Inserting an unprotected iPhone or iPad into a new port can leave you with unwanted infections. "Juice jacking" and "trustjacking" are two ways to catch digital diseases, but there are ways to protect yourself.
You might not have previously thought about cybersecurity when charging your iPhone on the go, but that Lightning cable can carry data as well as power. Here are the vulnerabilities involved and how to minimize the risks.
What is "juice jacking?"
Smartphones and tablet computers use the same port for charging and data transfer. "Juice jacking" exploits the possibility that an owner might connect their device to a malicious or compromised charging port, which can then be used to steal data from the device.
Previously, iOS devices were more vulnerable to juice jacking, since connecting an iOS device to a PC didn't require authorization. However, when iOS 7 was introduced in 2013, this was no longer the case.
How to prevent juice jacking
When you connect your iOS device to a computer, iOS 7 prompted you with, "Trust This Computer? Your settings and data will be accessible from this computer when connected via USB or Wi-Fi." You could then select "Trust" or "Don't Trust."
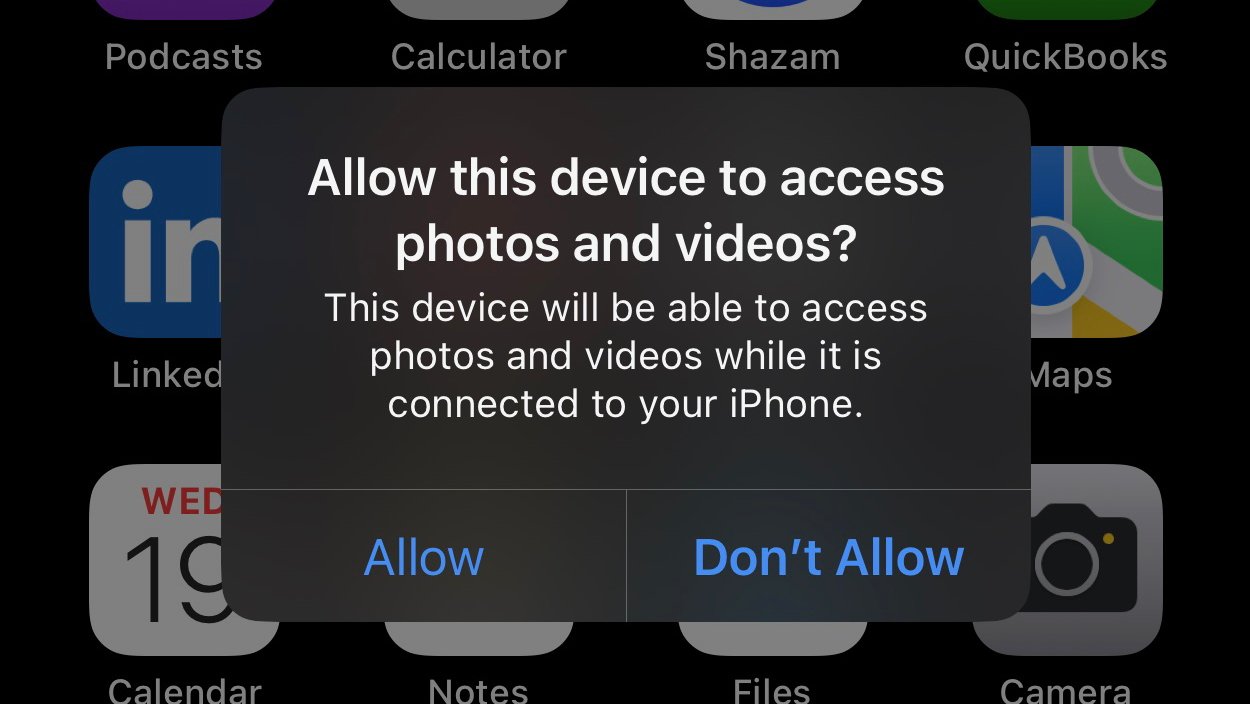
The wording was later changed to, "Allow this device to access photos and videos? This device will be able to access photos and videos while it is connected to your iPhone." You could then choose "Allow" or "Don't Allow."
Providing you choose Don't Allow, juice jacking can't occur. If you see this prompt when connecting your device to a port that's only supposed to provide charging, it's likely to be a malicious attempt to transfer data or install malware.
While this prompt — if declined — effectively prevents juice jacking on iOS devices, a related vulnerability was discovered in 2017, called "trustjacking."
What is "trustjacking?"
Symantec, the cybersecurity software company, discovered a way in which another user can control the owner's iOS device via Wi-Fi, even when it's no longer connected to a malicious socket by a cable.
It works by exploiting a feature called iTunes Wi-Fi Sync, which (as the name suggests) allows an iOS device to be synced with a computer's iTunes software via Wi-Fi when they are not physically connected together.
Choosing Allow upon connecting the iOS device with a cable allows the computer to communicate with it using iTunes APIs. Although this method still depends on the owner choosing to trust the connected computer, it provides a way for the attacker to persistently control the device at a high level once the physical connection is severed.
Trustjacking enables an attacker to make iTunes backups and install applications - all without the owner's notice or consent. Pulled backups can include iMessage & SMS chats as well as app data. Furthermore, apps installed on the device can be surreptitiously replaced with malicious ones which can gather sensitive information and data about the user's activity.
Although the use of iTunes Wi-Fi Sync is limited to when the computer and the iOS device are connected to the same Wi-Fi network, trustjacking can potentially be combined with a malicious profile attack and use a VPN to maintain permanent access. However, the risk of encountering this situation is low, and only applies to devices enrolled in an organization's MDM program.
Apple's response to trustjacking
To mitigate the trustjacking issue, Apple introduced an extra step with the release of iOS 11 in 2017. This added the requirement to enter the device's passcode when the Allow option is selected, to ensure that only the iOS device's owner could authorize the data connection.
However, providing authorization occurs, this still doesn't stop an iOS device from being controlled by iTunes Wi-Fi sync once the cable has been disconnected, or warn the user about this possibility, so it only partially addressed the vulnerability.
How to reduce the risk of trustjacking
As far as we can tell, trustjacking is still a risk for all iOS and iPadOS devices. Thankfully, there are a few ways in which you can minimize this risk as a device owner.
Firstly, if you're at all suspicious that there's an unwanted computer with access to your device, you can revoke access to all trusted computers. Once you've done this, you'll need to re-authorize all the computers to which you want to connect your device.
- Go to Settings
- Tap Transfer or Reset iPhone/iPad
- Tap Reset
- Select Reset Location & Privacy
- Then enter the device's passcode to confirm.
You can also encrypt iTunes backups so that would-be attackers can't read the information. To do this, connect your device to a computer you trust.
How to encrypt local backups of your iPhone
- For Macs, open Finder, or, for Windows PCs, open iTunes.
- From the General or Summary tab, go to the Backups section.
- Check Encrypt local backup.
Finally, remember that a data connection isn't needed if you just want to charge your iPhone or iPad, so always choose the Don't Allow option unless you're transferring data. And if you don't own the computer being used, it's probably best practice to revoke access once you're done.
 Alex Baggott
Alex Baggott








 Wesley Hilliard
Wesley Hilliard
 Marko Zivkovic
Marko Zivkovic

 Malcolm Owen
Malcolm Owen

 Amber Neely
Amber Neely










