A study by Duo Labs looking at a series of name-brand PC makers revealed that their bundled software "is making us vulnerable and invading our privacy."
"Updaters are an obvious target for a network attacker, this is a no-brainer," wrote Duo Labs researcher Darren Kemp. "There have been plenty of attacks published against updaters and package management tools in the past, so we can expect OEM's to learn from this, right?
"Spoiler: we broke all of them."Every vendor shipped with a preinstalled updater that had at least one vulnerability resulting in arbitrary remote code execution as SYSTEM
Kemp noted that an analysis of Windows 10 notebooks from Acer, Asus, Dell, HP and Lenovo found that "every vendor shipped with a preinstalled updater that had at least one vulnerability resulting in arbitrary remote code execution as SYSTEM, allowing for a complete compromise of the affected machine."
He added, "the level of sophistication required to exploit most of the vulnerabilities we found is somewhere between that possessed by a coffee stain on the Duo lunch room floor and your average potted plant - meaning, trivial."
Even without third party partners adding their own poorly designed bloatware, Microsoft Windows 10 was discovered to continue to connect to Microsoft's servers and send unknown data, even after users activate data privacy settings.
Lenovo scrambles to save its sloppy security record
China's Lenovo— the largest producer of both Windows PCs and Android smartphones— responded to the report by issuing a security advisory that "recommends customers uninstall Lenovo Accelerator Application by going to the 'Apps and Features' application in Windows 10, selecting Lenovo Accelerator Application and clicking on 'Uninstall,'"
One of the components of the Lenovo Accelerator Application is UpdateAgent, which Duo Labs had called "one of the worst updaters" due to the fact that it pings Lenovo's servers for new updates every ten minutes.
Because there is "no verification or encryption protecting the transmission of updates, it's trivial for an attacker to insert malicious code," noted a report by ThreatPost.
Duo Labs researcher Mikhail Davidov noted of UpdateAgent, "It was unclear at the time of discovery what its legitimate use was for," adding that "Lenovo's decision to advise users to uninstall it manually seems strange to me, as an update can be pushed to all affected models to uninstall itself without requiring user interaction."
ThreatPost added, "These issues are not unique to Lenovo. All of the vendors' machines Duo Labs examined had similar flaws around a lack of encryption, privilege escalation and remote code execution vulnerabilities. Of those vendors who did encrypt the transmission of updates, for example, some were either poorly implemented or failed to include proper validation checks."
One year after Lenovo's Superfish scandal
Last year, Lenovo was discovered to have bundled Superfish adware on its notebook computers, software that was designed to hijacks users' browser sessions to inject customized advertisements but had a side effect of seriously degrading the security of encrypted connections.
To inject ads in pages involving encrypted HTTPS requests, Superfish loaded its own a self-signed root certificate on the Lenovo machines. Pages loaded over HTTPS are signed with this certificate, rather than the actual certificate of the site owner, allowing Superfish to decrypt the contents without the user knowing.
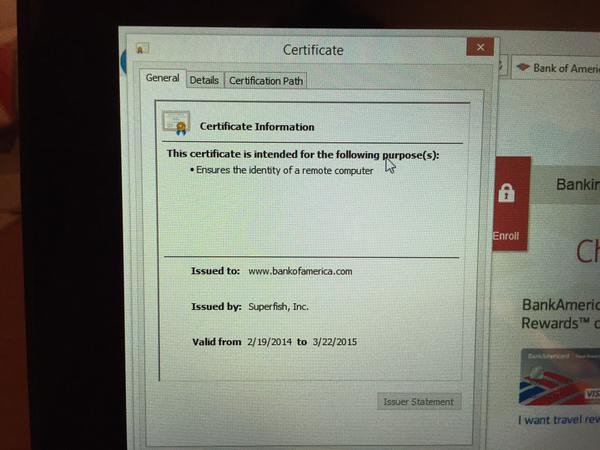
Bank of America's website being signed with a Superfish certificate, as noticed by Google security engineer Chris Palmer
Lenovo responded by saying it would stop sending ads to Superfish-tained machines and stop installing Superfish on its new Windows PCs, but did nothing to solve the actual problem Superfish created for users.
The company effectively blew off the findings of researchers by claiming in a statement that it "thoroughly investigated this technology and do not find any evidence to substantiate security concerns."
Windows, like Android, endangered by hardware partner's malice or incompetence
The fact that top tier PC makers are all bundling their own poorly designed software with Windows, introducing easy to exploit security vulnerabilities, has a clear parallel on Android, where hardware vendors routinely bundle not just buggy software updaters but often even purposely disable the security configuration settings that protect devices from installing apps from malicious third-party sources and in some cases install security backdoors.
A 2014 study by Bluebox Labs tested a dozen Black Friday bargain Android tablets from major retailers including Amazon, Best Buy, Kmart, Kohl's, Staples, Target and Walmart and reported "shocking" security flaws, malware and active backdoors installed on the new devices.
These flaws are on top of issues that affect the Android OS itself, which have included vulnerabilities such as Masterkey, FakeID and Stagefright.
Security is a key issue for Apple
While Google's chairman Eric Schmidt boasted to the media in 2014 that "our systems are far more secure and encrypted than anyone else, including Apple," groups that take privacy and security seriously, like the Electronic Frontier Foundation, have recommended Apple's messaging products for their end-to-end encryption while cautioning that Google did not provide similar security for its users.
Last November, Chris Soghioan, the principal technologist for the American Civil Liberties Union, went even further to state that Apple's efforts to protect the privacy of its users, including end-to-end encryption of their communications, effectively separated its more affluent iOS users from the poor and disadvantaged forced to use Android.
"The security people I know at Google are embarrassed by Android," Soghioan noted.
"Apple is nearly unique of tech firms in it's high profile, has revenue that don't rely on compromising privacy... " https://t.co/F7IIlb4shL
— Jeremiah Grossman (@jeremiahg) February 17, 2016
Both Android devices and Windows PCs have a wide variety of over the counter spyware tools and privacy exploits that are easy for even amateurs to find, while even tools sold to law enforcement (including FinSpy, above, from global surveillance firm Gamma Group) note that they won't work on iPhones and other iOS devices unless their security has been jailbroken by the user.
Apple has doubled down on security and privacy as key features of its Mac and iOS platforms. Additionally, without any commercial interest in collecting user data for marketing purposes, Apple is in a unique position to defend user privacy and security.
Last summer, Apple introduced WebKit Content Blockers as a secure new App Extension to enable developers to create tools that filter out any web content, including display ads and user tracking.
The company is likely to outline further new initiatives in security and user privacy at its Worldwide Developer Conference to be held in San Francisco the week after next.
 Daniel Eran Dilger
Daniel Eran Dilger






-m.jpg)






 Malcolm Owen
Malcolm Owen
 Amber Neely
Amber Neely


 Christine McKee
Christine McKee

 Chip Loder
Chip Loder
 Marko Zivkovic
Marko Zivkovic









24 Comments
Doesn’t matter. Windows Rulz! Apple Suckz! Ask any neckbeard. Windows and Android rule the world. Apple is a has-been toy maker. I read this on the Internet.
Microsoft doesn't care about privacy, that's been proven over and over again over the past 20 years.
I'm proud to declare that I've never owned a PC laptop in my entire life, and you can bet your first born that I never will either.
I'm not the least bit surprised that there's plenty of bloatware and unwanted, dangerous crap inside.
I've always hated how PC laptops usually came with tons of stickers plastered on them. How ugly and disgusting is that? That right there is a deal breaker, and it just tells you all about the mentality of the companies releasing such machines, and nobody should be shocked that there is tons of unwanted crap on the inside too, and not just on the outside.