Apple has released more details about its macOS High Sierra 10.13 Supplemental Update released on Thursday, advising it fixed two security issues relating to APFS volume encryption and a potential hack that could allow an attacker to extract a user's keychain passwords.
The first issue was reported to Apple by Matheus Mariano of Leet Tech, described as "A local attacker may gain access to an encrypted APFS volume." If a hint was set within Disk Utility during the creation of an APFS encrypted volume, it was noted that the password was stored as the hint.
Apple addressed this issue by clearing the hint storage if it was discovered the hint was the same as the password. Apple also claims to have improved "the logic for storing hints."
The other reportedly fixed security issue involved an application that had the ability to extract passwords from the keychain. Patrick Wardle of Synack discovered the vulnerability in late September, creating a concept app to demonstrate how the attack could work.
The concept app had the capability to pull website logins from the Keychain, so long as the user was logged in, with the vulnerability itself not requiring root access in order to be exploited, though still requiring users to run it while deliberately overriding macOS security settings and unsigned software warnings.
According to Apple's description of the flaw, the method bypassed the keychain access prompt with a "synthetic click," and was addressed by "requiring the user password when prompting for keychain access."
The free Supplemental Update also includes a fix for a cursor graphic bug when using Adobe InDesign and resolved an issue where email messages couldn't be deleted from Yahoo accounts in Mail, as well as improving installer robustness.
Notably, the Supplemental Update did not include sufficient enough changes for Apple to issue it with a point-zero-one distinction. The company is still working on a macOS 10.13.1 update for High Sierra, with the first beta issued to developers last week.
 Malcolm Owen
Malcolm Owen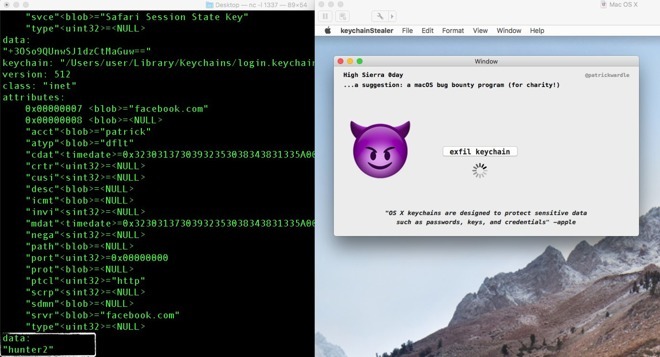













 Charles Martin
Charles Martin



 Andrew O'Hara
Andrew O'Hara

 William Gallagher
William Gallagher








8 Comments
Good stuff, but still a little clumsy for the support people to deal with customers who call with a problem with High Sierra Version 10.13. Ugh, which 10.13? The About This Mac dialog doesn't display a build number or "supplemental" tag so they'll have to go rooting around in the App Store update history. Not a big deal but still not very Apple-like. The good thing is that they plugged a couple of holes that seriously needed to be plugged.
Was this update rolled out to the beta testers of 10.13.1, either separately or integral to 10.13.1 beta?
The supplemental updates toasted my work Touchbar Macbook Pro. I spent about five hours troubleshooting. I couldn't open a terminal because my .bash_profile (which uses git to give me the branch i'm currently on in the prompt) would lock it up before I'd get a prompt. I couldn't figure out why my terminal wasn't working. I uncovered a few odd issues along the way.
1) Single usermode fsck -fy does not seem to work any more
2) Disk Utility disk first aid will lock up the entire computer (minus mouse movement) until it is done. I didn't know this until I let it go. It does say it locks up the drive, but didn't explicitly explain it was going to lock up usage of the computer.
3) mdfworker threads were going crazy and I was getting about 800 messages a second in my Console.
4) McAfee is not liked by 10.13
Xcode was the cause of my issues and I'm not sure why. When I could get Xcode 9 to open, it wouldn't ever finish building, it would just lock up during the middle of a build. Even after cleaning build folder and derived data. This was also related to my Terminal lock up. Once I was able to get rid of my .bash_profile, I was able to see my git command was broken with a `git --version`. I would have to ctl-c out of it. Using `xcode-select --reset` fixed it momentarily. I ended up having to go to Xcode 9.1 beta to fix it. Still at a loss why, but my confidence in APFS is shaken right now.