The online world is still a dangerous place, but while antivirus providers are trying to sell you subscriptions for their wares, macOS is still secure enough for users to resist the products. The best antivirus for Mac is a combo of existing protections and user sanity.
Viruses and malware are a fact of online life, with numerous reports detailing how various digital nasties are badly affecting systems around the world. Both for individuals and for organizations with more stringent security practices.
On Windows, having some form of additional protection was, and still is, needed, especially as it's the biggest target for virus makers to aim for. With a smaller user base, Mac was less of a target at first, but it has become a bigger one as the years rolled on.
What helped the Mac was its reputation as being very immune to malware and viruses in general. That it was virus-proof in some way, and you didn't need an antivirus tool at all.
That is still pretty much true today, to a point. Apple includes various mechanisms in macOS that makes it very difficult for malware to actually be a problem for the typical user.
This hasn't stopped various companies from trying to provide extra security, declaring themselves to be the best antivirus for Mac in some way.
To be sure, it is still a target of viruses and malware, but certainly not in a way that Windows users have to be concerned about. While some of it is down to users being careful and thinking about how they act online, a lot of it is still down to the protection systems macOS has in place.
That reputation of security exists for good reason. Here's why.
Gatekeeper
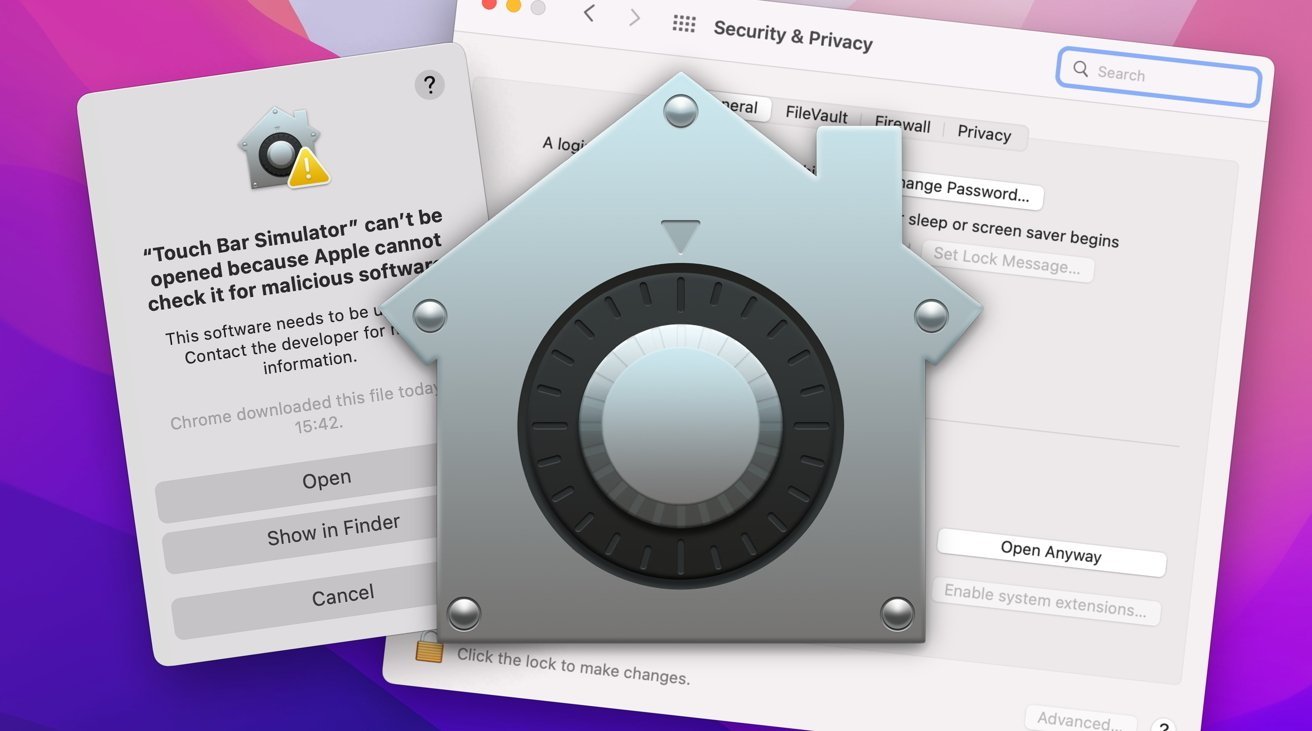
Of all of the protections Apple has in macOS, Gatekeeper is the most visible one to users. You'll know it as the warning that flags up whenever you download a piece of software from the Internet and try to run it.
Gatekeeper is capable of stopping malware from being run on a Mac, by placing multiple obstacles in the way that the user themselves need to work around.
Rather than outright scanning for malicious code, Gatekeeper instead acts as a nightclub bouncer, making sure that the software has the right authorization to run.
Gatekeeper verifies a downloaded app before running it for the first time, ensuring it has either been sourced from the Mac App Store, or that it has a valid Developer ID and has been notarized by Apple.
If it's from the Mac App Store, the app therefore has already gone through various checks via Apple itself, so Gatekeeper rightfully assumes that there's little wrong with it, and allows the app to run.
When it comes from other sources, that's where more checks come into play.
The Developer ID is provided to the developer as an indicator they are a trusted creator of the app in the first place. The application of the certificate to the app is a way to ensure that it is from that specific developer without any changes made to it.
The notarization part involves developers providing apps to an automated notary service operated by Apple, which checks to make sure the app is safe to run.
Think of notarization as the equivalent of Apple performing some checks to make sure the app is OK and handing it back to the developer with a mark to denote that this particular executable is fine.
Apps with a valid Developer ID and notarized are allowed by Gatekeeper to run, and therefore is trusted by macOS.
If an app package is interfered with by a malicious third-party actor, then that could affect either or both the Developer ID certificate or notarization security. In such cases, Gatekeeper would see an issue, and stop the app from running.
The problem is that it is still possible for users to run apps that aren't notarized by Apple on a Mac, or can see the warnings issued by Gatekeeper and press on to get the app running regardless. It's not difficult to get around such Gatekeeper notices.
Sadly, this does give viruses and malware a chance to exist on macOS that would otherwise be thwarted by Gatekeeper at the first instance.
That said, Gatekeeper's protection has drawn the attention of virus producers, as if they can thwart that system, they have a leg up in infecting the Mac. There have been some occasional issues cropping up, but Apple does work to fix them as soon as they surface.
Other than these rare occasions, Gatekeeper has been fairly resilient and a very useful tool in the Mac security arsenal. At least as far as its powers stretch.
Gatekeeper can do a lot of the heavy lifting of keeping a Mac secure. It just can't cover every eventuality.
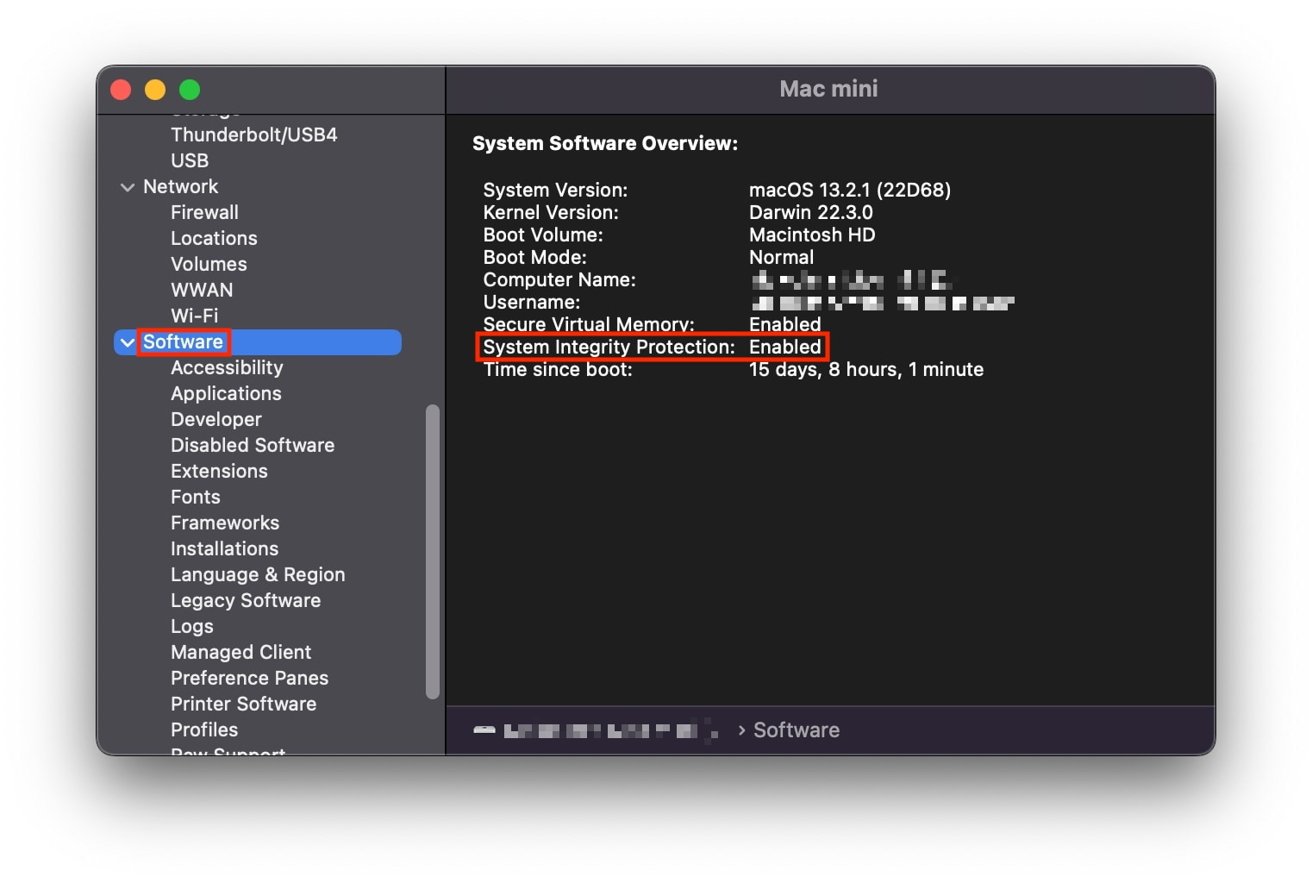
System Integrity Protection
System Integrity Protection (SiP) is another mechanism that comes into play, that limits how an application can run on a Mac.
Specifically, it stops malicious software from making changes to certain protected folders and files on the Mac. By restricting the root user account, the main one that has free administrative reign, SiP can help limit the damage caused by malware working as if they are a root user.
Before OS X El Capitan, applications installed using an administrator's username and password were given root-level access, with no limitations at all. A malicious app with such rights would be able to affect important areas of the Mac's operating system, and with nothing to stop it.
SiP protects a series of highly important areas of macOS, including the System folder, usr, bin, sbin, var, and applications preinstalled as part of macOS itself.
At the same time, SiP also allows third-party apps to write to the Applications, Library, and usr/local folders, which are typical areas a legitimate app will need to access.
As part of these protections, SiP will still allow for modifications to protected folders and files, but only under processes that Apple itself has signed, and that also have specific entitlements enabling such activity. For example, Apple's own software updates and installers are typically allowed to make changes through SiP.
Just as there are occasional gaps in Gatekeeper's security history, there are minor blips in SiP, such as an October 2021 flaw that allowed Apple-notarized app install packages to perform activities normally barred by SiP.
Again, Apple worked quickly to patch the issue before it became a real problem.
Apple Silicon
Another thing that Apple's hardware manages to do right is the hardware itself. Apple's shift away from Intel provided more than just performance benefits and more control over the entire system.
It also means Apple's systems aren't affected by the same chip issues that can plague Intel-based computers.
Take the example of Meltdown and Spectre, which were exploits that preyed on vulnerabilities in Intel chips. Apple computers that also used Intel chips were affected by the same vulnerabilities, and so had to undergo various fixes.
 Apple Silicon can avoid Intel chip vulnerability issues, but Apple still has to deal with any issues in its chip designs.
Apple Silicon can avoid Intel chip vulnerability issues, but Apple still has to deal with any issues in its chip designs. With the switch to Apple Silicon, the Mac is no longer affected by the same processor-based vulnerabilities that Intel had to deal with, simply because of using different designs.
This isn't entirely a change that absolves Apple from having to deal with any chip issues whatsoever. Researchers have already found their own issues with Apple Silicon.
The key here is that it's hardware problems that Apple itself can fix and manage for itself, without having to lean on Intel to come up with a patch. And also hardware problems that aren't caused by third-party decisions, only Apple's own.
The best antivirus for Mac is user awareness
The problem with security features such as SIP and Gatekeeper is that they can provide protection as far as they are allowed to go. If a user thinks they know better, it's possible for a user to get around the restrictions, and potentially allow malware to run unimpeded.
It's not just in macOS, but pretty much everywhere. While every protective feature can be made available, an uncaring user may do everything in their power to thwart those very systems.
For example, a well-secured Windows system with antivirus and a firewall could be well protected. Except the user could still turn off both the antivirus and firewall if they want, leaving their PC vulnerable.
You could put a sandwich into an office fridge, in a rigid container wrapped in multiple layers of duct tape and with multiple notes declaring it is your sandwich and not to steal it. But you know deep down that the office thief will still be eating your sub anyway.
The best antivirus for Mac may well be the user themselves, as if they can remember to act with care surrounding things they download from the Internet, they should do fine.
For example, it makes sense to only download applications from sources that you trust. This could be the developer, a well-established marketplace, or even better, the Mac App Store.
Then there's paying attention to Gatekeeper's warnings, as they should make you think twice about running the download in the first place.
And then there are the other obvious things, such as being mindful of what sites you visit, the links you click, and the information you provide online.
If you're vigilant, you can be fairly safe online with a Mac, without an antivirus installed.
This isn't to say that you shouldn't get an antivirus installed on your Mac. They can be a handy backup, as a cognitive safety net, and could catch things that do slip past Apple's own systems.
However, it's only if the user is careless in the first place. And even so, if they can get around Apple's protections, they'll get around any other anti-malware tools installed on a Mac too, even if it's securely locked down by enterprise security teams.
The best antivirus for Mac is not to be stupid in how you use it in the first place.
 Malcolm Owen
Malcolm Owen









 William Gallagher
William Gallagher


 Andrew O'Hara
Andrew O'Hara
 Chip Loder
Chip Loder