Touch ID changed the way users authenticate themselves on their devices. Before the iPhone 5s, most users went without any passcode on their smartphones, with a select few opting for 4-digit pins.
Apple shifted to Face ID in its iPad Pros and flagship iPhones, but Touch ID is still used in many modern Apple products. The iPad Air, iPad mini, 10.2-inch iPad, and iPhone SE still use fingerprint authentication.
The MacBook Air and all MacBook Pros come with fingerprint readers embedded in the keyboard. Desktop Macs running Apple Silicon gain Touch ID via an external Magic Keyboard. Apple doesn't offer Face ID in any Mac.
Touch ID features
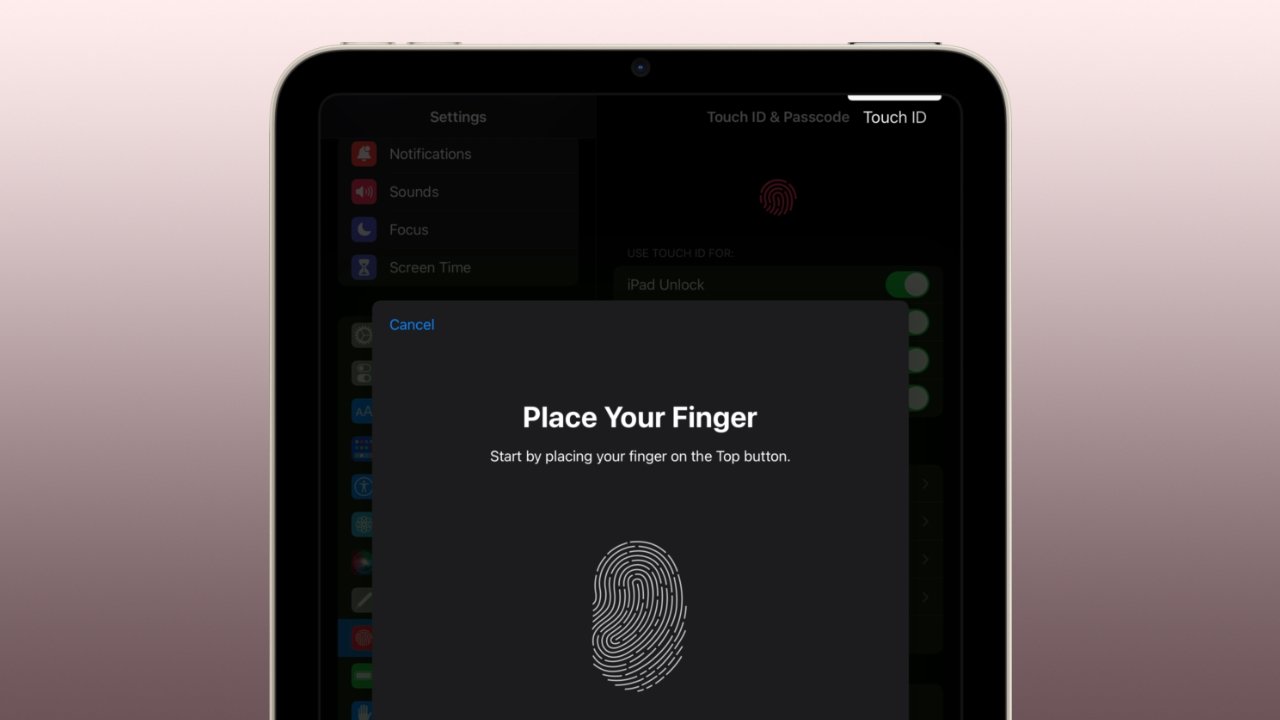
Apple allows users to create fingerprint scans of up to five fingers per device. Touch ID relies upon the same scanning technology and Secure Enclave data storage in every Apple device regardless of shape or location.
The Fingerprint Sensor
The fingerprint reader used in Apple products uses a sapphire-crystal surface surrounded by a steel ring. The glass protects the components used to capture the fingerprint underneath.
A high-resolution image is captured using capacitive touch when a finger is detected. This image is converted into a numeric value and encrypted before passing to the Secure Enclave.
The final value generated by the sensor is compared to a value stored in the Secure Enclave. If it matches one of the stored values, then the fingerprint is a match, and the device unlocks. This system has a 1 in 50,000 expected false positive value, compared to Face ID's 1 in 1 million.
Touch ID works similarly across devices, though it is fit within a smaller surface area within the power button on iPads.
Secure Enclave
Before Apple introduced the M1 processor, the Secure Enclave resided within a dedicated piece of Apple Silicon called the T2. Otherwise, any device with Apple Silicon had the Secure Enclave baked into the system-on-a-chip.
Apple's T2 Security chip is a 64-bit ARMv8 SoC that runs a separate operating system called bridgeOS 2.0. It handles the entire boot process, all encryption using a dedicated AES hardware engine, audio processing, camera control, and System Management Controller capabilities. It also enables the "Hey Siri" capability in Intel-based Macs.
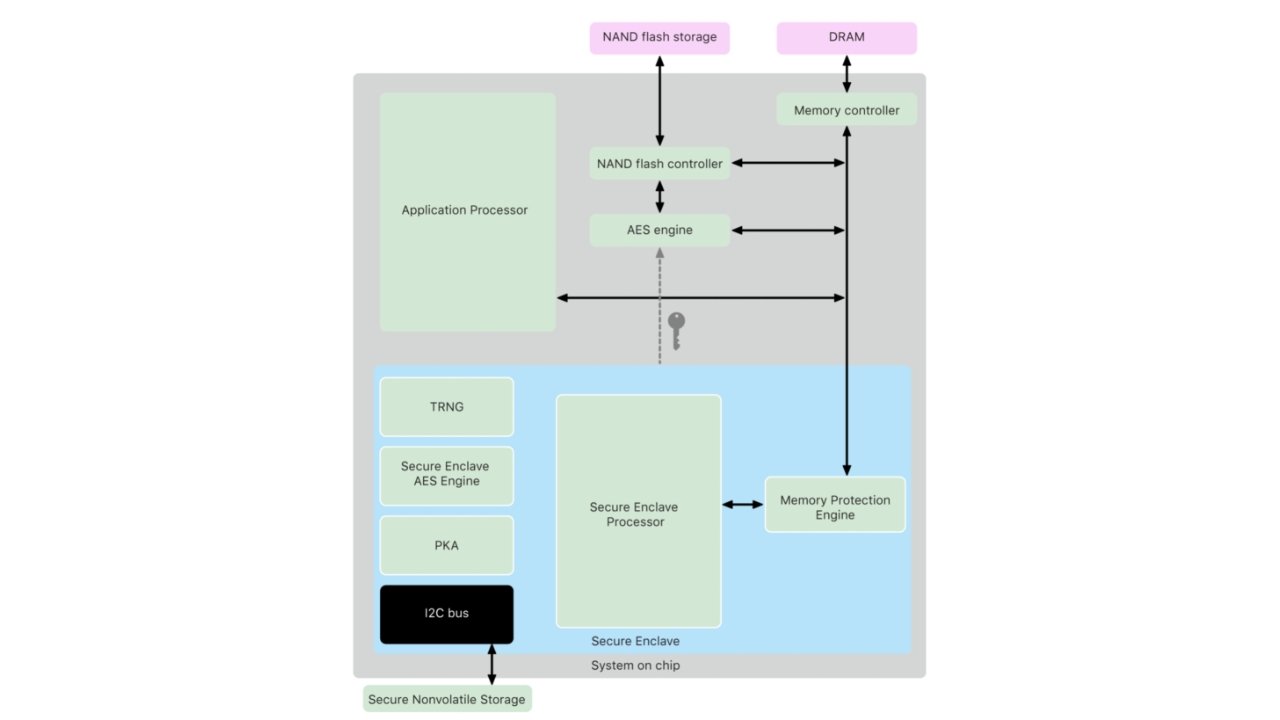
The Secure Enclave and the sensor have a shared key used to create a session key, which encrypts and authenticates the data. All data collected by the sensor is sent to the T2 Security chip using a dedicated serial peripheral interface bus. The T2 chip then forwards this data to the Secure Enclave for processing.
It is a coprocessor (or hardware-based key manager) that physically resides within the application processor package. It's isolated and communicates with the parent chip using an interrupt-driven "mailbox" – they also share memory data buffers. Because it is isolated and self-maintaining, it retains its integrity even if the operating system is compromised.
The data provided by the sensor is converted into mathematical representations by the Secure Enclave. These numbers are then encrypted and stored in the file system. The Secure Enclave's 4MB storage is solely used for 256-bit elliptic curve private keys.
When a file is created on the device, the AES engine generates and uses a new 256-bit "per-file" key to encrypt the file as it's written to the local storage. This key is then encrypted using a class key and stored in the file's metadata, which is then encrypted with a random file system key created when the operating system was first installed.
The Secure Enclave stores the class key and handles all wrapped file keys, which are never revealed to the main processor. The file system metadata key is encrypted using the Secure Enclave's Hardware UID (Unique Identifier) key on devices that use the Apple File System. The SoC's firmware encrypts all keys stored within the Secure Enclave.
Using Biometrics
Touch Id is used for more applications than just unlocking a device. It is integrated throughout Apple's operating systems for secure access to information and payments.
Developers can add support for biometrics to keep unauthorized users from snooping around apps in an already-unlocked device. Banking apps, secure messaging apps, and others have implemented this feature widely.
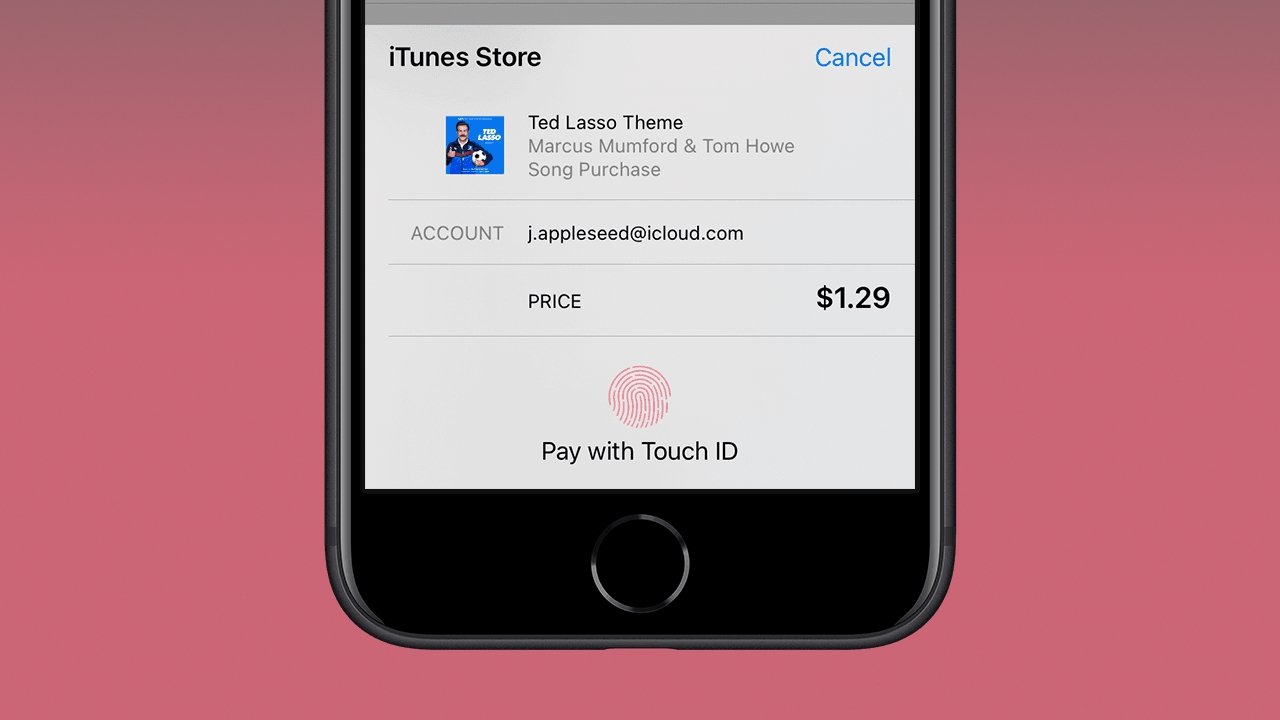
Apple Pay uses biometric authentication as well. This means any purchase made in apps, on the web, or at a payment kiosk will prompt the user for a fingerprint.
The system was designed so that developers could implement the feature without concern for which biometric was presented. Apps will ask for an authentication token, and the secure enclave will provide one after successful authentication of a face, fingerprint, or passcode.
Rumors
If rumors are true, Apple could revive Touch ID in its flagship iPhone lineup. Under-display fingerprint technology would allow Apple to supplement Face ID on iPhones without using a Home Button or Side Button. Some suggest that Apple could add a fingerprint reader via the sleep/wake button on iPhone, but it isn't clear if this would be used alongside Face ID as an alternative or in tandem.
The desire to return to Touch ID is strong given that the pandemic created a situation in which many people would conceal most of their faces on a day-to-day basis. However, Apple has maneuvered around this problem with a new version of Face ID that can be used when wearing a mask.



 Charles Martin
Charles Martin
 William Gallagher
William Gallagher
 Evan Selleck
Evan Selleck
 Andrew Orr
Andrew Orr
 Malcolm Owen
Malcolm Owen


 Mike Peterson
Mike Peterson