Once again, BitTorrent client Transmission has distributed malware to some users through an altered installer, with downloaders of the software on Aug. 28 and 29 probably infected by the "Keydnap" package.
The previous version of Keydnap required users to click on a maliciously formed file, which then opened the installer in Terminal. The malware then waited to install until the next app was launched, and popped up a dialog box asking for authentication.
When packaged with Transmission, the malware needed no second app to execute, nor did it require further user authentication beyond what was needed to install Transmission. Additionally, since the Transmission app was properly signed, Gatekeeper allowed the execution of the malware installation without complaint.
After being granted root access, the updated Keydnap can then be used by the owners of the improved command and control server to hunt down the decryption key for the user's Keychain, and upload the stored passwords. Keychain-stored passwords include system passwords, as well as login information for Internet-based services, such as banking credentials, Gmail passwords, Amazon login information, and others.
The signature included in the bogus Transmission installer does not belong to the legitimate developers. Apple has been informed about the bad signature, and it is unknown if the key has been revoked at this time.
Transmission's developers immediately pulled the infected download after being informed of the issue.
ESET Research recommends that users who installed Transmission between Aug. 28 and Aug. 29 look for any of the following files or directories:
- /Applications/Transmission.app/Contents/Resources/License.rtf
- /Volumes/Transmission/Transmission.app/Contents/Resources/License.rtf
- $HOME/Library/Application Support/com.apple.iCloud.sync.daemon/icloudsyncd
- $HOME/Library/Application Support/com.apple.iCloud.sync.daemon/process.id
- $HOME/Library/LaunchAgents/com.apple.iCloud.sync.daemon.plist
- /Library/Application Support/com.apple.iCloud.sync.daemon/
- $HOME/Library/LaunchAgents/com.geticloud.icloud.photo.plist
To supplement Gatekeeper, an internet connection monitoring application like Little Snitch can be used to examine incoming and outgoing Internet transmissions, and block undesirable ones, such as the broadcast of pilfered data with this implementation of Keydnap. Utilities similar to BlockBlock can continuously monitor for installation of persistent components vital for malware installers.
Originally, ESET had no idea how Keydnap was spread, and suspected that security researchers were the prime target. The latest inclusion in Transmission is the first wide vector of attack for the malware.
For two days in March, users who downloaded Transmission 2.90 were subject to the KeRanger malware. When incorporated into an app, KeRanger connected to a remote server through the Tor anonymizing service, then began encrypting stored documents and data before asking for a one bitcoin ransom.
 Mike Wuerthele
Mike Wuerthele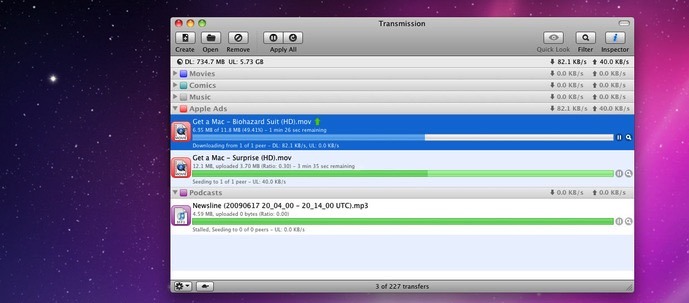







-m.jpg)






 Chip Loder
Chip Loder
 Marko Zivkovic
Marko Zivkovic
 Malcolm Owen
Malcolm Owen
 Christine McKee
Christine McKee

 Sponsored Content
Sponsored Content










36 Comments
Besides thieves who download music/movies, who else uses BT?
If they're trying to get their app banned from torrent sites, they're doing a good job.