Billions of smartphones and other devices are vulnerable to the newly disclosed "BLESA" Bluetooth flaw, but Apple already issued an iOS patch for it in April 2020.
The vulnerability, dubbed Bluetooth Low Energy Spoofing Attack (BLESA), affects devices running the Bluetooth Low Energy (BLE) protocol — including smartphones, laptops, tablets, and IoT devices. Apple patched it, however, in iOS 13.4 and iPadOS 13.4.
First discovered by a research project at Purdue University, the vulnerability lies in the reconnection process of the BLE specification.
When two BLE devices have already paired and authenticate each other, the standard allows them to easily reconnect when they move out of and back into range of each other. In theory, the two devices should re-check each other's cryptographic keys during the reconnection process.
The researchers at Purdue found that the protocol contains a few weak links in its language. For one, authenticating during reconnection is optional and not mandatory. More than that, the authentication could be circumvented if it is applied.
As a result, an attacker could bypass reconnection authentication and spoof an existing BLE connection. That could allow a bad actor to intercept Bluetooth traffic, or carry out other malicious attacks.
Who is at risk for BLESA attack?
Based on BLE usage statistics, the researchers estimate that the number of vulnerable devices is in the billions.
Not all BLE stacks are affected by the vulnerability, however. Windows devices are immune, for example. Linux-based laptops and IoT devices are impacted, as are Android devices.
Apple's iOS is affected in versions before iOS 13.4. Researchers claimed to be unable to test the vulnerability in macOS, but it typically get the same mitigations that iOS does.
Users running an older version of iOS install the latest available update to prevent the exploit.
 Mike Peterson
Mike Peterson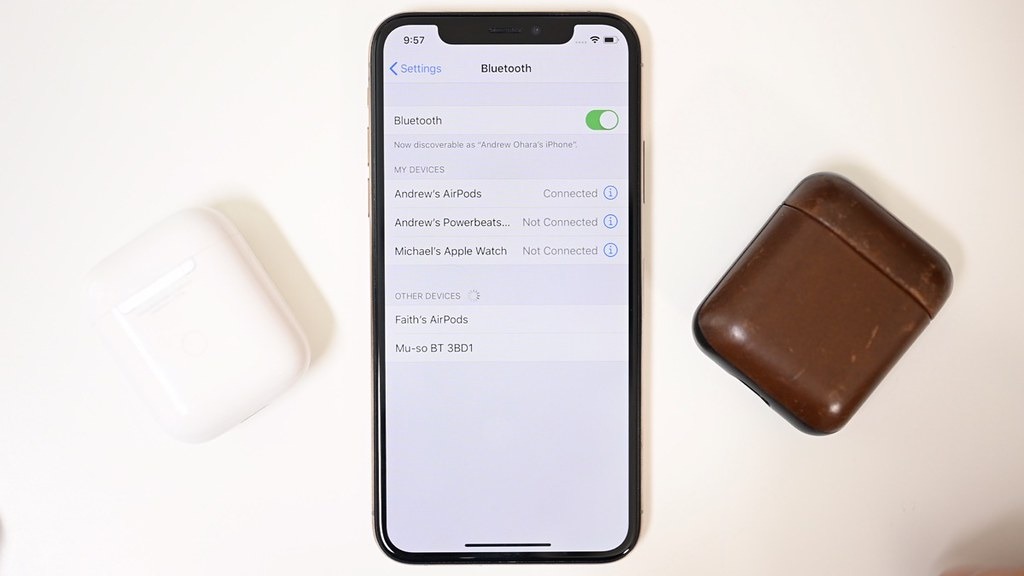








 AppleInsider Staff
AppleInsider Staff
 Chip Loder
Chip Loder
 Christine McKee
Christine McKee
 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher


 Andrew Orr
Andrew Orr






2 Comments
"We were recently advised by Google that the fix to an earlier CVE (2019-2225) [part of the December 2019 Android security updates] will mitigate BLESA. Due to time constraint, we have not independently verified its effectiveness against BLESA; but we will do so in the near future. We’d like to thank colleagues from Google for sharing this information."
So what would a practical real world attack look like?
Because this notion of waiting for two de ices to move away from each other then jumping in when they’re back in range sounds a bit theoretical to me.