Hack allows free access to in-app iOS purchases [u]
Last updated
Editor's note: AppleInsider does not condone illegal activity or EULA abuse and in no way endorses the activity described below. As such this article is presented purely for discussion.
According to a report by MacWorld, Russian coder Alexey V. Borodin is responsible for finding and taking advantage of the exploit which was subsequently posted to YouTube. As of this writing the video had accumulated over 2,000 views.
The process entails installing forged digital certificates onto an iOS device and connecting to a unique DNS server which the app believes to be Apple's official App Store. Borodin explains that the server then sends spoofed code receipts, normally issued by Apple, to the app which in turn validates the purchase. He goes on to say that the receipts were "easy to spoof" because they are generic and contain no specific user data.
While other hacks require a jailbroken iOS device able to run proprietary code, the newest iOS exploit simply takes advantage of what can be perceived as a hole in Apple's purchasing system.
Apparently Borodin created the bypass as a "challenge" to developers of CSR Racing, a so-called "freemium" app that costs nothing to download but offers exclusive in-app purchases to unlock special content.
“I set this up due to hungry and lazy developers, Borodin wrote in an instant message conversation with the publication. "I was very angry to see that CSR Racing developer taking money from me every single breath.â€
Screenshot of Borodin's in-app purchasing workaround being used on CSR Racing. | ZonD80's YouTube channel
Instapaper developer Marco Arment believes that the hack will only work for one-time in-app purchases while subscription-based buys should be unaffected.
“It probably won’t affect the auto-renewing subscriptions, since they rely on a lot of server-side processing to track, but it wouldn’t surprise me if it could affect any other [in-app purchase] type (including non-renewable ‘subscriptions’ like what Instapaper uses) if the apps don’t check with Apple’s verification servers from their own web services,†Arment writes.
Employing the hack not only affects developers' incomes but users could face negative implications as well and the fault may lie with Apple's purchasing system.
“I can see the Apple ID and password [of users who use the hack],†Borodin said. “But not the credit card information.†It appears that Apple's system passes both bits of sensitive information to the Apple Store server in unencrypted plain text.
The exploit is likely an easy fix for Apple, said developer Marco Tabini, though a patch woud likely involve a software update.
Borodin claims that he is not worried about any legal action from Apple and instead took a different spin on the situation: “I’m a happy user of iPhone 4S … I think they will hire me.â€
Update: Apple caught wind of Borodin's successful App Store receipt validation scheme and has issued the following statement (via The Loop):
“The security of the App Store is incredibly important to us and the developer community, Natalie Harrison, told The Loop. “We take reports of fraudulent activity very seriously and we are investigating.â€
 AppleInsider Staff
AppleInsider Staff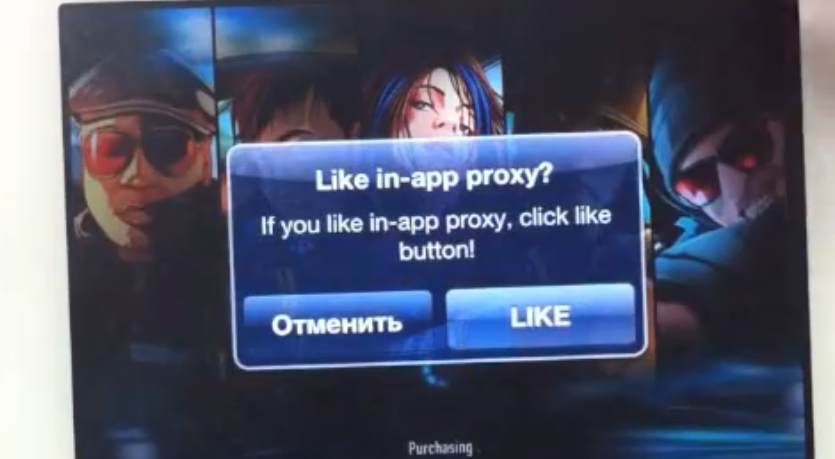











 Amber Neely
Amber Neely
 Thomas Sibilly
Thomas Sibilly
 William Gallagher
William Gallagher
 Malcolm Owen
Malcolm Owen
 Christine McKee
Christine McKee









69 Comments
Okay, why are we reporting this at all? "To get the word out and make sure Apple and developers know about it." Still.
"To get the word out and make sure Apple and developers know about it."
As a developer, I'd like to address Alexey with this... I'm an app developer who is neither lazy nor greedy. I'm trying to make a paycheck and it takes time and energy to create value in apps. We want to keep the cost of our app low, so we use in-app purchases when we add new features that not everyone wants to pay for. We already deal with the app being pirated and now we have the prospect of in-app purchases being stolen as well. Why don't you get a life and actually try to improve upon your world instead of stealing from hard working developers who are trying to make a living?
This is probably better not blasted all over every Apple fansite.
[quote name="Negafox" url="/t/151270/hack-allows-free-acces-to-in-app-ios-purchases#post_2146578"]This is probably better not blasted all over every Apple fansite. [/quote] Probably so, but too late because AI was actually late to this party. Who really wants to pass their user name and password to Russia? Please people, you're only asking for trouble if you use this hack.