Apple engineer Ivan Krstić spoke on far more than Apple's new bug bounty program at the Black Hat security conference, and delved into the inner workings of iOS hardware and software security features both in iOS 9 and the forthcoming iOS 10.
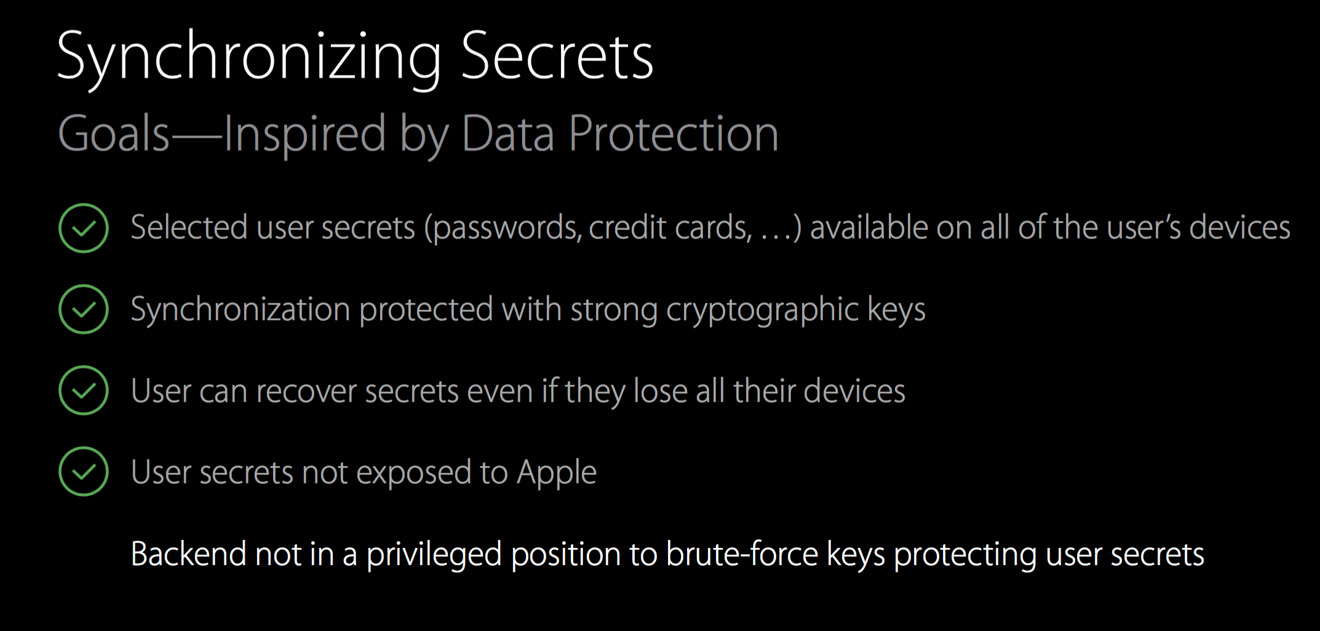
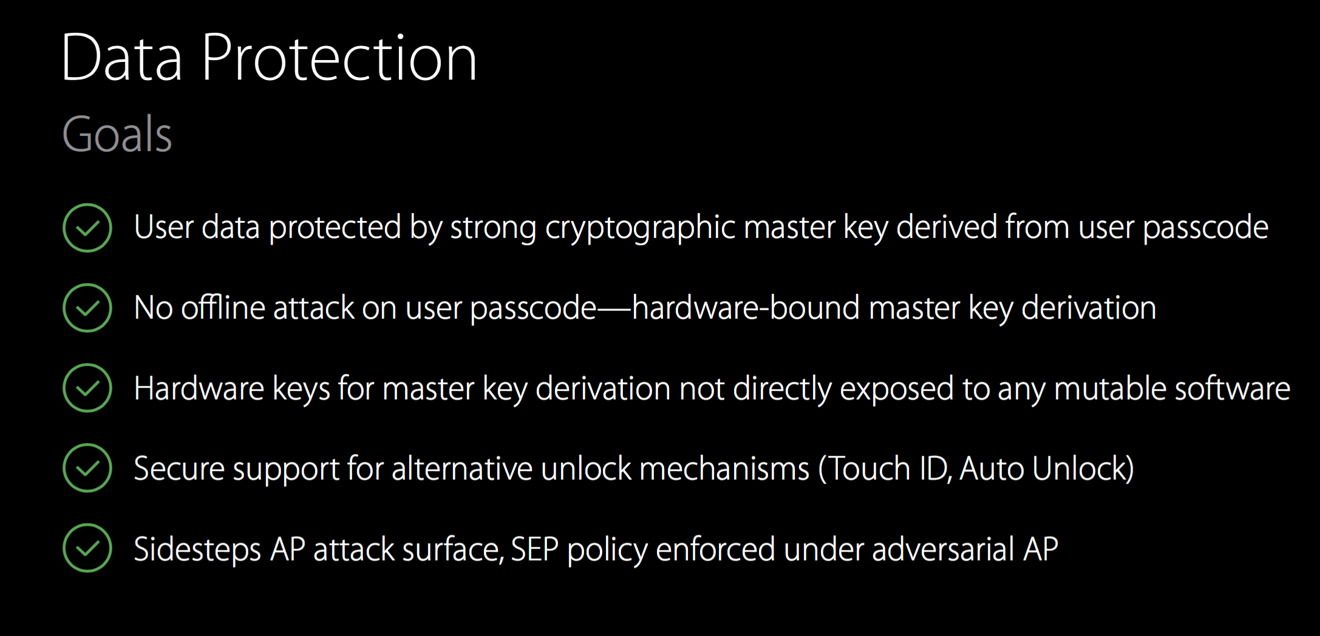
Krstić spoke at length about Apple's Secure Enclave Processor (SEP). The SEP is "protected by a strong cryptographic master key from the user's passcode," said Krstić, adding that "offline attack is not possible" even when the main processor has been compromised.
"On first initialization [the SEP] uses a true random number generator to create a unique device key within the processor," said Krstić. "It's not exportable, and it's stored in immutable secure ROM."
Specific topics detailing the SEP covered at the talk included the "update later" mechanism, various types of permanent and ephemeral security keys, decryption of individual files while keeping the core of iOS safe, and how Touch ID unlocks a device while at the same time keeping the device's master encryption key not visible to an attack at any time.
Safari on iOS is protected by "Hardened WebKit JIT Mapping." Rather than compiling JavaScript code in advance, such as found on the Amazon Kindle and similar devices, Apple guarantees rapid JavaScript execution by compiling it "just in time" (JIT) before execution. However, JIT compiling also requires less stringent code-signing, potentially opening up a hole in security.
Apple has skirted JIT security issues by dedicating certain areas of application memory for certain tasks. JavaScript execution in iOS 9 and earlier is prevented from running code in memory designated as raw data storage — a common vector of attack. Additionally, in iOS 10, compiled JavaScript code cannot be changed once it is running and in execution-specific memory, preventing on-the-fly alterations of code, also frequently used in attacks.
Regarding Apple's overall encryption services, Krstić detailed the construction process, which at one point has "admin cards" stored in in tamper-proof bags stored in separate physical safes prior to the launch of the keyed server bank. After the server bank is launched to provide encrypted data transmission services to users, the admin cards are destroyed, preventing manipulation of the back-end by any party for any reason, including Apple.
Should Apple have to update the encrypted server bank in any way, there is no way to do an "on the fly" update to the servers. Instead, the company must commission new encryption servers, take the old ones off-line, and update consumer devices accordingly.
Addressing the newly announced Auto Unlock feature that allows the Apple Watch to unlock a nearby Mac, Krstić addressed Apple's unique approach to the problem. In similar products, Krstić noted that account providers have access to user data, and some encryption keys. In Apple's approach, the authentication process and generated cryptography are local to the devices, and not handled by Apple server infrastructure.
Krstić was the named the director of security architecture for the "One Laptop per Child" initiative in 2006. He joined Apple in 2009, and is currently the head of Apple security engineering and architecture.
The Black Hat talk by Krstić on August 4 addressed "cryptographic design and implementation of our novel secure synchronization fabric" as it relates to technology like Auto Unlock, HomeKit, Unlock, iCloud Keychain, and iOS Safari. Training at the Black Hat conferences are made by various computer security vendors, with keynote speeches given by notable members of the community, such as former directors of the U.S. National Security Agency, or Homeland Security officials.
Also announced by Krstić, security researchers invited by Apple can now hand over working exploits for cash rewards. Apple has refrained from such offers in the past. Security researchers who give awards to charity will be matched by Apple.
Apple's iOS 10 is currently on its fourth developer beta, and is expected alongside macOS Sierra in the fall.
 Mike Wuerthele
Mike Wuerthele






-m.jpg)






 Christine McKee
Christine McKee
 Malcolm Owen
Malcolm Owen
 Chip Loder
Chip Loder
 Marko Zivkovic
Marko Zivkovic
 Wesley Hilliard
Wesley Hilliard










13 Comments
He was a great hire for Apple, one of the world's top security researchers. Kudos to Apple for their security efforts.
That picture though