Chinese PC maker Lenovo has found itself in the middle of a public relations disaster, following revelations that it sold a number of notebook computers with pre-installed software that hijacks users' browser sessions to inject customized advertisements and seriously degrades the security of encrypted connections.
The adware, from a visual search firm named Superfish, is a contextual search platform that has been shown to act as a transparent proxy for requests flowing through browsers on Lenovo machines. It analyzes the content of websites, inserting advertisements that it considers relevant.
In order to access HTTPS requests, Superfish also comes loaded with a self-signed root certificate. Pages loaded over HTTPS are signed with this certificate, rather than the actual certificate of the site owner, allowing Superfish to decrypt the contents.
This creates a serious security problem. Anyone with the encryption password for the certificate — which was easily found by Robert Graham of Errata Security — can extract the private key and perform a man in the middle attack to intercept the communications of any computer with the certificate installed, or to craft legitimate-seeming fake phishing websites.
In a statement, Lenovo acknowledged that it had installed Superfish on "some consumer notebook products shipped in a short window between September and December." The company promised that the backend services powering the ad injection technology have been disabled, and that it would not include Superfish on any future products.
Unfortunately, that does nothing to alleviate the security concerns caused by allowing the installation of a self-signed root certificate in the first place. Despite the clear implications, Lenovo does not appear worried.
"We have thoroughly investigated this technology and do not find any evidence to substantiate security concerns," the company said in the same statement.
 Sam Oliver
Sam Oliver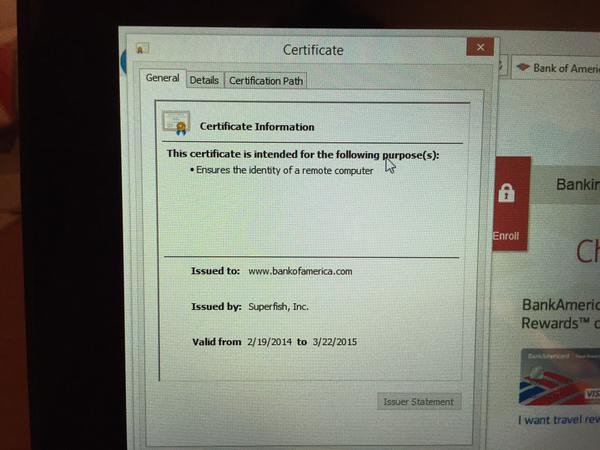






 Marko Zivkovic
Marko Zivkovic
 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher
 Andrew Orr
Andrew Orr
 Amber Neely
Amber Neely










46 Comments
So...don't trust Red China companies. Got it.
The company promised that the backend services powering the ad injection technology have been disabled, and that it would not include Superfish on any future products.
Google: "Dang. Can we buy Superfish? We need to inject ads wherever we can."
If Apple were caught doing this, it would be sued into oblivion. And the rhetoric coming out from the Chinese government about US tech spying on them? Well, I guess it's okay for China to do it. Hypocrisy. There should be a class-action lawsuit against Lenovo NOW!
Questionable default software has been common practice among PC makers for years. Dell, Gateway, HP, Sony....everyone of them have done similar things to the point that most people that are concerned with security immediate wipe a new PC and load a clean version of windows from a source other than the recovery media/partition. This is barely news.
[quote name="woodycurmudgeon" url="/t/184871/lenovo-bundled-adware-on-some-laptops-leaves-users-with-staggering-security-vulnerabilities#post_2678658"]Questionable default software has been common practice among PC makers for years. Dell, Gateway, HP, Sony....everyone of them have done similar things to the point that most people that are concerned with security immediate wipe a new PC and load a clean version of windows from a source other than the recovery media/partition. This is barely news.[/quote] Mostly true. People who are concerned about security, don't buy Dell, HP, Toshiba, etc in the first place and build their own equipment. Unfortunately that is not an option for laptops. For laptops getting a "naked" system is generally impossible, but the "it violates the letter of the license but not the spirit of it" work-around is to use a vanilla OEM version of the operating system from a desktop, but still use the key that belongs to the laptop. But generally people who are concerned about security or privacy are the same people who deal with questionable software (pirated software, malware, etc) as part of their job or hobby in the first place. The average person who buys a name-brand system shouldn't have to do all this just to get a working system.