Apple demoed technology at WWDC 2022 called Private Access Tokens — and they could potentially kill CAPTCHAs once and for all.
Private Access Tokens (PAT) can prove when an HTTP request is coming from a human instead of a bot. CAPTCHAs are the current form of authentication but it takes time for a human to complete one.
Known as the Completely Automated Public Turing test to tell Computers and Humans Apart, a CAPTCHA is an image or puzzle that appears on the web.
They start by clicking the "I'm not a robot" button. Distorted words, identifying objects in an image, or sliding a puzzle piece, these tools are an annoyance.
CAPTCHAs can also be compromised, such as being used to steal login information or come from a company that doesn't put privacy first.
PATs authenticate an HTTP request automatically in the background. Web users won't notice a thing, and cloud providers such as Cloudflare and Fastly are already incorporating the technology.
Authenticating people on the web
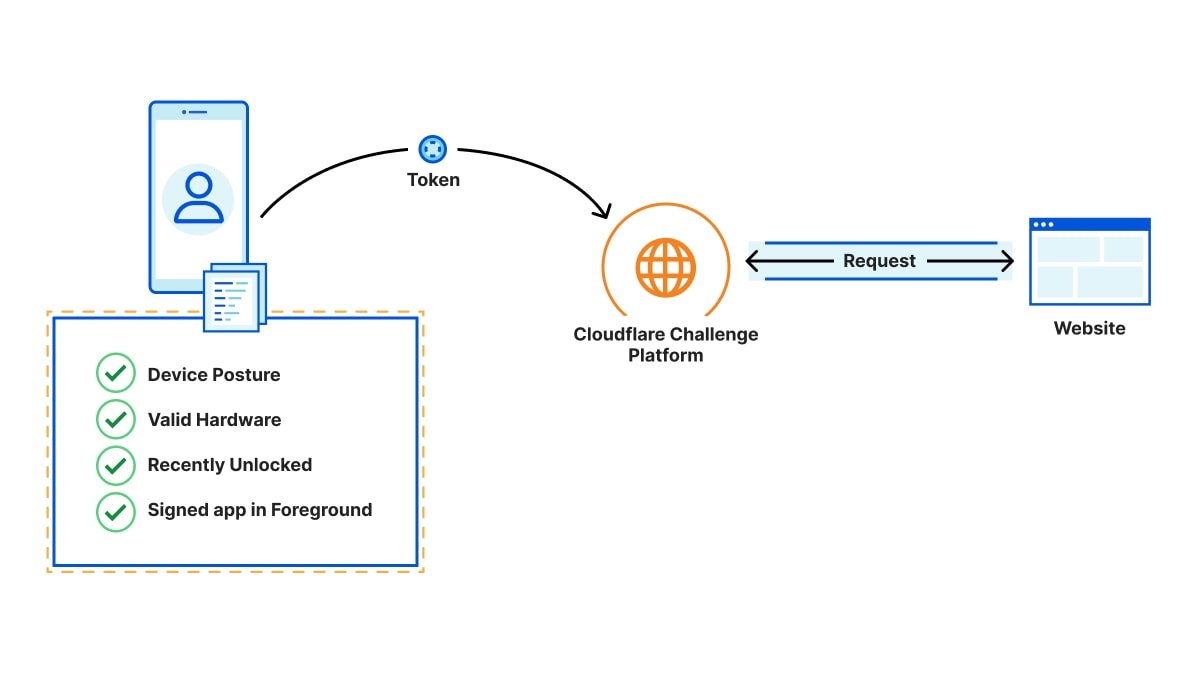
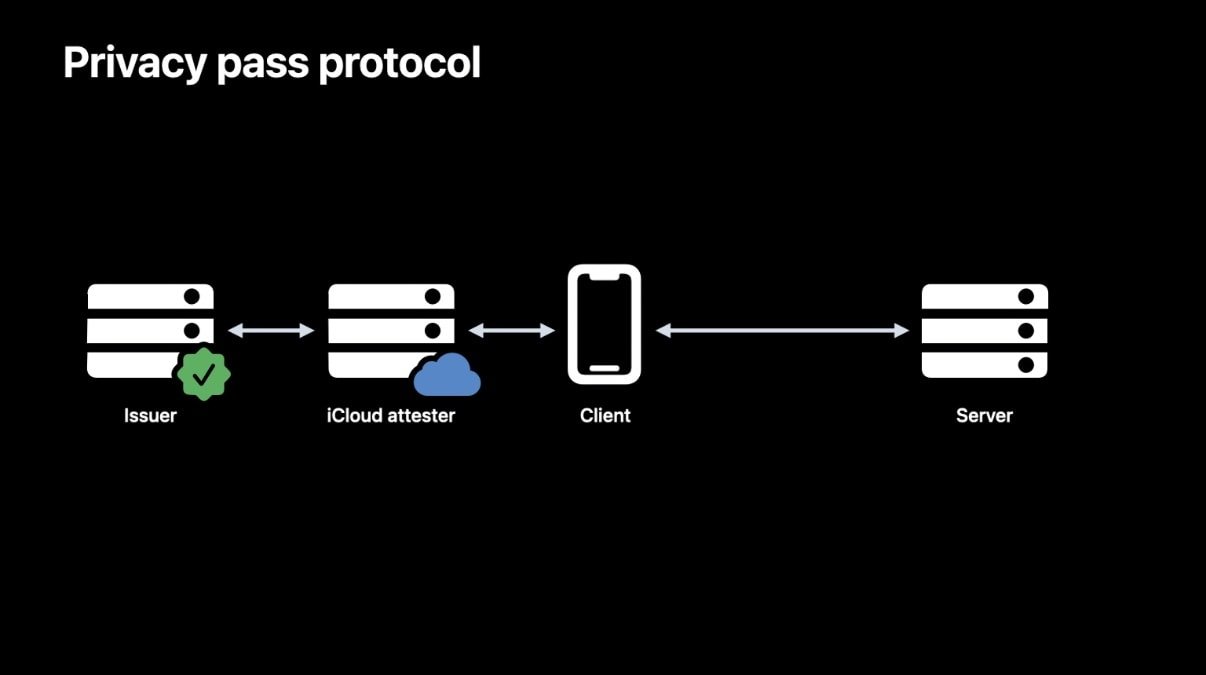
Using a new HTTP authentication method called PrivateToken, a server uses cryptography to verify a client passed an iCloud attestation check.
When the client needs a token it contacts an attester — in this case, Apple — which performs the process using certificates stored in the device's Secure Enclave. The attester can also perform something called rate-limiting.
Rate-limiting can recognize if the client device is following typical user patterns or is part of an iPhone click farm, as one example.
When an Apple user logs into their device with a password, Touch ID, or Face ID, open Safari and navigate to a website, their actions are hard for a bot to imitate.
The signed token is eventually sent to the server in a multi-step process. The server doesn't know anything about the device or the person accessing it. But it trusts the attester and validates the token, and the person is taken to their destination web page.
Cloudflare explains that when PATs are used, device data is isolated and not shared between the parties involved in the process. Cloudflare knows the destination URL but not the device or user interaction information.
The website only knows the URL and client IP address, and the device manufacturer or attester only knows the minimum amount of device data required for attestation. It doesn't know the destination URL or the user's IP address.
Tokens are single-use as a way to limit replay attacks, which is when a client tries to present a token multiple times.
Web servers accessed through Safari and WebKit will work automatically with PATs. Other devices may not recognize the token process, so Apple cautions developers to make sure user authentication doesn't block the main web page and to present it as optional.
Apple says that these tokens require a device running iOS 16 or macOS Ventura or later with an Apple ID signed in. The Apple ID is only used for attestation and isn't shared.
It's an interesting move from Apple, and the goal of ending CAPTCHA is a noble one. It's also another way in which Apple users experience the web differently.
With technologies such as iCloud Private Relay, Hide My Mail, and App Tracking Transparency, Apple continues to limit exposure of personal information for its customers.
The company is working to help make Private Access Tokens a web standard, but there is no mention of tokens working on Android or Windows. People on those platforms may have to put up with CAPTCHAs, for now — or wait for Microsoft's and Google's work on the matter.
 Andrew Orr
Andrew Orr

-m.jpg)






 William Gallagher
William Gallagher
 Thomas Sibilly
Thomas Sibilly
 Andrew O'Hara
Andrew O'Hara
 Amber Neely
Amber Neely
 Marko Zivkovic
Marko Zivkovic
 Malcolm Owen
Malcolm Owen
 William Gallagher and Mike Wuerthele
William Gallagher and Mike Wuerthele









5 Comments
Anything that gets rid of those awful “Click all of the…” CAPTCHAs sounds great to me!
Apple trying to gatekeep the whole internet and to put an end to open source devices.
Soon: This website is only available to non-jailbroken devices running iOS 16 or later because corporates don't like to build several different solutions. Just like they are ignoring Firefox more and more, increasing the power of Google and Chrome - this would lock people into the PAT ecosystem and allow websites to get hard proof that you are running a certified Apple device.
The web was set out to be an open platform, with non-discriminatory access for everyone - this is the opposite. But hey, most people seem to accept Google's invasive reCAPTCHA already..
Look I love the site but I have to tell you... seriously stop putting them on a pedestal. I've had this tech since 2015 on most other devices, it's nothing new, and it's definitely not something Apple is bringing to revolutionize the world.
On top, it's actually quite problematic because now the only way to share accounts is gonna be through google/apple family package. You're welcome, Netflix and Amazon. Not only that, but they can also disable you completely as they instantly become your only identity provider. You don't get your identity anymore, it's whatever apple's servers says it is... which can be "terrorist for insulting someone on the internet" if they want to.
Think critically, not different.
I still want the CAPTCHA platform dead. Put down. Buried. Ground into nothingness. It's a potentially viable concept horrific in execution. If it was finished, I'd cheer.
If a website knows that I'm using TouchID or FaceID to authenticate, doesn't that ALREADY imply a human is there and that there's no need for a captcha?
On the other hand, most Macs don't have TouchID or FaceID yet, and human validation is probably more important on Macs than on iOS devices because iOS devices don't make it easy to insert your own automation software.
Has anyone got a TouchID enabled Mac laptop, and does using it mean you can avoid captchas already?