Apple's iPadOS 16.3 is out with support for security keys
Apple has released iPadOS 16.3 to the public with support for physical security keys that can add another layer of protection for Apple ID.
The iPadOS 16.3 update is is available to download by the public. It is a relatively minor release compared to iPadOS 16.2 with its most significant feature being support for security keys.
After a long beta cycle with relatively few beta versions, Apple finally revealed that the update would also bring support for the new HomePod. It also expands Advanced Data Protection to countries outside of the United States.
iPadOS 16.3 releases alongside iOS 16.3, macOS 13.2, and the other operating system updates. The releases are mostly focused on bug fixes and performance improvements.
How to install iPadOS 16.3 on the iPad
- Open the Settings app.
- Select General.
- Select Software Update.
- Select "Update to iPadOS 16.3."
If an iPad is set to automatically update, it will handle downloading and installing iPadOS 16.3 on the user's behalf.
 Andrew Orr
Andrew Orr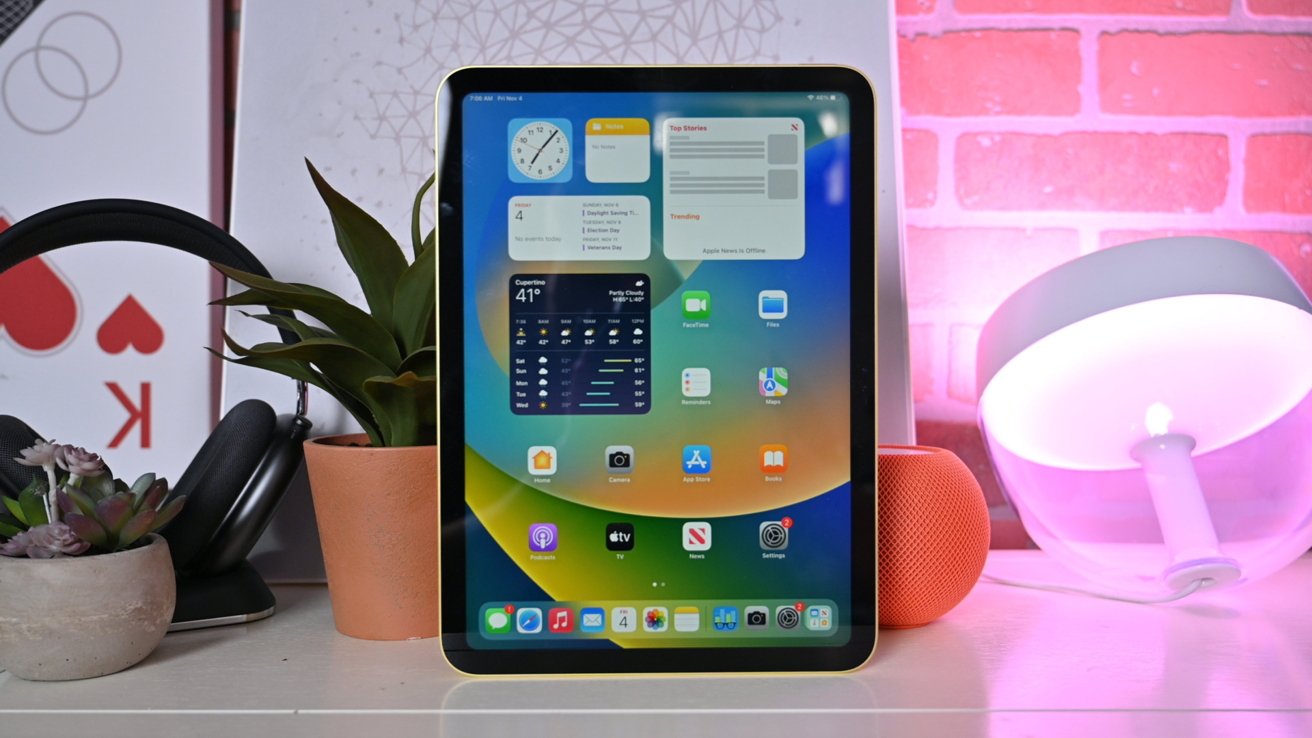






 Amber Neely
Amber Neely
 Thomas Sibilly
Thomas Sibilly
 AppleInsider Staff
AppleInsider Staff
 William Gallagher
William Gallagher
 Malcolm Owen
Malcolm Owen
 Christine McKee
Christine McKee








6 Comments
I'm not "getting" the benefit to Security Keys over two factor authentication, which is easy to use and effective.
I hope AI does a story like "who needs Security Keys" to help me understand it better.
It would be interesting to see how the security capabilities outlined in the article linked below map to technology and capabilities that Apple is now making available.