Security researchers at antivirus firm Intego have discovered a new Mac malware in the wild that tricks users into bypassing modern macOS app security protections.
In macOS Catalina, Apple introduced new app notarization requirements. The features, baked in Gatekeeper, discourage users from opening unverified apps — requiring malware authors to get more creative with their tactics.
As an example, Intego researchers have discovered a new Trojan horse malware actively spreading in the wild via poisoned Google search results that tricks users into bypassing those protections themselves.
The malware is delivered as a .dmg disk image masquerading as an Adobe Flash installer. But once it's mounted on a user's machine, it displays instructions guiding users through the malicious installation process.
In a tactic described by Intego as "novel," the malware asks users to right-click and open the malware instead of double-clicking it. Per macOS Catalina Gatekeeper settings, this displays a dialogue box that has an "Open" button. Normally, when clicking an unverified file, Apple doesn't allow users to open them so conveniently.
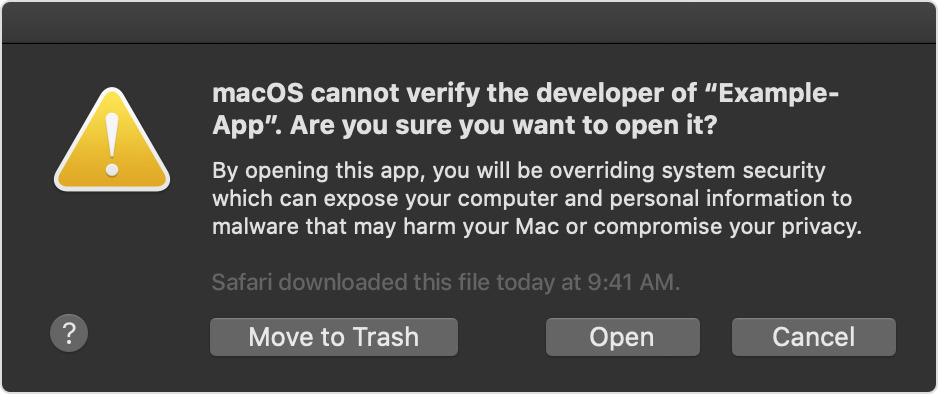 Right-clicking and opening a file allows users to run unverified software more easily. Credit: Intego
Right-clicking and opening a file allows users to run unverified software more easily. Credit: IntegoNormally, macOS discourages users from opening unverified apps by making the process more difficult. Specifically, forcing users to head into System Preferences to override Gatekeeper. The strategy also saves bad actors from signing up for an Apple Developer account or hijacking an existing one.
Once users actually open the installer app, it runs a bash shell script and extracts a password-protected .zip file that contains a more traditional malicious app bundle. Although it initially installs a legitimate version of Flash, Intego notes that it can also be used to download "any other Mac malware or adware package."
Interestingly, the malware has been spread via Google search results that redirect users to malicious webpages claiming that a browser's Flash Player is out of date. Intego added that the malware has, thus far, been able to avoid detection by most antivirus software.
The actual malicious portions of the malware are re-engineered variants of past macOS Trojans, such as Shlayer or Bundlore. Intego also spotted similar security-evading malware in 2019.
Who's at risk and how to avoid it
Even though Adobe Flash player will officially reach its end of life on Dec. 31, 2020, Intego notes that "outdated Flash" malware tends to be pretty successful. The aforementioned Shlayer Trojan, for example, infects about one in 10 Mac users.
Since the malware is actively spreading via Google search results, the risk for compromise is a bit higher. Intego notes that it appears when users search for the exact titles of YouTube videos.
Users can avoid this malware by only clicking on links that they absolutely trust. If any website asks you to download something unsolicited, get out of there.
Indicators of compromise can include the following apps: flashInstaller.dmv in Downloads; a FlashInstaller.zip file or a file named "Installer" in a subfolder in private/var/folders.
Intego notes that several domains — including youdontcare.com, display.monster, yougotupdated.com and installerapi.com — have been associated with this campaign. Any traffic to or from these domains "should be considered a possible sign of an infection," the researchers said.
 Mike Peterson
Mike Peterson







-m.jpg)






 Christine McKee
Christine McKee
 Marko Zivkovic
Marko Zivkovic
 Mike Wuerthele
Mike Wuerthele

 Amber Neely
Amber Neely
 Sponsored Content
Sponsored Content
 Wesley Hilliard
Wesley Hilliard










15 Comments
I should be fine. Don't use Google search and will never install Flash ever again. Apple should treat anything related to Flash as malware, especially since it has always been the easiest way to infect Macs (outside Word malware). I know there are people who still use and develop in Flash but let's move on.
Which is worse, a real Flash installer or a fake one? It's a toss-up.
Just say no to Flash has been the watchword for years. Fortunately, Flash will be saying no to us all at the end of the year, as Adobe closes it down.
Meanwhile, if you use some kind of legacy service that requires Flash, stop!
I am old enough to remember — can’t believe it was over 13 years ago! — SJ saying Flash was crap, and taking so much heat for it.
Wait. Who’s still using Flash on websites? I haven’t been to Fat-Pie or Home Star Runner in years and I think they just publish videos now anyway. I’m sure it’s still great to have as an animation tool, but not as a browser plugin or web feature.