One of the first found feature changes in iOS 16.6 and iPadOS 16.6 may be an iMessage verification system that could help prevent government agencies from eavesdropping on the conversations of critics.
In December 2022, Apple introduced a number of security protections to help protect the sensitive data of its users in iCloud and iMessage. Months later, in the first beta of iOS 16.6 and iPadOS 16.6, Apple seems to be preparing to take one of the features live.
Released on May 19, the first developer beta of the new cycle includes a setting in iMessage to enable iMessage Contact Key. While the setting exists in the beta, reports MacRumors, it doesn't appear that the setting has been enabled in iOS itself, making its appearance an indicator that it should arrive in the near future.
During its introduction, Apple said that iMessage Contact Key Verification would arrive sometime in 2023, but not when.
The feature works as an enhancement to existing end-to-end encryption in iMessage itself, and specifically targets users who face what Apple refers to as"extraordinary digital threats." This refers to journalists, human rights activists, and members of government who may face attempts to break Apple's security and to eavesdrop on messaging conversations.
The Contact Key Verification feature allows a user to verify they are messaging only with the intended recipient, without interference from outside forces. For added security, users can verify with each other by comparing a Contact Verification Code in person, over FaceTime, or via other secured communications.
Users who have enabled iMessage Contact Key Verification will be alerted automatically if a state-sponsored attacker were to somehow succeed in breaching cloud servers or to otherwise find a way to monitor encrypted communications.
 Malcolm Owen
Malcolm Owen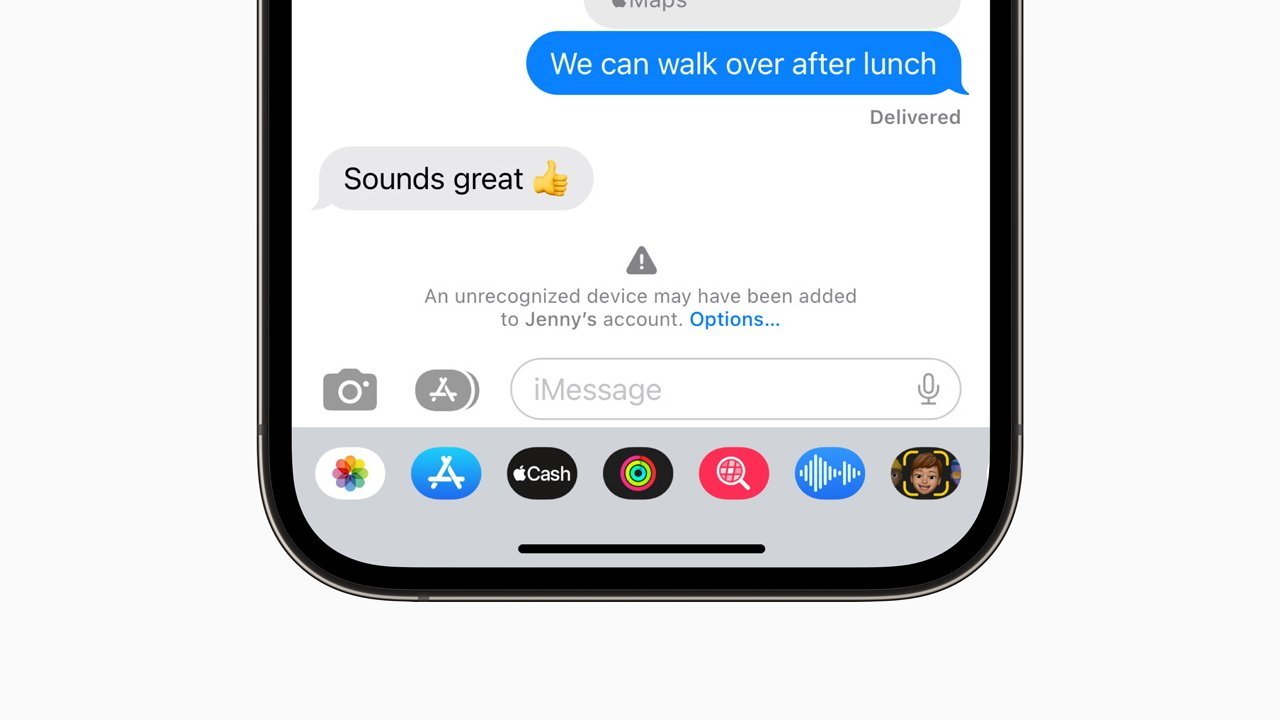








 Christine McKee
Christine McKee
 Marko Zivkovic
Marko Zivkovic
 Mike Wuerthele
Mike Wuerthele

 Amber Neely
Amber Neely
 Sponsored Content
Sponsored Content
 Wesley Hilliard
Wesley Hilliard








14 Comments
So iMessage is e2e encrypted, but if someone snoops on the cloud it’ll tell you!? Seems like there’s a little detail missing here somewhere…