HomeKit bug affecting iOS disclosed by security researcher
Last updated
A vulnerability in iOS that uses HomeKit as an attack vector involving very long device names, has been disclosed after a researcher disclosed it to Apple in August 2021.
As with its other products, Apple is keen on keeping HomeKit as secure as possible for its users. In a disclosure published on January 1, it seems that there is a bug in the smart home platform that could cause problems for its users.
According to security researcher Trevor Spiniolas, if a HomeKit device name is changed to a "very long string," set at 500,000 characters in testing, iOS and iPadOS devices that loads the string can be rebooted and made unusable. Furthermore, since the name is stored in iCloud and gets updated across all other iOS devices signed into the same account, the bug can reappear repeatedly.
Spiniolas has called the bug "doorLock," and claims it affects all iOS versions from iOS 14.7 onwards under testing, though it is likely to also exist on all iOS 14 versions too.
Furthermore, while an update in iOS 15.0 or 15.1 imposed a limit on the length of a name that an app or a user could set, the name can still be updated by previous iOS versions. If the bug is triggered on an iOS version without the limit and shares HomeKit data, all devices it shares the data with will be affected as well, regardless of version.
There are two situations that can occur, with devices that don't have Home devices enabled in Control Center finding the Home app is unusable and crashes. Neither reboots nor updates will fix the problem, and restored devices will again render Home unusable if it is signed into the same iCloud account.
For iPhones and iPads that have Home devices enabled in Control Center, which is the default setting for when users have access to HomeKit devices, iOS itself becomes unresponsive. Inputs become delayed or ignored, with the device unresponsive and going through the occasional reboot.
Rebooting nor updating the device will fix it in this situation, and disrupted USB access basically forces users into restoring their device and losing all local data. However, restoring and signing into the same iCloud account will trigger the bug again with the same effects as before.
Spiniolas believes the issue could be used for malicious purposes, such as via an app with access to Home data introducing the bug by itself. It's also feasible for an attacker to send invitations to a Home to other users, even if the target doesn't own a HomeKit device.
How to avoid the issue
According to the researcher, the worse of the two scenarios can be avoided by disabling Home devices in Control Center. To do so, open Settings followed by Control Center, then set the toggle for "Show Home Controls" to off.
Users should also be vigilant to invitations to join Home networks of other users, especially those from unknown contacts.
A slow fix
Spiniolas claims to have initially reported the bug to Apple on August 10th, with Apple said to have planned for a security update fixing the bug to be issued by the end of 2021. However, Apple then allegedly changed its estimate on December 8th to "Early 2022."
The delayed fix prompted Spiniolas to warn Apple that a public disclosure of the bug would be made on January 1, 2022.
"I believe this bug is being handled inappropriately as it poses a serious risk to users and many months have passed without a comprehensive fix," writes the researcher. "The public should be aware of this vulnerability and how to prevent it from being exploited, rather than being kept in the dark."
 Malcolm Owen
Malcolm Owen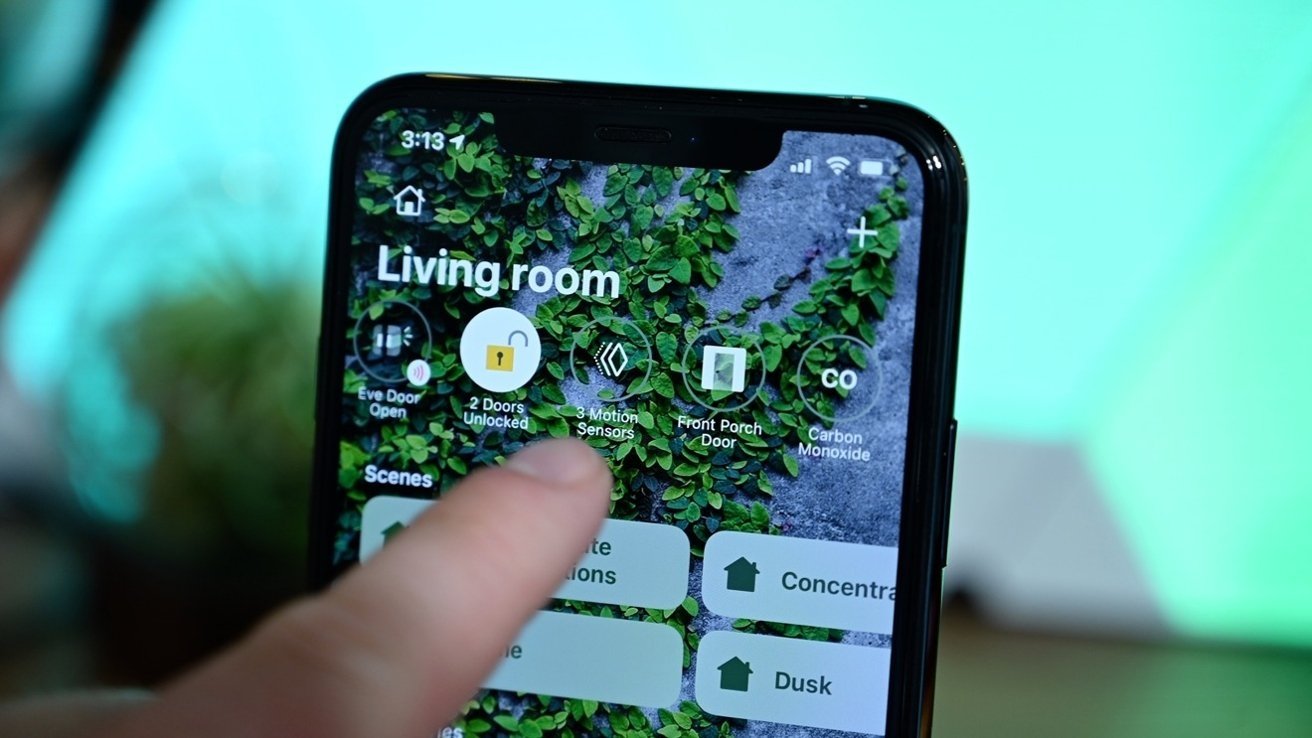











 Amber Neely
Amber Neely
 Thomas Sibilly
Thomas Sibilly
 AppleInsider Staff
AppleInsider Staff
 William Gallagher
William Gallagher

 Christine McKee
Christine McKee









7 Comments
"...the bug to Apple on August 10th, with Apple said to have planned for a security update fixing the bug to be issued by the end of 2022" :s
Seems a tish bit long a window to fix this bug, but hey, what do I know? >:)
What’s considered a “very long string”? Pretty certain most people aren’t using anywhere near 500k characters for HomeKit device names. That’s such a ridiculous number to test with. Why not 100, 1k, 100k, all of which are still absurdly high. And who accepts HomeKit invites from people they don’t know?
I have mixed emotions on the "security researcher"'s handling of this. Apple said they have the intent to patch this - but to the researcher it isn't soon enough. That smacks of ego-boosting self promotion and "blackmail" of a vendor when an arbitrary deadline isn't met without fully assessing how severe the vulnerability really is.
One other hand, vendors do need to quickly patch serious breaches. And "security by obscurity" is not security.
On the other hand, if Apple hasn't seen an active exploit where they are getting inundated by people with bricked phones because of this, that means that the hacker community hasn't probably figured this one out yet. And now this "researcher" just gave them the ability to do so.
Any good security professional will tell you that the vulnerabilities (bugs) you have to address immediately are those that are easily exploitable, have no or impractical mitigations, and have the greatest impact when exploited - for example, the infiltration and extraction of data. In other words, the threat is high and the risk of that damage when it happens is severe. Yes it's inconvenient when your phone crashes, but that's a denial of service attach, not data exposure.
My guess is that Apple's opinion of the bug is that it doesn't push all those measurements to a level that screams "emergency".
"Seems a tish bit long a window to fix this bug, but hey, what do I know?"
I don't know either. But we have no idea what changes have to be made to completely address this. The degree of exposure and likelihood of this happening probably doesn't mean Apple should drop everything and fix this one. Like they have with many others with active exploits.