Google reportedly ignoring Safari users' privacy settings to better track its ads [u]
Last updated
According to an investigation by Wall Street Journal, Google and at least three other smaller web ad networks (Vibrant Media, Media Innovation Group and Gannett PointRoll), have purposely overridden Safari's browser privacy settings using code that misrepresents its ads as being a user-initiated form submission.
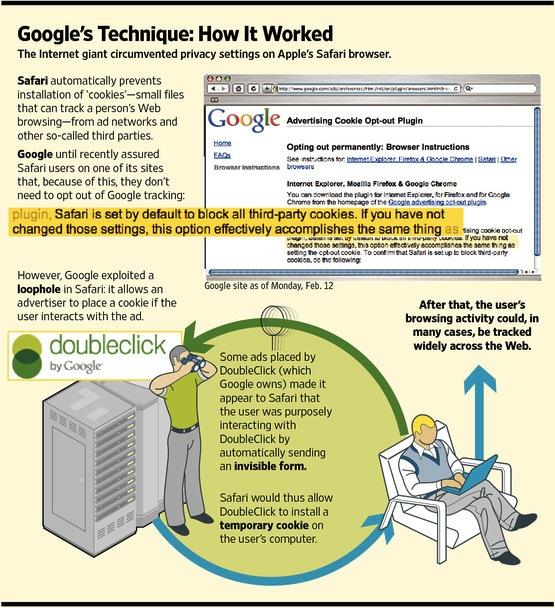
The default settings of Safari block cookies "from third parties and advertisers," a setting that is supposed to only allow sites that the user is directly interacting with to save a cookie (client side data that remote web servers can later access in subsequent visits).
Advertisers like Google save cookies on users' browsers so they can track their browsing habits across the various websites they place their ads on, and these "third party" cookies are expressly what the setting is designed to block.
The report notes that "Google added coding to some of its ads that made Safari think that a person was submitting an invisible form to Google. Safari would then let Google install a cookie on the phone or computer."
While the cookies were set to expire with a day or two, the report states that a "technical quirk in Safari" subsequently "allows companies to easily add more cookies to a user's computer once the company has installed at least one cookie," resulting in "extensive tracking of Safari users."
Google's hack around Safari's browser privacy settings was discovered by Stanford researcher Jonathan Mayer and "independently confirmed by a technical adviser to the Journal, Ashkan Soltani," who the site reported to have found Google's circumvention code enabling tracking for about a third of the web's top 100 sites for either desktop users or iOS users.
The Wall Street Journal named a wide variety of top websites, including Google's own YouTube, Aol, About.com, Comcast, NYTimes, YellowPages.com, Match.com and Fandango, as testing positive for Google's circumvention code, but noted that "there is no indication that any of the sites knew of the code" that Google was placing on their pages as a third party web advertising network.
The report cited Michael Balmoris, a spokesperson for AT&T, the operator of YellowPages.com, as saying "We were not aware of this behavior," and "we would never condone it."
It also cited an unnamed "official" from Apple as saying "we are working to put a stop" to the circumvention of Safari's privacy settings by advertisers like Google.
Google itself issued a statement saying the Wall Street Journal "mischaracterizes what happened and why. We used known Safari functionality to provide features that signed-in Google users had enabled. It's important to stress that these advertising cookies do not collect personal information."
Update: Google reached out to AppleInsider to share the following comment from the company's senior vice president of Communications and Public Policy, Rachel Whetstone:
The Journal mischaracterizes what happened and why. We used known Safari functionality to provide features that signed-in Google users had enabled. It’s important to stress that these advertising cookies do not collect personal information.
Unlike other major browsers, Apple’s Safari browser blocks third-party cookies by default. However, Safari enables many web features for its users that rely on third parties and third-party cookies, such as “Like†buttons. Last year, we began using this functionality to enable features for signed-in Google users on Safari who had opted to see personalized ads and other content— such as the ability to “+1†things that interest them.
To enable these features, we created a temporary communication link between Safari browsers and Google’s servers, so that we could ascertain whether Safari users were also signed into Google, and had opted for this type of personalization. But we designed this so that the information passing between the user’s Safari browser and Google’s servers was anonymous— effectively creating a barrier between their personal information and the web content they browse.
However, the Safari browser contained functionality that then enabled other Google advertising cookies to be set on the browser. We didn’t anticipate that this would happen, and we have now started removing these advertising cookies from Safari browsers. It’s important to stress that, just as on other browsers, these advertising cookies do not collect personal information.
Users of Internet Explorer, Firefox and Chrome were not affected. Nor were users of any browser (including Safari) who have opted out of our interest-based advertising program using Google’s Ads Preferences Manager.
Vibrant Media, another web advertiser using similar tactics to Google's, called the circumvention a "workaround" intended to "make Safari work like all the other browsers," because other major browsers, including Google's own Chrome and the almost exclusively Google-financed Mozilla Firefox, do not block third party cookie tracking by default.
Google is already under government scrutiny regarding its privacy policies. In a settlement last year with the US Federal Trade Commission, the company agreed not to "misrepresent" privacy practices to customers or pay a fine of $16,000 per violation per day.
However, in its own online privacy guide, Google represented to Safari users that they did not need to do anything to opt out of its advertising cookies because "Safari is set by default to block all third-party cookies. If you have not changed those settings, this option effectively accomplishes the same thing."
Google has since removed that wording from its site, and after being contacted by the Wall Street Journal, has also reportedly disabled the tracking code to circumvent Safari's privacy settings.
 Daniel Eran Dilger
Daniel Eran Dilger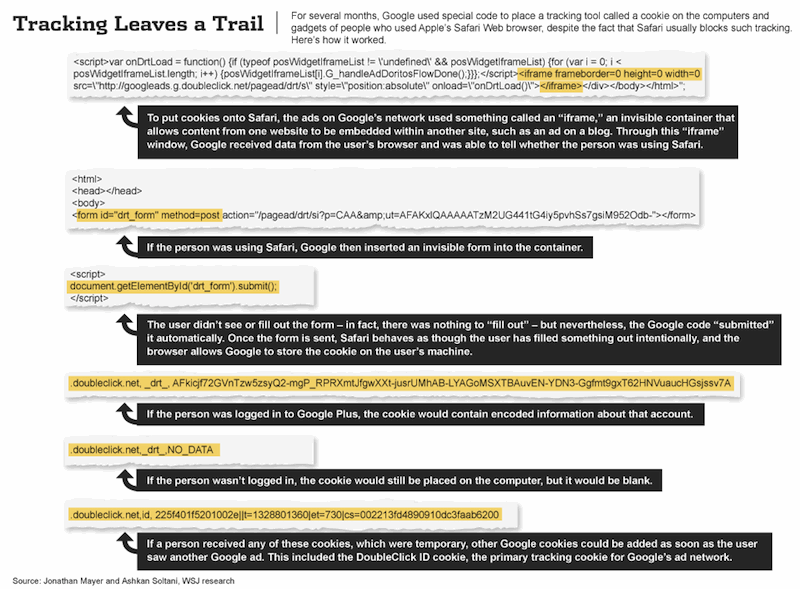











 Amber Neely
Amber Neely
 Thomas Sibilly
Thomas Sibilly
 AppleInsider Staff
AppleInsider Staff
 William Gallagher
William Gallagher
 Malcolm Owen
Malcolm Owen
 Christine McKee
Christine McKee









106 Comments
Heinous.
It's the mysterious iframe--the standard HTML element for many revisions and yet to be sandboxed seamlessly in Chrome and Safari.
Sandbox the bastard already. I'd really like to not have 2 sets of CSS files. to make iframes match the look n' feel of their parent window container.
I guess if you customers aren't willing to pay for your product you have got to find somebody you can screw to make a buck. After all, it costs a lot of money trying to copy Apples every move.
Javascript is your friend.
The Internet is just too hard for the geniuses at Google, and so is the smartphone business. When the only way you can make a buck is by screwing people behind their backs, maybe you need to find another line of work.