The recent updates to iOS and macOS patched a serious flaw that could allow apps with Bluetooth access to record conversations with Siri.
An app could record a person's conversations with Siri and audio from iOS keyboard dictation when using AirPods or a Beats headset. It would happen without the app needing microphone access or showing that it was using the microphone.
Developer Guilherme Rambo found and reported the bug to Apple on August 26 and got a fast response a few days later that they were investigating. Apple patched the flaw, tracked as CVE-2022-32946 in the vulnerability database, on October 24 with iOS 16.1 and macOS Ventura.
SiriSpy
Rambo started by wondering about the audio quality on AirPods when using Siri, saying there is no drop in quality when using the microphone. However, there is typically a drop in quality during a video conference, for example.
He set out to investigate using a command-line tool he created called "bleutil." Rambo can use it to interact with Bluetooth Low Energy devices on macOS.
During testing, Rambo found that the tool intercepted audio data from the AirPods while he used Siri, and it didn't require microphone permission from the system. So he wrote an app for iPhone, iPad, Apple Watch, and Apple TV running both iOS 15 and the latest iOS 16 beta in late August.
The app tested the flaw, and Rambo found that an app with Bluetooth permission could record the user in the background without requesting permission. Control Center only listed "Siri & Dictation" as the feature running instead of the app.
Readers can find the complete explanation with technical details on Rambo's website. In short, it was a serious flaw, and it's unclear if other people also stumbled onto it.
How to Protect Yourself
In this case, the only way to protect conversations with iPhones and Macs is to update the latest software.
Updating is the best and most common advice in the security world. Updates to apps and operating systems almost always have fixes for security vulnerabilities found in older software versions.
Thankfully, Apple has improved the situation with iOS 16, iPadOS 16, and macOS Ventura. A feature called Rapid Security Response decouples security patches from software updates so the OS will protect users faster than ever.
In iOS 16 the setting is found in Settings > General > Software Update > Automatic Updates. A toggle called "Install Security Responses & System Files" says that patches for security bugs and system files will be automatically installed.
It's found in the same place within System Settings on macOS Ventura now that Apple has redesigned the older System Preferences app to be similar to iOS Settings.
 Andrew Orr
Andrew Orr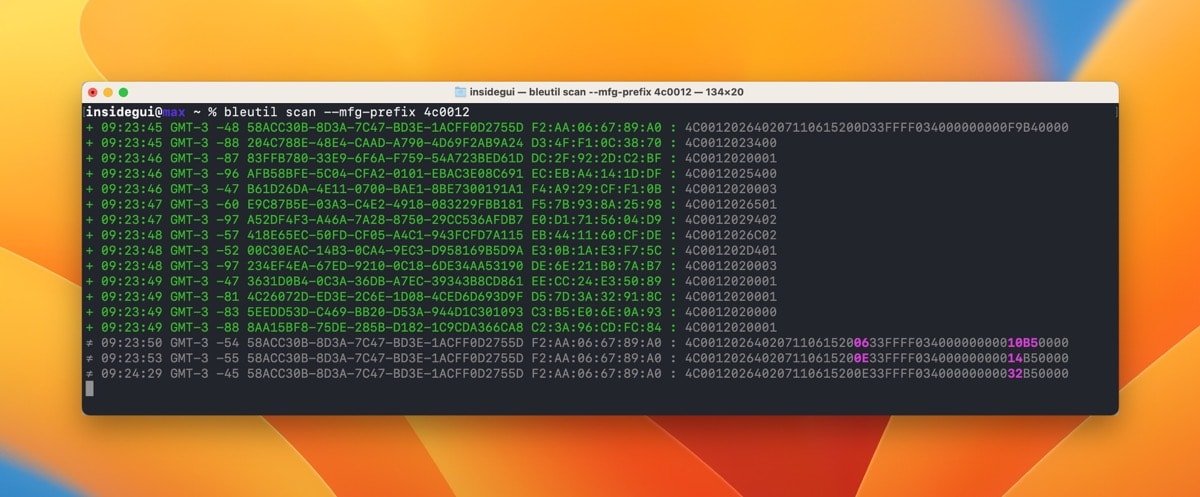







-m.jpg)






 Marko Zivkovic
Marko Zivkovic
 Mike Wuerthele
Mike Wuerthele
 Christine McKee
Christine McKee
 Amber Neely
Amber Neely
 Sponsored Content
Sponsored Content
 Wesley Hilliard
Wesley Hilliard

 William Gallagher
William Gallagher









6 Comments
Watch this get reported by the media as "your iPhone could have been listening to you" without the nuance of "a malicious app could have been listening to your Siri requests if the app had access to Bluetooth and you were making those Siri requests over Bluetooth".
"could have"
Chasing those meaty stories it seems.
Yeah I can already hear the cries of “See we told you Siri was spying on you”. I figure the first lawsuit will be filed by the weekend. Never mind that there’s no evidence that this was ever used.
Ha Ha Ha, people have no idea what does what. I don't know if it's still the case but Windows Cortana used to store audio requests in a hidden folder. This meant that on Windows, if one used Cortana for searches for something, law enforcement (or someone else) could potentially obtain audio of them in their own voice making the request.
I am NOT saying that Siri does this but our devices and their software are very complex and God only knows what it's all doing either by design or as a result of flaws.
Let the researchers come up with an actual app in the App Store that was doing this. Sideloading a malicious app on a jailbroken iPhone doesn’t count.