The macOS email client Airmail 3 contains a number of severe vulnerabilities, researchers claim, with attackers potentially able to use the exploits to steal a user's emails and attachments, just from the user opening a specially-constructed message.
The way Airmail 3 handles URL requests can be abused to acquire a victim's data, VerSprite researchers advised to ThreatPost. An email could consist of a link containing a URL request, one that uses the "send mail" function of the client in such a way that it could send an email back without the user's knowledge, if clicked.
As part of the same boobytrapped message, other code could be embedded that makes the client attach files to the outbound email. A second vulnerability allows attackers to request specific documents from the user account database, such as previously received or sent emails and attachments, and covertly include them in the outbound message.
While this second vulnerability requires the name of the file, it is noted Airmail 3 stores its data in a fairly open way within SQLite databases, with paths researchers suggested were "relatively deterministic" and easy to guess, if not discover.
A third vulnerability, an "incomplete blacklist" of HTML Frame Owner Elements, could allow Webkit Frame instances to be opened through the email. As sub-classes of these are not forbidden by the client, the researchers note this could be abused to bypass an HTML filter to avoid included HTML plug-ins being classed as malicious, with as many as 12 plug-ins able to be used to request attachments.
While the majority of the vulnerabilities would require a user to actively click on links, a fourth vulnerability can allow for attacks to take place by the user simply opening the email, without clicking any of its contents. In some cases, Airmail's EventHandler navigation filter can be bypassed, allowing an embedded HTML element to open automatically without user intervention.
Researcher Fabius Watson admits the fourth vulnerability isn't reliable, with it only successful roughly half the time, but it does open up the possibility for link-based attacks without needing the user to click them. Watson also notes that, even if it fails to automatically run, attacks can still end up successful if users click links in the trap message.
The flaws were found in the Mac version of Airmail 3, but it is unclear if similar flaws appear in the iOS version of the client. VerSprite is in the process of submitting the vulnerabilities to the MITRE database, and it has also reported the issues to Airmail, but patches have yet to be released to fix the issues.
"I would avoid using Airmail 3 until this is fixed," Watson advised to the report.
Airmail informed AppleInsider a fix will be arriving "probably today." The URL-based sending is said to be a feature to allow Airmail to automatically send messages, but it will require a confirmation by users to actually send the outbound mail in future.
The company also dismisses the potential impact of the exploit, calling it "very hypothetical," and advising no users have reported themselves as being affected by it.
 Malcolm Owen
Malcolm Owen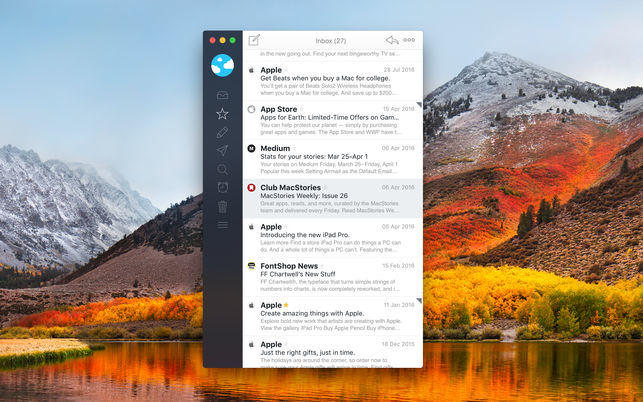







-m.jpg)






 Christine McKee
Christine McKee

 Sponsored Content
Sponsored Content

 Amber Neely
Amber Neely










6 Comments
I use the Apple Supplied mousetraps. Mail, Pages, Numbers, Keynote, Safari, Calendar, etc. Makes it easy.
The update is at the App store.