Security on Apple's iOS is notably tight, but an Israeli firm has pointed out that the profile system for iPads and iPhones could leave users open to remote attacks resulting in data theft.
Israeli firm Skycure Security on Wednesday published a proof-of-concept vulnerability report on the company blog (via InformationWeek). Skycure's report shows how malicious users could leverage iOS profiles, also known as mobileconfig files, in order to circumvent Apple's malware protections.
Malicious apps are filtered in the App Store approval process, making it more difficult than on other platforms for them to get onto iDevice users' machines in the first place. Furthermore, iOS' sandboxing structure makes it difficult for apps to access anything outside of their set permissions. Mobileconfig files, though, are used by cellular carriers, Mobile Device Management solutions, and some mobile applications to configure certain system-level settings for iOS devices, including Wi-Fi, VPN, email, and APN settings.
Skycure claims that, with a bit of social engineering, an attacker could get victims to download a malicious iOS profile. The attacker could do so by, for example, promising a user access to popular movies and TV shows on an attacker-controlled website. The user would install an iOS profile to "configure" their devices accordingly, and the attacker would then have access.
With access to the user's device, an attacker could route all of the victim's traffic through the attacker's server or install root certificates on the victim's device, allowing for interception and decryption of SSL/TLS secure connections.
Skycure also notes that some AT&T stores, in signing up customers for pay-as-you-go accounts, were directing those customers to download and install a profile from unlockit.co.nz on an unencrypted channel. The installation of that mobile configuration is necessary to get access to AT&T's data network, but downloading a mobileconfig file in such a manner, Skycure says, leaves users wide open to man in the middle attacks, especially when performed over a public Wi-Fi network.
Skycure recommends that iDevice users only install profiles from trusted websites and applications and do so only through a secure channel, indicated by an address beginning with https. The firm also recommends wariness when faced with a non-verified mobileconfigs, calling them cause for suspicion.
 Kevin Bostic
Kevin Bostic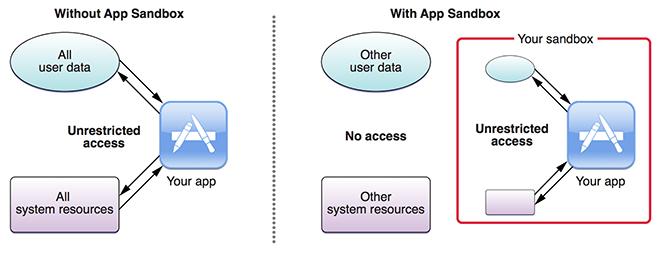






-m.jpg)






 Wesley Hilliard
Wesley Hilliard
 Malcolm Owen
Malcolm Owen
 Mike Wuerthele and Malcolm Owen
Mike Wuerthele and Malcolm Owen
 Amber Neely
Amber Neely

 William Gallagher
William Gallagher

 Christine McKee
Christine McKee







16 Comments
Apple winning
The part about AT&T is strange indeed. I had to do exactly that to get data working on my pay-as-you-go account. It sucks that they won't officially support iPhones unless they're on an expensive post-paid plan.
Skycure claims that, with a bit of social engineering, an attacker could get victims to download a malicious iOS profile. The attacker could do so by, for example, promising a user access to popular movies and TV shows on an attacker-controlled website. The user would install an iOS profile to "configure" their devices accordingly, and the attacker would then have access.
Yet another fallacious vulnerability report. This non-issue vulnerability needed the users intervention for downloading the profile and accept to install it on his device. I don't think sane people will fail in this trap, there is nothing new here and I don't see how the mobileconfig features can be view as vulnerability as long you need the user consent to proceed.
You always can do whatever hack you want thru social engineering with idiot...
So an app, that isn't likely to make it into the store in the first place, could be used perhaps to do nasty things to a device and its data. But no such app has been found to be in the store so at the moment the only possible threat might be to those that jailbreak and install apps via Cydia etc who don't vet to any degree.
Meanwhile there's a HUGE security hole on iOS that remains unpatched: With a little simple social engineering, an attacker can persuade a user to turn off their passcode, mail the attacker their phone and house key, tell the attacker all their passwords, and go to work in a third-world copper mine with all paychecks forwarded to the attacker.