'MACDefender' on Apple's radar as OS X malware spreads - report
According to an internal AppleCare document obtained by Ed Bott of ZDNet, the "MACDefender" software is considered an "Issue/Investigation in Progress." The confidential internal document, issued to representatives this week, notes that "AppleCare does not provide support for removal of the malware."
A series of bullet points accompanying the document state that employees should not confirm or deny that the malware has ben installed, attempt to uninstall it, or send customers to Tier 2 for further resolution. In addition, representatives are also told not to refer customers to the Apple Store, as those employees do not remove malware either.
"Explain that Apple does not make recommendations for specific software to assist in removing malware," the document reads. "The customer can be directed to the Apple Online Store and the Mac App Store for antivirus software options."
Bott also previously reported via his Microsoft Report that an AppleCare representative said malware for the growing Mac platform is "getting worse." The anonymous person claimed that call volume at AppleCare is four to five times higher than normal, and the "overwhelming majority" of calls are related to MACDefender or another alias.
"Many Mac users think their Mac is impervious to viruses and think this is a real warning from Apple," the anonymous person reportedly said. "I really wish I could say not many people will fall for this, but in this last week, we have had nothing but Mac Defender and similar calls."
The MACDefender malware first gained attention earlier this month, when it was spotted by an antivirus company. The program automatically downloads in web browsers through JavaScript.
But users must also agree to install the software and provide an administrator password, which led Intego to categorize the threat as "low." However, the latest details would suggest that users are unaware of what they are installing and proceed with the installation anyhow.
The malware spreads through search engines like Google via a method known as "SEO poisoning." The sites are designed to game search engine algorithms and show up when users search for certain topics.
Users on Apple's support forums have advised killing active processes from the application using the Mac OS X Activity Monitor. MACDefender can then be deleted from the Applications folder by dragging it into the trash.
 Slash Lane
Slash Lane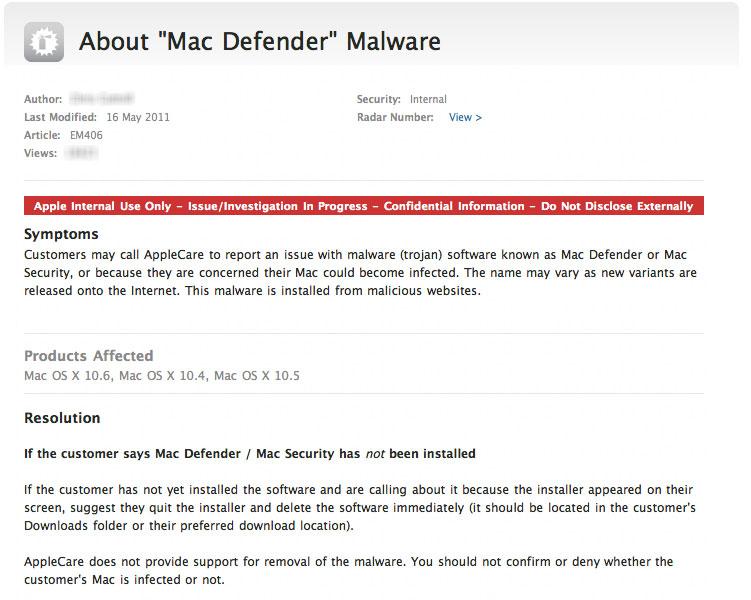










 Malcolm Owen
Malcolm Owen

 William Gallagher
William Gallagher
 David Schloss
David Schloss
 Amber Neely
Amber Neely