A now-fixed exploit in the macOS version of Microsoft Office may have allowed attackers to hack a Mac user just by getting them to open a document.
The exploit was developed by Jamf security engineer and ex-NSA hacker Patrick Wardle, who has long specialized in hacking Macs. Wardle showed off the attack method at the Black Hat 2020 security conference Wednesday.
As he explained on his blog, it takes advantage of macros in Microsoft Office. That's an age-old technique for hacking Windows, but Mac-targeting macro attacks are "growing in popularity and are quite en vogue," Wardle wrote.
Leveraging macros, which are essentially small programs embedded in files, is only one part of the equation. To actually get the exploit to work, Wardle had to string together several other vulnerabilities.
By creating a file with an old .slk format, Wardle was able to get Office to run macros without alerting the user Adding a "$" character to the start of the filename allowed Wardle to escape the macOS sandbox. Finally, Wardle zipped the file into a .zip format — which macOS doesn't check against its notarization requirements.
The attack is complicated, but illustrates a good point about the way an attacker may think. By leveraging multiple vulnerabilities and techniques, Wardle was able to create an exploit that only required users to double-click a Word document.
Wardle notes that a user still needs to authenticate some of the actions by logging in. But if a user does authenticate it, an attacker could install backdoors or other malicious files — opening the door to further attacks.
Luckily for Mac users, the vulnerabilities that Wardle took advantage of were patched in the latest version of Office on Mac and macOS 10.15.3. Still, with macro-based attacks on the rise, it's likely that similar vulnerabilities could come to light in the future.
Wardle alerted both Microsoft and Apple of the flaws, but told Motherboard that the latter company didn't respond to his report.
Apple opened a bug bounty program for macOS in 2019, but Wardle told Motherboard that he has never received any money from the company for exploits or vulnerabilities that he has discovered.
 Mike Peterson
Mike Peterson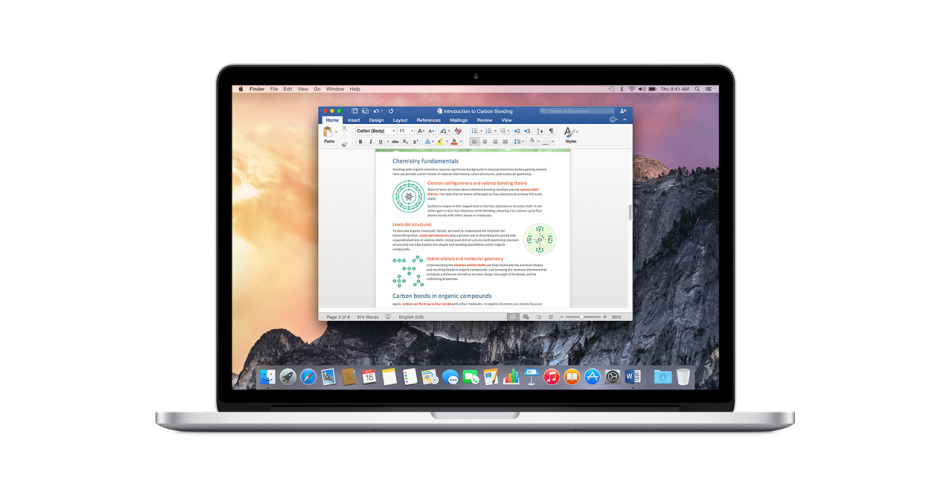







-m.jpg)






 Christine McKee
Christine McKee
 Wesley Hilliard
Wesley Hilliard
 Thomas Sibilly
Thomas Sibilly
 Marko Zivkovic
Marko Zivkovic
 Andrew O'Hara
Andrew O'Hara
 Amber Neely
Amber Neely
 William Gallagher
William Gallagher









5 Comments
So what version is the patched one?
Yes, one of Microsoft’s to the computing world is VBA – Virus Basic for Applications, a programming language that simplified the creation of cross-platform malware. Not surprised to see they’ve introduced a new malware platform for the Cloud age.