Brazilian iPhone thieves demonstrate importance of responsible password practices
Last updated
A recent rash of iPhone thefts in Brazil serves as yet another cautionary tale for users who store passwords in an unsecured location on their device.
In June, reports surfaced about a string of Brazilian iPhone thefts that dates back to 2020. Instead of flipping the hardware for cash, thieves sought a more lucrative payout by using the devices to gain unauthorized access to victims' bank accounts.
Exactly how the locked iPhones were breached and bank accounts accessed remained unknown until Sao Paulo authorities arrested members of a gang that specialized in the technique. Unlike government data gathering operations or sophisticated hacks that require expensive equipment and obscure software exploits, all that was needed was SIM card removal tool, reports Folha de Sao Paulo.
According to Police Chief Fabiano Barbeiro, criminals take the SIM out of a victim's iPhone, place it in an unlocked device and search for linked accounts on social media networks like Facebook or Instagram. Once an account connected to the phone line is found, the intruder searches for an associated email address which, according to one suspect, is usually also paired to a user's Apple ID.
Using the email account and phone number, the thieves reset the Apple ID password on the unlocked iPhone, download system backup information from iCloud and conduct a search for "password," presumably through Spotlight. In many cases, victims store passwords, account numbers and other important information in plain text, according to the suspect.
With the information in hand, the SIM card is swapped back to the original iPhone. Another gang member responsible for accessing bank accounts takes charge of the device and uses it to siphon off money.
9to5Mac spotted news of the Brazilian iPhone crime ring earlier today.
Apple does include certain security features that can mitigate portions of the attack, including two-factor authentication and remote data wipe in Lost Mode. Indeed, the company in a statement last month promised to make data erasure features "easier to access." Still, the security safeguards are only effective if they are enabled prior to theft.
In this case, and as a general rule, it's never safe to store passwords locally in an unsecured location. For those who deal with multiple passwords or "strong" randomized passcodes that are difficult to memorize, investing in a password manager or using Apple's own Keychain are viable options.
Keep up with everything Apple in the weekly AppleInsider Podcast — and get a fast news update from AppleInsider Daily. Just say, "Hey, Siri," to your HomePod mini and ask for these podcasts, and our latest HomeKit Insider episode too. If you want an ad-free main AppleInsider Podcast experience, you can support the AppleInsider podcast by subscribing for $5 per month through Apple's Podcasts app, or via Patreon if you prefer any other podcast player.
 Mikey Campbell
Mikey Campbell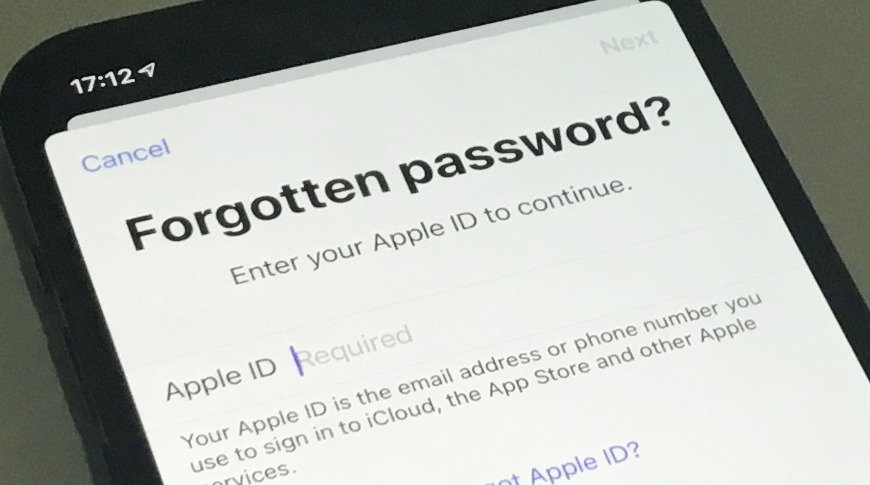











 Amber Neely
Amber Neely
 Thomas Sibilly
Thomas Sibilly
 AppleInsider Staff
AppleInsider Staff
 William Gallagher
William Gallagher
 Malcolm Owen
Malcolm Owen
 Christine McKee
Christine McKee









16 Comments
Yet another reason why using SMS to send 2FA or recovery codes is a bad idea...
I’m dumbfounded as to why anybody would list their passwords next to or under the actual word “password”. Even my non-tech savvy mother knows not to do this. If passwords must absolutely be stored on the phone, at least be clever enough to label them as something else. And I’ve never had to reset my Apple ID or do any of the other things these thieves did, but wouldn’t storing such information in a locked note eliminate this risk since Touch ID and Face ID info is encrypted in the Secure Enclave?
I'm a bit lost here. I understand that having the SIM card gives the thief's phone the phone number of the stolen one, but is there any info stored on the SIM that would contain the social media information? But I could see a link between the phone number and a Facebook account for example -- if the thief can search by the phone number and find the Facebook account somehow that connects the two.