Only 400 iTunes accounts compromised in fraud, Apple says
Over the weekend, it was reported that some iTunes account holders were involved in a number of fraud cases. Just how many accounts were compromised, though, was unknown. Clayton Morris of Fox News reached out to Apple for comment, and reported the company's official word on his personal blog this week.
"Apple told me that an extremely small percentage of users, about 400 of the 150 million iTunes users - that is less than 0.0003% of iTunes users, were impacted," he wrote.
It's the second time this week that Apple spoke out publicly on the issue. The company had previously revealed that the developer whose sales were boosted, Thuat Nguyen, was banned from the App Store and his applications were removed.
Nguyen occupied over 40 of the top 50 applications in the App Store's books category with a number of Japanese manga titles. The books were listed under the name "mycompany" with the website "Home.com." Apple's official statement said that Nguyen was involved in "fraudulent purchase patterns."
The company also recommended that users review their iTunes and credit card accounts to ensure that no unauthorized activity has taken place.
In addition, Apple said its own servers were not compromised at all in the incident, but the company is taking steps to further protect consumers who may have had weak passwords compromised.
"Apple says that starting today they're implementing a new security feature to minimize this type of fraud in the future," Morris wrote. "Basically you'll have to enter your credit card's CCV code a little more often from now on."
 Katie Marsal
Katie Marsal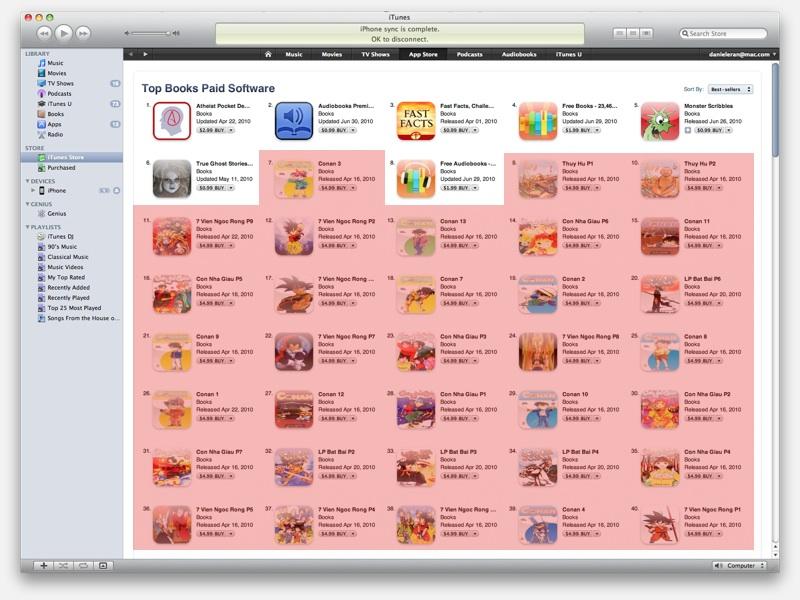






 Amber Neely
Amber Neely
 Thomas Sibilly
Thomas Sibilly
 AppleInsider Staff
AppleInsider Staff
 William Gallagher
William Gallagher
 Malcolm Owen
Malcolm Owen
 Christine McKee
Christine McKee








23 Comments
First!
'customers who had weak passwords compromised'.
I guess now we'll hear from all the people who think Apple should look over your shoulder while you select a password and make sure the password meets Apple's standards.
After that, we'll hear from all the people protesting Apple's interference in your selecting any password you want - no matter how weak it is.
After all, we all know that whatever happens, it's Apple's fault (unless something good happens, and then it's clearly not Apple's doing).
This sounds like bullcrap from Apple. How can 400 accounts make 40 books to jump into top 50 if we have over 150.000.000 iTunes accounts? Is 400 purchased copies enough to get to top selling?
This sounds like bullcrap from Apple. How can 400 accounts make 40 books to jump into top 50 if we have over 150.000.000 iTunes accounts? Is 400 purchased copies enough to get to top selling?
Because it's a time-dependent event. They measure sales over some small time period. Let's say that a top selling book sells 100,000 books in a year. That's under 300 per day. If they buy a single book from every one of those new accounts in the same day, it would jump to the top. It's really much easier to think about things rationally rather than accusing Apple of lying every time you don't understand something.
In reality, the numbers are probably even smaller. The data is somewhat older, but only 900,000 books OF ALL TITLES in the first month. I don't know how these 'book apps' fare compared to iBooks downloads, but it's likely that even 100 sales in a day would put you into the top ranking.
This sounds like bullcrap from Apple. How can 400 accounts make 40 books to jump into top 50 if we have over 150.000.000 iTunes accounts? Is 400 purchased copies enough to get to top selling?
I would love to hear how your two questions relate to you opening statement.
It sounds like you have come to a conclusion without any comprehension of the subject in question or really wanting to know the answer at all.
My hat's off to jragosta for trying. Not that it would matter. IMO.
BTW Jragista, you're right on re your first comment.
I'm curious how Apple came to the conclusion their statement implies: That weak user passwords is the sole vulnerability that was exploited. I certainly wouldn't argue against it being the most likely cause. Probably far more than 400 out of any set of 150 million people would unwisely choose to use weak passwords even if the account ties to their credit card. But how do they know? Was it simply a process of elimination - "We verified that our servers weren't compromised so it must have been guessed passwords," - or do they have some evidence that Thuat used a password cracker program? I hope its more than the former because its pretty tough to prove the negative that servers weren't compromised.
Since this is a fraud case, is the FBI going to investigate?