Some Mac users received a nasty surprise last week when it was discovered that a recent version of the open source Transmission BitTorrent client infected their computer with malware — a situation that may have been avoided with proper precautions.
Most savvy computer users know that it's important to be vigilant about where they download software from, but few stop to verify that the file they received is the file they were supposed to receive. This can be a critical final step in preventing malware infections of the sort we saw with Transmission.
Developers often post checksums or hashes alongside the download links for their projects to facilitate this kind of verification. Broadly, a checksum is the result of a mathematical calculation run on a particular file — if the file hasn't been altered, the checksum you calculate will match the checksum provided by the developer.
It's still not clear exactly how the infected download made it onto Transmission's website, but those who received it early in the process have reported that the bad file's checksum didn't match the checksum provided by the Transmission team. If they had verified the checksum before installing, they would've known something was amiss.
It's worth mentioning that this is not an infallible process: if a website is compromised, the attacker could've easily changed the checksum as well. Still, it's a useful — and very quick — precaution to take.
Important note: For most people, files will be automatically placed in their downloads folder. To access this folder in Terminal, use ~/Downloads.
Verifying an SHA-1 checksum
SHA-1 is the checksum format used by Apple, among many others. To find the SHA1 checksum of a file, open a Terminal window and enter the following:
openssl sha1 /full/path/to/file
If your file is called Paint.dmg and it's in the Downloads folder, it would look like this:
openssl sha1 ~/Downloads/Paint.dmg
The result should look like this:
SHA1(/Users/username/Downloads/Paint.dmg) =07272d863ab77113e38e6ce3878c2162feb4893e
The series of letters and numbers in the result is the checksum: just compare it to the checksum provided by the developer.
Verifying an SHA256 checksum
Another popular checksum is SHA256, the kind used by Transmission's team. To verify it on a Mac, use:
openssl dgst -sha256 /full/path/to/file
Verifying an MD5 checksum
MD5 is no longer recommended as a checksum hash for security reasons, but some legacy programs may still use it. To verify:
openssl md5 /full/path/to/file
 AppleInsider Staff
AppleInsider Staff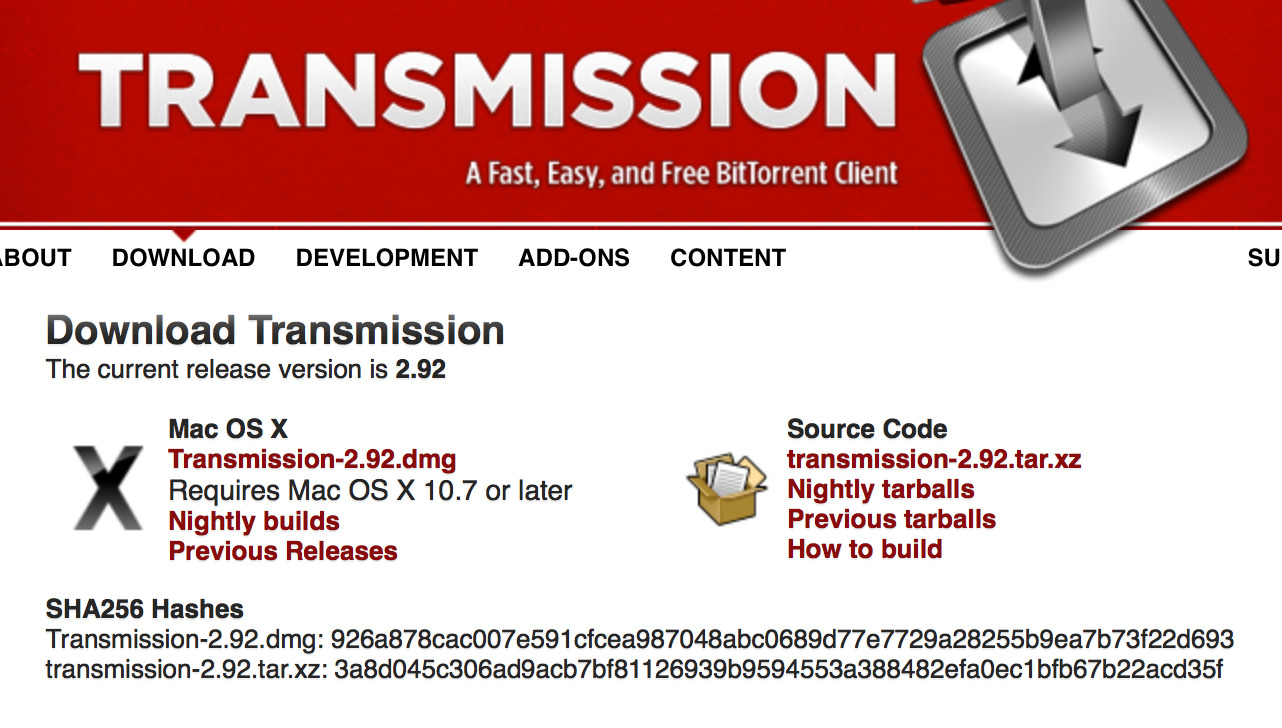







-m.jpg)






 Christine McKee
Christine McKee
 William Gallagher
William Gallagher
 Amber Neely
Amber Neely
 Andrew O'Hara
Andrew O'Hara

 Sponsored Content
Sponsored Content
 Charles Martin
Charles Martin








4 Comments
Is there a terminal command that returns what checksum method is used for a file? It would be nice to have an Automator script that would look at the file and return a checksum for the less than tech savy users. AI could start a whole series of these scripts...
Seems like this is ripe for an app on the mac store.
Sure I can type the command, but an app is pretty necessary for comparing the two hashes, and there are apps that do this. Why not point those out?