A new piece of Mac ransomware distributed via pirated software, dubbed "EvilQuest," is actively targeting macOS users in the wild.
Although ransomware specifically aimed at Mac users are particularly rare, new instances of malicious software that encrypt user files and demands a ransom to unlock them do surface from time to time.
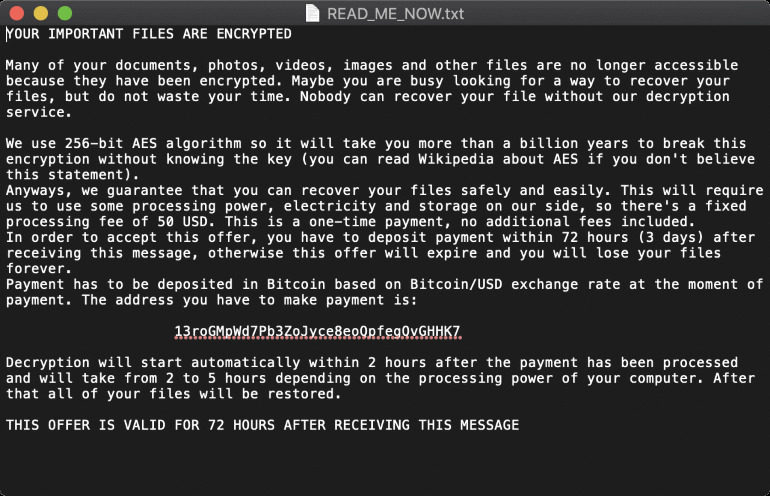
On Tuesday, several security researchers published analysis and reports of the newly discovered "OSX.EvilQuest" ransomware. First spotted by independent malware researcher Dinesh Devadoss, EvilQuest is said to have been circulating in the wild since the start of June 2020, ZDNet reported.
EvilQuest has a few nefarious additions that make it unique among ransomware examples. In addition to maliciously encrypting a user's files and charging money to unlock them, EvilQuest also installs a keylogger and a reverse shell on a system, along with code that steals cryptocurrency wallet files.
According to former NSA hacker and Jamf macOS security researcher Patrick Wardle, those capabilities could allow attackers "full control over an infected host."
As with previous pieces of Mac ransomware, it appears that EvilQuest is distributed via pirated software. Researchers have found it bundled in a package called Google Software Update, while others have seen it hidden in pirated versions of DJ app Mixed In Key and security tool Little Snitch.
According to Malwarebytes Mac & Mobile chief Thomas Reed, the ransomware also attempts to modify files in Google Chrome's update mechanism in an effort to gain persistence on an infected machine.
This the third instance of a piece of ransomware surfacing that specifically targets macOS users, following the discovery of Patcher in 2017 and KeRanger in 2016.
How to avoid or mitigate the EvilQuest ransomware
At this point, it appears that EvilQuest is solely being distributed through torrenting websites and pirated software. So if you stick to the Mac App Store or third-party developers that you trust, you should be able to avoid getting it.
There are also two apps that can mitigate the risks of EvilQuest for users.
Wardle's free and open-source RansomWhere? app can generically detect and stop ransomware on macOS. The latest version of Malwarebytes can also detect and mitigate EvilQuest before it does any damage.
 Mike Peterson
Mike Peterson







-m.jpg)






 Charles Martin
Charles Martin
 Christine McKee
Christine McKee
 Wesley Hilliard
Wesley Hilliard
 Malcolm Owen
Malcolm Owen
 Andrew Orr
Andrew Orr
 William Gallagher
William Gallagher
 Sponsored Content
Sponsored Content








16 Comments
AppleInsider might also consider recommending regular OFFLINE backups of data your files in macOS. (Offline meaning backups that are taken to external media, with the medium immediately disconnected from the computer after the backup is completed.) Time Machine fits the bill here. Even if you do get hit with the ransomware, there’s no reason to pay the ransom if you can restore from a previous back-up.
Another alternative is a cloud backup service such as Backblaze or Carbonite. These services keep multiple versions and are a good defense against physical loss such as a house fire or burglary. I’m not sure about Carbonite but Backblaze which I use is quite inexpensive.
Still another alternative is to not download pirated apps and stick as much as possible to software from the Mac Store and trusted vendors.