A new Bluetooth vulnerability could allow an attacker to downgrade or bypass Bluetooth encryption keys, opening the door to man-in-the-middle attacks or other types of malicious exploits.
The flaw, dubbed "BLURtooth," resides in a component of the Cross-Transport Key Derivation standard and leaves devices vulnerable to man-in-the-middle attacks or other exploits. It affects all "dual-mode" devices running Bluetooth 4.0 or 5.0, which includes the iPad Pro to the iPhone 11.
According to a security notice by the Bluetooth Special Interest Group (SIG), researchers at Purdue University and the Ecole Polytechnique Federale de Lausanne discovered that CTKD may permit escalation of access between two devices.
The CTKD component is used to negotiate authenticate keys when pairing two Bluetooth devices together, and works by implementing two different sets of keys for the Bluetooth Low Energy or Basic Rate/Enhanced Data Rate standards.
However, the researchers discovered that an attack could leverage CTKD to overwrite other Bluetooth keys — granting them access to other Bluetooth-capable apps or services on an affected device. The SIG notes that the vulnerability can be used to overwrite keys completely, or force a downgrade to keys that use weaker encryption.
"This may permit a Man In The Middle (MITM) attack between devices previously bonded using authenticated pairing when those peer devices are both vulnerable," the SIG wrote.
Attackers may also be able to spoof the identity of a paired device to gain access to authenticated services
In theory, attacks like these could lead to theft of data or other malicious activity. But it isn't clear whether device-level restrictions or security features could mitigate the risks.
Who's at risk from BLURtooth
At this point, there's no given timeline for a patch. Because of that, the only real way to mitigate it on affected devices could be to pay close attention to which Bluetooth devices your device is connected to.
Apple's iOS security features may provide some level of protection. Apple also requires apps to obtain permission from users before they connect to a service or accessory using Bluetooth. App sandboxing should prevent a compromised service from accessing data in other apps.
Additionally, the SIG notes that there's a mechanism that can be deployed in the updated Bluetooth 5.1 standard to mitigate the attack. Because of that, devices running Bluetooth 5.1 should be considered safe.
 Mike Peterson
Mike Peterson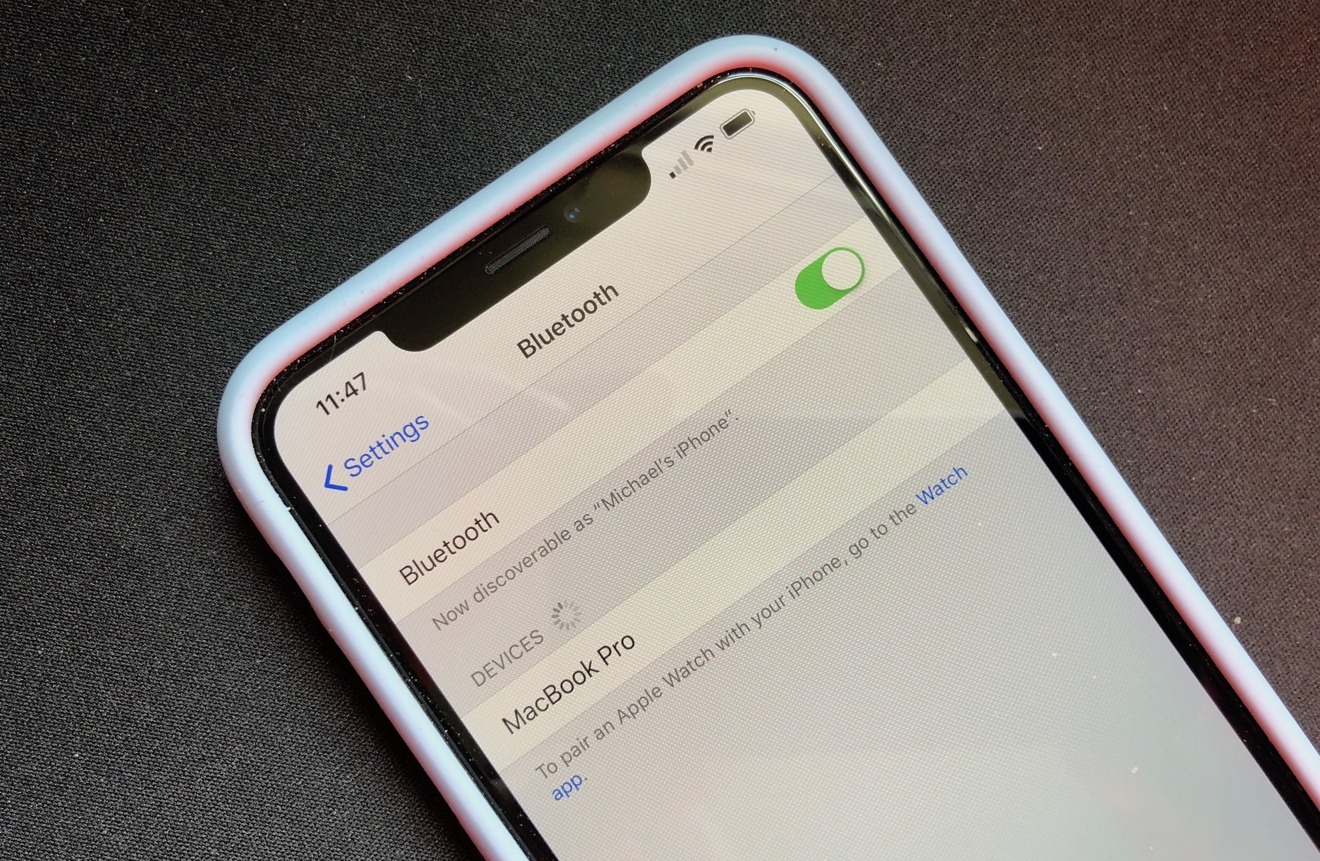

-m.jpg)






 Marko Zivkovic
Marko Zivkovic
 Mike Wuerthele
Mike Wuerthele
 Christine McKee
Christine McKee
 Amber Neely
Amber Neely
 Wesley Hilliard
Wesley Hilliard

 William Gallagher
William Gallagher









2 Comments
This is not a new vulnerability, it has always been there. It is a newly discovered vulnerability.
I typically just keep BT off unless I'm using a keyboard or playing a game (controller).