An operations security manual developed to advise journalists and political activists on how to protect their identities is now being distributed by supporters of Islamic State terrorists. One of its recommendations is to use Apple's securely encrypted iMessage service.
According to a report by Kim Zetter for Wired, the OPSEC manual, discovered by researchers at the West Point military academy in online forums used by ISIS supporters, details a variety of ways members can avoid being detected.
The manual appears to have been entirely co-opted from work done by a Kuwaiti security group to advise journalists and activists working in Gaza. However, despite being distributed among ISIS supporters, it appears that even the terrorist group's most dangerous members are not actually following it.
Abdelhamid Abaaoud, the suspected mastermind behind mass murder plots in both Belgium and France, frequently failed to use encryption in his own phone communications and also left behind a cell phone with unencrypted content including photos and videos that identified him. Others involved in the Paris attacks discarded phones with active GPS, which helped authorities track where they had been and led them back to their safe-house.
OPSEC advice only as good as the user
Aaron Brantly of West Point's Combating Terrorism Center told Wired that the security manual was "about as good at OPSEC as you can get without being formally trained by a government," and that its advice was "roughly what I give to human rights activists and journalists to avoid state surveillance in other countries."
He added, "If they do it right, then they can become pretty secure. [But] there's a difference between telling somebody how to do it and then [them] doing it right." The OPSEC manual largely mirrored the general advice given to anyone who wants to avoid being hacked
The advice in the OPSEC manual largely mirrored the general advice given to anyone who wants to avoid being hacked, whether by government agencies, malware hackers, identity thieves, or even advertising networks that seek to profile their users.
The manual advised on using strong passwords, and warned against clicking on "suspicious" links that could enable government agencies or other hackers to breach their security. It also described how to set up ad-hoc WiFi networks to distribute photos and text messages without needing internet access.
Facebook bad, iMessage good, No mention of Playstation
Mirroring much of the same advice given in a guide written by the Electronic Frontier Foundation, the OPSEC manual advised against using most American providers of VPNs, encrypted chat tools and other services, particularly singling out Instagram because its parent company— Facebook— has a poor track record on privacy.
It similarly advised against using FaceBook's WhatsApp, a chat application that makes use of encryption and which has been singled out by US government officials as being used by ISIS to avoid surveillance. Despite using encryption, Wired noted that a German security firm had earlier reported problems with how it implemented this.
Sony's Playstation console, another encryption tool specifically cited by authorities as a way for terrorists to communicate, was not found in the OPSEC guide at all, West Point researcher Brantly stated.
The EFF's report specifically called out AIM; BlackBerry Messenger; Facebook's Messenger and WhatsApp; Google Chat and Hangouts; Microsoft's Skype; Secret; SnapChat and Yahoo Messenger as failing to provide end to end encryption, while calling Apple's iMessage and FaceTime "the best of the mass-market options."
The OPSEC guide also made a notable exception to its blanket recommendation against using American products: Apple's iMessage, which got a thumbs up for using encryption in a way that neither government intelligence agencies nor Apple itself can spy upon.
However, there's no evidence that ISIS is actually using iMessage, as the OPSEC manual was written for journalists operating in Israel and Gaza by researchers in Kuwait. ISIS operates across a series of regions where iPhones have very low penetration.
Al-Qaeda prefers Android
Last year, a report by in intelligence firm Recorded Future showed that Al-Qaeda groups have focused on developing their own encryption tools, focusing on mobile devices, with "Android as the preferred platform for these groups."
The primary reason Al-Qaeda likes Android is "the large availability and affordability of Android phones, especially in underdeveloped countries," the firm noted.
While Android's legendary lack of inherent security singles out its users for targeted malware attacks, the insecure nature of the platform also provides Al-Qaeda with a vast network of devices to exploit for use in distributed Denial of Service attacks or to obfuscate the source of its communications.
Like encryption, backdoors can be also used by both good and bad people
The OPSEC manual disturbed by ISIS members warned that, in general, communications on both Android and iOS are only fully secured when all their data traffic is routed through Tor, a distributed anonymizing service that obscures the source of transmissions. It specifically recommended using an Android phone with third party mobile encryption, such as Cryptophone or Blackphone.
Apple has already come under fire from the U.S. Department of Justice and Federal Bureau of Investigations for not supporting a "backdoor" mechanism that would give governments open access to communications for surveillance purposes.
New outbreaks of terrorist attacks are being leveraged by the FBI, Central Intelligence Agency and other groups to demand more government access, even though the evidence shows that the terrorists involved commonly weren't using encryption to plot their attacks. The primary use of citizen surveillance in the U.S. targets the use of drugs and guns, noted a report by The New York Times.
Apple's chief executive Tim Cook has repeatedly maintained that adding "backdoors" to allow American or other western government agencies to surveil users is ignorant, shortsighted policy.
"To protect people who use any products, you have to encrypt," Cook told the Telegraph in an interview earlier this month. "You can just look around and see all the data breaches that are going on...we believe very strongly in end to end encryption and no back doors."
Cook warned that requiring companies to add backdoors could have "dire consequences," saying that "any backdoor is a backdoor for everyone.""If you halt or weaken encryption, the people that you hurt are not the folks that want to do bad things. It's the good people. The other people know where to go" - Tim Cook
He added, "It's not the case that encryption is a rare thing that only two or three rich companies own and you can regulate them in some way.
"Encryption is widely available. It may make someone feel good for a moment but it's not really of benefit. If you halt or weaken encryption, the people that you hurt are not the folks that want to do bad things. It's the good people. The other people know where to go."
Despite recognizing iMessage as a secure tool, the OPSEC obtained and distributed by ISIS members shows that Cook's statements are true. The majority of ISIS terrorists are already using open Android devices that are cheap and disposable, and can side-load homegrown encryption apps, if and when they bother to use encryption at all.
 Daniel Eran Dilger
Daniel Eran Dilger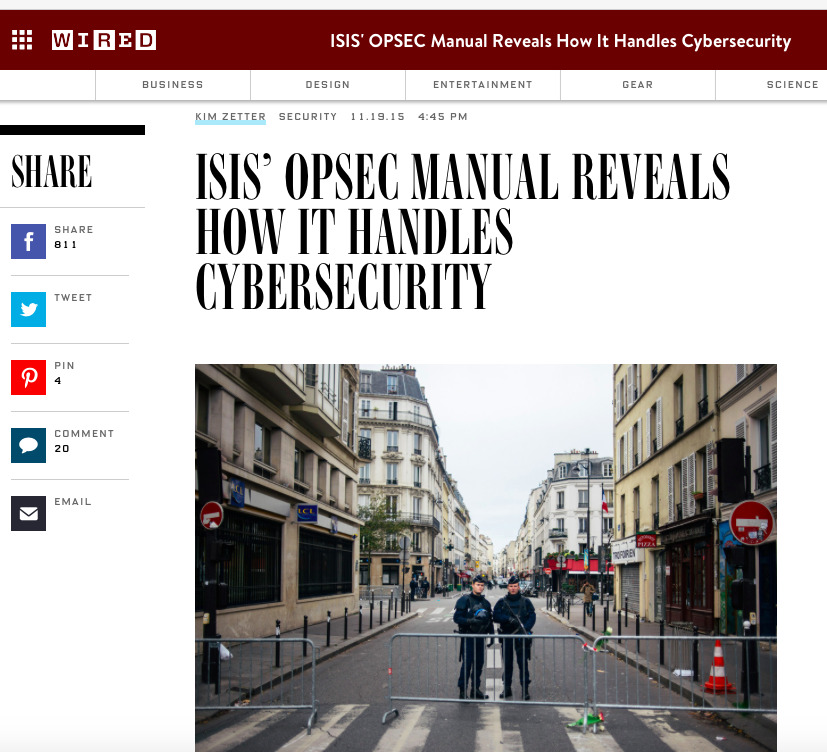







-m.jpg)






 Christine McKee
Christine McKee
 Marko Zivkovic
Marko Zivkovic
 Wesley Hilliard
Wesley Hilliard
 Malcolm Owen
Malcolm Owen


 William Gallagher
William Gallagher
-xl-xl-m.jpg)








200 Comments
Gizmodo: APPLE SUPPORTS TERRORISM
Let's just start referring them as iSIS.
Find my iPhone. Bomb said iPhone.
Just because evil people use a tool, it doesn't mean anything is wrong with the tool.
Just because evil people use a tool, it doesn't mean anything is wrong with the tool.
So true but there are those who will surely twist the facts. Some post right here on AI.