It appears Apple's quick fix for the recently discovered root user bug can be disabled by upgrading to macOS 10.13.1 from a previous version of the operating system, meaning users who do so are unwittingly reintroducing the glaring security hole.
According to a Wired report on Friday, multiple users have confirmed that upgrading from macOS 10.13.0 High Sierra to the latest version 10.13.1, released at the end of October, defeats Apple's security patch for the root user login flaw.
In particular, users running macOS 10.13.0 who downloaded and installed the security update released on Wednesday say the root bug reappears after upgrading to macOS 10.13.1.
Making matters worse, two people who attempted to reinstall Apple's fix after upgrading to macOS 10.13.1 say the root login bug persists until the system is rebooted. Apple in its documentation does not list rebooting as part of the required installation process.
"I installed the update again from the App Store, and verified that I could still trigger the bug. That is bad, bad, bad," said Thomas Reed, a security researcher at MalwareBytes. "Anyone who hasn't yet updated to 10.13.1, they're now in the pipeline headed straight for this issue."
Reed went on to point out that many Mac owners do not reboot their computer for months at a time, meaning the root flaw could in some cases linger.
Earlier this week researchers publicized a macOS security bug that allows anyone to log in to a Mac running High Sierra as its "root" System Administrator without first requiring a password. Less than a 24 hours later, Apple pushed out Security Update 2017-001 via the Mac App Store, plugging the hole.
The security patch introduced its own problems, however, as users had issues authenticating or connecting to file shares on their Mac. Apple posted a quick Terminal fix to its Support Pages before reissuing the security patch with a permanent solution a few hours later.
While not as damaging as the original root user bug, the glitch in Apple's security patch is unusually sloppy for the Cupertino tech giant. How the two bugs in the security patch slipped past Apple's quality assurance team is unknown.
 Mikey Campbell
Mikey Campbell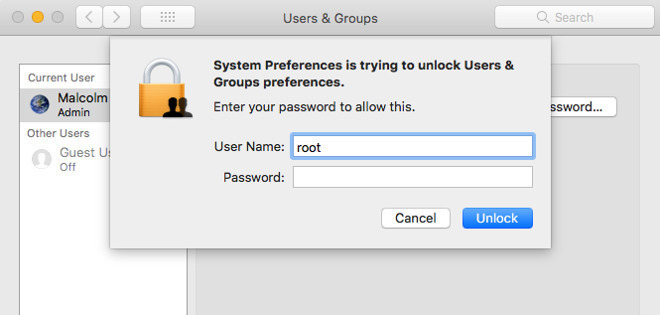







-m.jpg)





 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher


 Wesley Hilliard
Wesley Hilliard

 Christine McKee
Christine McKee




-m.jpg)




32 Comments
So, let me get this right... I already updated to 10.13.1 last month so it's not affecting the recent security update, right?
That's sick.
Sloppy
So, what's wrong with that? The update and the bug both work as expected. One will install 10.13.1 first, then install Security Update 2017-001 over that, else macOS will already automatically install the security update on 10.13.1. Apple should stick to the released build number and should not distribute the "corrected" one with a different build number: that would create huge confusions among users and support staff. This is how it works in Windows or other software too.
So...Apple is bad for not adding a patch released two days ago into an update released over a month ago? Hmmm...they’re an EVIL company for not adding future patches into their already released updates/upgrades! *sarcasm* I want all of next year’s updates and patches in last month’s update, I tell ya!! hahaha