratic societal values.
The last, "Freedom of choice for lawful access solutions," encourages tech companies to "voluntarily establish lawful access solutions to their products and services that they create or operate" in the countries. While governments should not favor a particular technology, the firms providing access should be able to create their own custom solutions tailored to their particular architecture, while still being capable of providing lawful access.
The Freedom of Choice section seems to be a request for companies to produce a "back door" into their products, something that has been central to similar encryption debates over the years. While providing backdoor access would help governments, critics and the companies themselves argue that it would fundamentally weaken encryption for everyone, and wouldn't stop determined criminals from moving on to another more-secure platform or creating their own hard-to-crack encryption scheme.
In a separate statement on "Countering the Illicit Use of Online Spaces," the governmental group discuss the need for online spaces to be safe, and are "gravely concerned" about illegal online content, "particularly the online sexual exploitation of children." Noting that the dark web is not the only source for such content, the group claims social networks and other communications systems are "perpetuating the most abhorrent kinds of child sexual exploitation."
There is also a need to build upon existing efforts to combat terrorist use of online spaces to share radicalization materials, with the group noting that some process has been made to tackle the issue, but it is far from complete. Lastly, the same online spaces are being used to "undermine democratic institutions," an issue that is "delegitimizing the benefits and opportunities that communications and social media platforms create."
The group makes a number of demands for firms in the industry, including the need to develop and implement ways to prevent illegal content from being uploaded at all, and to immediately takedown content that makes it online. For existing content, automated and human systems are needed to "seek out and remove legacy content."
To protect users, the group recommends user safety is built into the design of all online platforms and services. The companies should also set "ambitious industry standards" over such content, and to increase assistance to smaller firms in developing and deploying their own illicit content countermeasures.
The Five Country Ministerial finishes by suggesting "Through the same innovation and cross-sectoral collaboration that has underpinned so many technological advances, the challenge of countering illicit online content is not insurmountable."
 Malcolm Owen
Malcolm Owen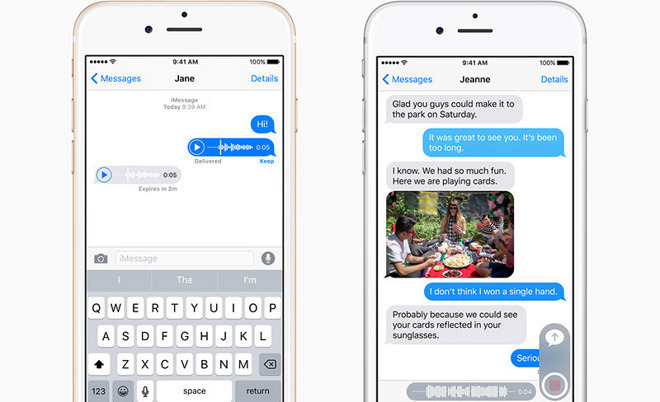

-m.jpg)






 Amber Neely
Amber Neely
 William Gallagher
William Gallagher
 Sponsored Content
Sponsored Content














67 Comments
These people deserve a swift kick in their back door.
Maybe the priority of the “Five Eye jurisdiction” should be to lock down their data first to prevent hacking.
It’s time to turn the table and accuse them of violating our privacy by not safeguarding our data.
These governments can have access to my secure data as soon as I get access to theirs. Total transparency on their part. Of course that will never happen.
Crap, I am so pissed off. They already have access to our Twitter, FB, Google, iCloud data and access to location data. What more do they want???