The team behind jailbreaking tool "unc0ver" on Wednesday said a new version of the software currently undergoing performance testing is effective against all current iOS versions, including the recently released iOS 13.5.
Leveraging an unspecified zero-day kernel exploit discovered by researcher "pwn2ownd," version 5.0 of "unc0ver" is capable of jailbreaking "every signed iOS version on every device," the "unc0ver Team" said in a tweet.
According to the group's webpage, the upcoming "unc0ver" iteration supports Apple-signed iOS releases from iOS 11 through iOS 13.5.
In August 2019, pwn2ownd released a version of unc0ver effective on devices running then-current iOS versions after Apple mistakenly unpatched a critical vulnerability in iOS 12.4. The first publicly available jailbreak to see wide distribution in years, unc0ver was neutralized with a subsequent fix issued in September. That same month, hacker "axi0mX" unveiled a tethered jailbreak for iOS 13.1.1 utilizing the Checkm8 exploit.
Jailbreaks are commonly used to escape Apple's "sandbox," granting access to hardware and software features not accessible by users under normal circumstances. The jailbreak community thrived in the early days of iOS thanks in part to Apple's iron fist implementation of iOS, but the technique slowly fell out of favor as the platform matured, gaining official customization options and app affordances.
Today's jailbreak news arrives just hours after Apple issued iOS 13.5 with a number of new features and user experience tweaks designed to cope with the ongoing coronavirus pandemic. For example, devices with Face ID authentication will automatically display a manual passcode verification prompt when a face mask is detected.
Apple's latest iOS version also includes the first public release of the company's Exposure Notification API. Developed in partnership with Google, the cross-platform tracking solution logs contact with anonymized Bluetooth beacons and, paired with a voluntary alert system, notifies users to recent interactions with participants who report contraction of COVID-19. Public health agencies developing contact tracing apps can build on the latticework as Apple and Google work to bake Exposure Notification assets into their respective iOS and Android operating systems.
 AppleInsider Staff
AppleInsider Staff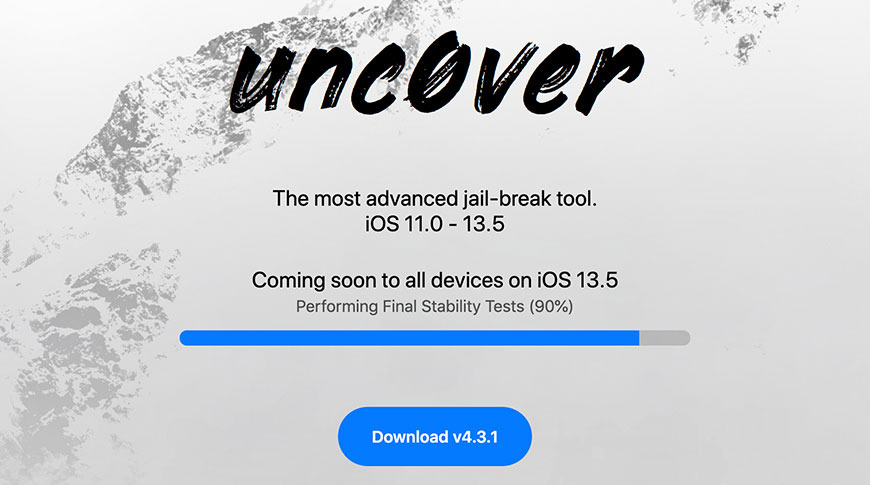







-m.jpg)






 Brian Patterson
Brian Patterson
 Charles Martin
Charles Martin


 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher
 Christine McKee
Christine McKee
 Marko Zivkovic
Marko Zivkovic







18 Comments
I’d much rather have the zero day patched.
Hopefully when this is released Apple is the first to download and reverse engineer it... and squash it.
Time for Apple to pay off these hackers to hack the companies the FBI uses to break into iPhones. Two can play this game.
The last time I jail-broke an iPhone was the first gen. iPhone when I got the iPhone 3G. The main purpose was to record video. I also downloaded the "I Am Rich" app on that via the jail-break.
The necessity of jail-breaking is now less for the average user, but I can see how it makes for a nice hobby to the tech enthusiasts.
Maybe Apple needs to come up with an iOS that once hacked, puts a Trojan horse back into the hackers network