macOS's Keychain vulnerability reported earlier in Sept., Apple patch likely coming soon
The Keychain password vulnerability affecting multiple versions of macOS — including High Sierra — was reported to Apple on Sept. 7, and will likely be patched by the company in the near future, according to the security researcher who first publicized the issue.
Technical details of the exploit won't be made public until Apple has released that patch, Patrick Wardle told Gizmodo. He cautioned though that if he found the problem, other less conscientious actors may have beaten him to the punch.
"If I can find these bugs, obviously nation states, malicious adversaries, and cyber criminals have tons more time and resources. I'm sure they're finding these bugs as well," he said.
The researcher recommended updating to High Sierra in the meantime, since "there's a lot of good built-in security features," and there's no protection in remaining on Sierra.
On Monday Wardle published video of a concept app able to capture Keychain passwords in plaintext, without root access, so long as the victim is signed in. Real-world targets would have download, install, and run the app while bypassing macOS security measures designed to deter using unsigned software.
"macOS is designed to be secure by default, and Gatekeeper warns users against installing unsigned apps, like the one shown in this proof of concept, and prevents them from launching the app without explicit approval," an Apple spokesperson said to Gizmodo. "We encourage users to download software only from trusted sources like the Mac App Store, and to pay careful attention to security dialogues that macOS presents."
 Roger Fingas
Roger Fingas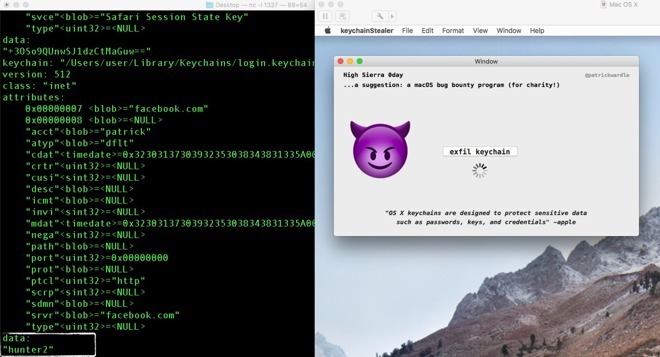










 Andrew Orr
Andrew Orr

 William Gallagher
William Gallagher
 Marko Zivkovic
Marko Zivkovic
 Amber Neely
Amber Neely
 Christine McKee
Christine McKee
 Malcolm Owen
Malcolm Owen
 Mike Wuerthele and Malcolm Owen
Mike Wuerthele and Malcolm Owen







