Mobile malware authors 'almost exclusively' focused on Android in 2013, says Symantec
Attackers continue to target Android more than any other mobile operating system, according to a new report released Tuesday, as Google's platform played host to all but one of the new mobile malware families discovered last year.
Microsoft's Windows Phone was the subject of the lone non-Android malware discovery, while Apple's iOS escaped the year unscathed. The data was revealed by Symantec as part of the company's annual internet security threat report.
The various app stores — both official and third-party — available to Android users continue to represent the platform's biggest weakness. A Remote Administration Tool, or RAT, appeared last summer, for instance, in a number of apps on the Google Play store.
To highlight those app stores' vulnerability, Symantec specifically called out "the release of an instant messaging application by a well-known smartphone vendor on the Android platform," likely referring to BlackBerry's BBM. "Attackers in turn took advantage of the popularity of the new app and released a variety of counterfeit versions bundled with adware. These apps were quickly removed from the Android marketplace, but not before accumulating a large number of downloads," they added.
Still other threats masqueraded as legitimate apps. Android.Fakedefender purported to be a malware scanning app which was itself a trojan, extorting users to pay for the removal of other, nonexistent viruses that it claimed to have discovered after a system scan.
Android has also been subject to increasingly sophisticated attacks as its installed base grows, the report said. Malware authors have begun to branch out from simply attempting to steal users' personal information to attacks traditionally seen on desktop operating systems, including hybrid campaigns that target both Android devices and PCs.
"The attraction of the mobile environment to attackers is clearly based on the size and growth rate of the user base today," the report reads. "Yet it's also based on the amount of personal information that's easily attainable once an attacker is on the device. With the right permissions the device's phone number, GPS coordinates, camera, and other information become readily available."
 AppleInsider Staff
AppleInsider Staff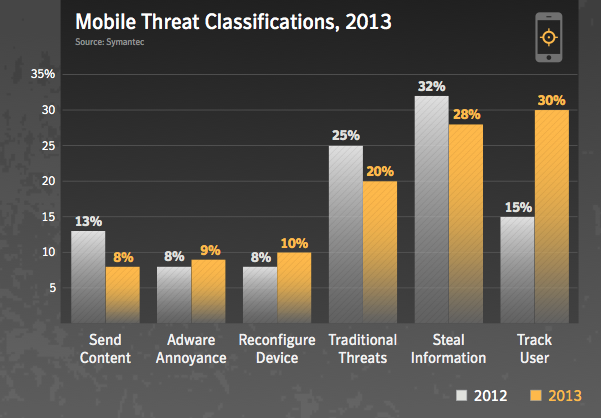











 Malcolm Owen
Malcolm Owen
 William Gallagher and Mike Wuerthele
William Gallagher and Mike Wuerthele
 Christine McKee
Christine McKee
 William Gallagher
William Gallagher
 Marko Zivkovic
Marko Zivkovic









