In a blog post late Monday, network security firm FireEye claims to have discovered a new iOS "flaw" that allows a nefarious app to log touch events and button presses in the background, then send the data off to a remote server.
First spotted by ArsTechnica, the post describes a proof-of-concept that FireEye researchers say can collect and transmit potentially sensitive information while running in the background.
From what can be gleaned from FireEye's blog, the supposed "flaw" takes advantage of iOS' built-in multitasking components, suggesting the attacking app must first be vetted and installed on an affected device to access legitimate APIs. Barring the side-loading of an app with private APIs, such as those certified for internal distribution through Apple's remote management solution, the app would have to successfully sneak by the App Store review process in order to work.
To this end, FireEye claims to have developed "approaches to bypass" Apple's app review process, but does not detail the workarounds.
Note that the demo exploits the latest 7.0.4 version of iOS system on a non-jailbroken iPhone 5s device successfully. We have verified that the same vulnerability also exists in iOS versions 7.0.5, 7.0.6 and 6.1.x. Based on the findings, potential attackers can either use phishing to mislead the victim to install a malicious/vulnerable app or exploit another remote vulnerability of some app, and then conduct background monitoring.
The monitoring app can reportedly record all input events in the background, including on-screen touches and physical button actuation like the home button, Touch ID and volume controls.
Further, FireEye notes that disabling iOS 7's background app refresh feature will not block said monitoring app from collecting and disseminating data. The firm offers the example of music apps that were granted access to background processes in earlier versions of iOS.
According to ArsTechnica, a now-removed blog post from FireEye claimed the firm had "successfully delivered a proof-of-concept monitoring app through the App Store that records user activity and sends it to a remote server. We have been collaborating with Apple on this issue."
FireEye's discovery, if it can be deemed as much, comes as Apple is being scrutinized over an SSL security flaw found recently in both iOS and OS X. The so-called "goto fail" error potentially opens the door for hackers to surreptitiously intercept data meant to be encrypted.
Apple issued a patch for iOS last week and is working on a fix for OS X that should see release soon.
 AppleInsider Staff
AppleInsider Staff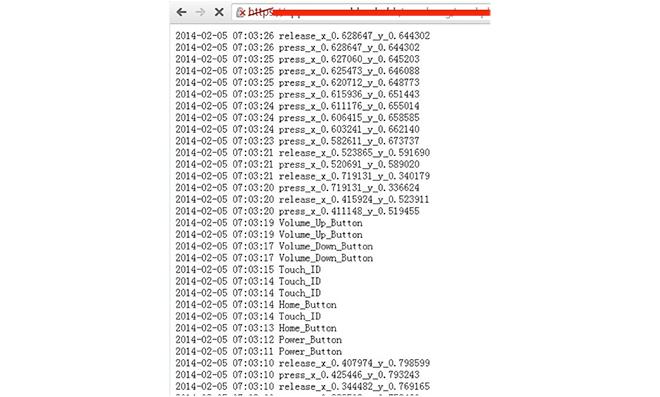







-m.jpg)






 Charles Martin
Charles Martin
 Christine McKee
Christine McKee
 Wesley Hilliard
Wesley Hilliard
 Malcolm Owen
Malcolm Owen
 Andrew Orr
Andrew Orr
 William Gallagher
William Gallagher
 Sponsored Content
Sponsored Content








24 Comments
Just great... C'mon Apple. I thought you were better than this!
So do I have this right? Getting an app that leverages this "flaw" would require jailbreaking (or else you self-installing the app as a developer/enterprise deployment on your own device)? How is that news? You can do all kinds of questionable things by jailbreaking/side loading. So what is seemingly newsworthy is not the background thing at all, but rather a second, unrelated flaw, in Apple's review process. If such a flaw exists (sounds plausible, but they are very vague) then--and only then--could such an app actually get onto normal users' phones? And they've backtracked, removing their formerly-posted claim to have gotten an instance of this onto the App Store? C'mon journalists and fact-checkers, I thought you were better than this! Until I see real evidence, this sounds like FireEye putting out misleading info to drum up publicity.
just as Lois implied I'm shocked that a person able to earn $7362 in 1 month on the internet . go now www.fiscalpen.com
So do I have this right? Getting an app that leverages this "flaw" would require jailbreaking (or else you self-installing the app as a developer/enterprise deployment on your own device)? How is that news? You can do all kinds of questionable things by jailbreaking/side loading.
So what is seemingly newsworthy is not the background thing at all, but rather a second, unrelated flaw, in Apple's review process. If such a flaw exists (sounds plausible, but they are very vague) then--and only then--could such an app actually get onto normal users' phones?
And they've backtracked, removing their formerly-posted claim to have gotten an instance of this onto the App Store?
C'mon journalists and fact-checkers, I thought you were better than this! Until I see real evidence, this sounds like FireEye putting out misleading info to drum up publicity.
So what is seemingly newsworthy is not the background thing at all, but rather a second, unrelated flaw, in Apple's review process. If such a flaw exists (sounds plausible, but they are very vague) then--and only then--could such an app actually get onto normal users' phones?
Apple's app review process isn't what you think. Apple only sees the binary, it's very easy to sneak code past. Just look how many tethering apps got through.
http://appleinsider.com/articles/13/08/16/apples-approval-of-jekyll-malware-app-reveal-flaws-in-app-store-review-process