The 20-page report (PDF), titled simply "iOS Security," was picked up by MacNN after it was discovered on Apple's website.
"Apple designed the iOS platform with security at its core," the paper begins. It appears to have been written to help convince enterprise customers that iOS is secure enough for their needs.
According to the company, iOS devices include "low-level and firmware features" to protect against malicious software and "high-level OS features" that "allow secure access to personal information and corporate data, prevent unauthorized use, and help thwart attacks."
Subsections of the report include discussions of system architecture, encryption and data protection, network security and device access.
With respect to system architecture, Apple highlighted the secure boot chain that takes place on iOS devices. It also detailed the DFU (device firmware upgrade) recovery mode.
A visual overview of iOS security features
"When an iOS device is turned on, its application processor immediately executes code from read-only memory known as the Boot ROM. This immutable code is laid down during chip fabrication, and is implicitly trusted," the paper said.
Other architecture-level security features include system software personalization, which prevents downgrading of iOS devices to older versions; app code signing, which prevents unsigned code from being run and runtime process security, which includes "sandboxing" and entitlements.
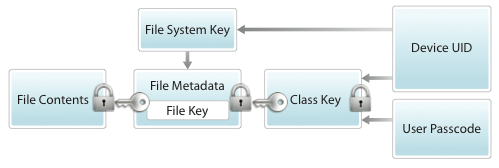
As for encryption and data protection, Apple touted the cryptographic hardware engines in iOS and the security features surrounding device Unique IDs and Group IDs. The company also described its "Data Protection" feature that keeps data locked while still allowing iOS devices to receive calls and notifications.
Apple also pointed to several features in iOS meant to provide enhanced network security on its devices.
"iOS uses—and provides developer access to—standard networking protocols for authenticated, authorized, and encrypted communications," the report read. "iOS provides proven technologies and the latest standards to accomplish these security objectives for both Wi-Fi and cellular data network connections."
A final subsection on device access provides information for enterprise administrators on setting up configurations, mobile device management (MDM) and device restrictions.
Apple also revealed that it maintains a "dedicated security team to support all Apple products." That team performs "security auditing and testing" of in-development and released products, provides "security tools and training" and "actively monitors" for new threats.
"Each component of the iOS security platform, from hardware to encryption to device access, provides organizations with the resources they need to build enterprise-grade security solutions. The sum of these parts gives iOS its industry-leading security features, without making the device difficult or cumbersome to use," the report's conclusion noted.
Apple has made inroads into the enterprise with its iPhone and iPad, but it has also faced some CIO hesitation over security concerns. For instance, IBM recently banned the Siri voice assistant feature from its internal networks because Siri must contact an external network to provide answers to queries.
 Josh Ong
Josh Ong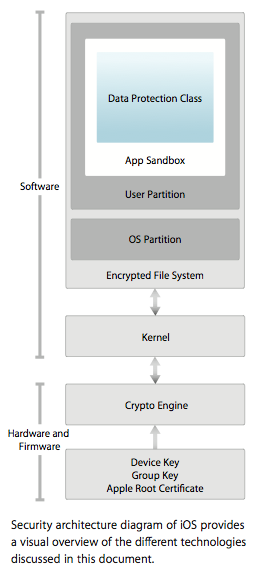







-m.jpg)






 Amber Neely
Amber Neely

 Wesley Hilliard
Wesley Hilliard
 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher











11 Comments
So where does Jailbreaking fit into this nifty diagram? Head in the sand from Apple and, although I haven't read it, the report would be more credible if it explained the limits of Jailbreaking. Maybe they can't acknowledge it because it shatters their security model.
So where does Jailbreaking fit into this nifty diagram? Head in the sand from Apple and, although I haven't read it, the report would be more credible if it explained the limits of Jailbreaking. Maybe they can't acknowledge it because it shatters their security model.
This is a great presentation for IT managers to make to their executives, but there is a little understanding that Apple is just helping them to blow a little wind up their skirts because they know the phones can still be jailbroken. No public system can ever be made foolproof.
Also, please correct me if I'm wrong, but there doesn't seem to be a reliable way for a company to detect a jailbroken phone on its own network—with one possible exception of an automated ssh probe using root/alpine (if it works, map the IP/MAC back to the registered user and send them a nasty email).
[quote name="Shawn Richards" url="/t/150481/apple-details-ios-security-with-new-guide#post_2120938"]So where does Jailbreaking fit into this nifty diagram? Head in the sand from Apple and, although I haven't read it, the report would be more credible if it explained the limits of Jailbreaking. Maybe they can't acknowledge it because it shatters their security model.[/quote] Apple's security is their draconian App Store which is either good or bad depending on how you look at it. The OS itself isn't particularly secure when stuff like JailbreakMe can exist to hack your iDevice and install third-party software via Safari. Apple users were lucky nobody crafted malicious webpages to brick the device. Apple's solution within the past year seems to have to been to hire the developers of the jailbreaking community.
This isn't about jail breaking, is it? This is to convince corporations and people that--if you [B]don't jailbreak[/B] your device--it will remain secure and virus free. All bets are off if you jailbreak.