Another Mac-specific malware pops up, but Apple's Gatekeeper still prevents infection
A second piece of Mac-specific malware has been discovered this week, one that could expose the passwords stored in the macOS Keychain. But once again, Apple's Gatekeeper security — when properly configured — will block the attack from succeeding.
Researchers at security firm ESET have been examining a new strain of OS X malware from an unknown source, and have published a breakdown of the so-called "OSX/Keydnap" package.
The malware is distributed as a .zip compressed archive, containing the package disguised as a text file or JPG graphic with accompanying icon. However, the file name has a trailing space, which by default, opens the Mach-O executable in the macOS Terminal.
After a double-click on the file, the Terminal icon appears in the dock, and very quickly closes. At this point, if Gatekeeper is active, the security mechanism pops up a warning to the user, saying that the file is from an unidentified developer, and prevents the launch.
If Gatekeeper has been configured by the user to execute all software regardless of source, the malware then downloads and runs the backdoor component which is executed at every reboot, replaces the Mach-O executable that the user clicked on with a decoy graphic or text file, and opens the decoy document in Preview.
The malware will seek root access, by waiting until another application launches, and popping up a dialog for user credentials.
After being granted root access, OSX/Keydnap can then be used by the owners of the a command and control server to hunt down the decryption key for the user's Keychain, and upload the stored passwords. Keychain-stored passwords include system passwords, as well as login information for Internet-based services, such as banking credentials, Gmail passwords, Amazon login information, and others.
To supplement Gatekeeper, an Internet connection monitoring application like Little Snitch can be used to examine incoming and outgoing Internet transmissions, and block undesirable ones, such as the download of the malware component in this case. Utilities similar to BlockBlock can continuously monitor for installation of persistent components vital for malware installers.
The revelation of the OSX/Keydnap package is the second Mac malware reveal in a week. On July 6, Backdoor.Mac.Eleanor was exposed, and is also easily preventable with properly configured Apple-provided security software, or by user awareness of the attack vector. AppleInsider was not able to obtain a sample of the malware to see if Apple's Xprotect has been updated.
The researchers at ESET note that they have no idea how the malware is spread, but spam email attachments are likely. Additionally, they have no count of active infections. Decoy images found during research point to the possibility of security researchers being a target of the malware.
 Mike Wuerthele
Mike Wuerthele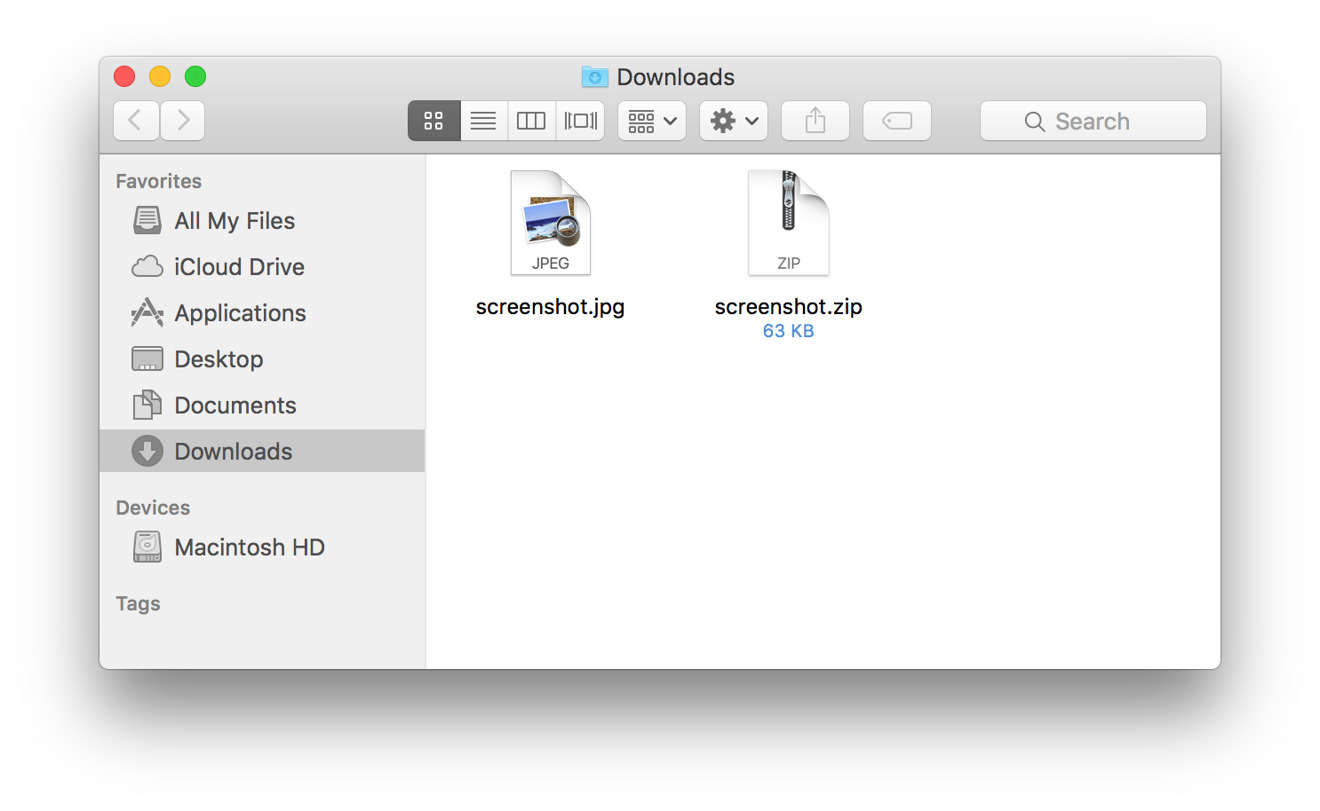










 Malcolm Owen
Malcolm Owen

 William Gallagher
William Gallagher
 David Schloss
David Schloss
 Amber Neely
Amber Neely