The recently-discovered Group FaceTime bug that allowed people to eavesdrop on other people without their permission has been worked around, and a fix is coming, but the UK's surveillance agency wants to use flaws like it as a feature, in order to more easily spy on targets.
Revealed on Monday, the Group FaceTime exploit can be used to allow audio, or even video, to stream from a target's iPhone or Mac, before a call has been accepted. The bug has prompted Apple to disable Group FaceTime as it works for a fix, and has already spawned multiple lawsuits over the potential privacy breach.
While critics are seeing it as an issue, government surveillance agencies are seeing it as an opportunity.
According to the American Civil Liberties Union (ACLU), the United Kingdom's Government Communications Headquarters (GCHQ) made a proposal for agents to be able to add unseen participants to secure messaging services communications, under what is named the "Ghost Proposal."
Produced by GCHQ officials Ian Levy and Crispin Robinson, the proposal involves institutionalizing the process of making an "untrustworthy user interface" to enable spying. In short, forcing services to allow such surveillance activities to take place.
"It's relatively easy for a service provider to silently add a law enforcement participant to a group chat or call," advises the proposal. "The service provider usually controls the identity system and so really decides who's who and which devices are involved - they're usually involved in introducing the parties to a chat or call."
It is suggested this would involve the service provider "suppressing a notification on a target's device." In effect, this means making Apple allow for a third contact to join a FaceTime call, but without the existing participants being made aware of the extra party.
The authors believe the Ghost Proposal would provide the ability to "wiretap" communications in secure messaging apps, and by doing so, "you don't even have to touch the encryption."
"It's very difficult to engineer software correctly in the first place, and it's even more difficult to design it with intentional flaws, however limited," advises the ACLU. "If a mechanism exists to deliberately make the user interface untrustworthy, it will be an attractive target for malicious hackers and other hostile actors. Who will be responsible for its inevitable abuse?"
The use of encryption in calls and messaging services does prevent government surveillance from listening in, and has caused major issues for law enforcement agencies trying to spy on persons of interest. As defeating the encryption has been practically impossible for some time, governments and law enforcement agencies have called for the introduction of backdoors to break the cryptography or other workarounds, in the name of protecting the public.
In one such attack on encryption in November, U.S. Deputy Attorney General Rod Rosenstein claimed "we cannot accept a culture in which technology companies considers it part of their responsibility to defeat legitimate law enforcement." However, in the same speech, he also called for increased protections of consumers, suggesting "We need to place security on the same footing as novelty and convenience, and design technology accordingly."
 Malcolm Owen
Malcolm Owen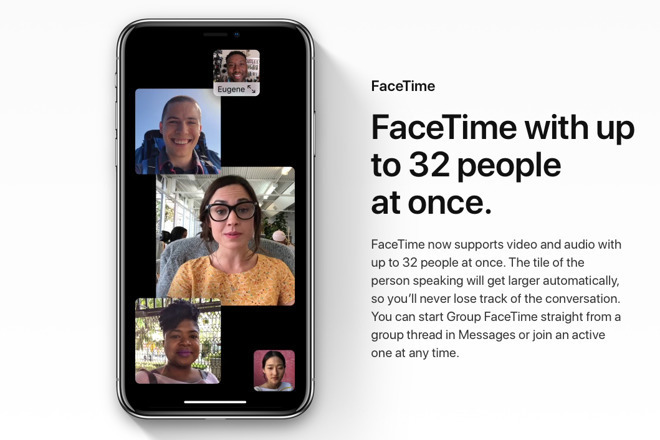







-m.jpg)






 Christine McKee
Christine McKee

 Sponsored Content
Sponsored Content

 Amber Neely
Amber Neely











7 Comments
And people wonder why I don't trust governments.
The security of people is important. Full stop. GCHQ should learn to spy through normal means.
I believe the city of Washington DC is subsidizing installation of residential surveillance cameras and/ or doorbells if users allow outside access to law enforcement. Skimmed perspective piece in yesterday’s Washington Post.